In an ever-evolving digital landscape, the necessity for robust security mechanisms has become paramount. Encryption serves as the cornerstone of data protection, safeguarding sensitive information from unauthorized access. However, the plethora of encryption standards available today can be a source of confusion. So, why do we require such an extensive array of encryption standards? This inquiry delves into the multifaceted reasons, emphasizing the diverse needs of various stakeholders, the implications of technological advancement, and the necessity for adaptability in security protocols.
First and foremost, one must acknowledge the heterogeneous nature of data. Information varies significantly in its sensitivity and context of use. For instance, financial data, personal health information, and governmental communications all demand varying levels of confidentiality. The Fine-grained nature of these requirements makes it imperative to develop specific encryption standards tailored for distinct scenarios. For a straightforward example, while AES (Advanced Encryption Standard) offers robust encryption suitable for a range of applications, certain highly classified government communications may necessitate even stronger algorithms, thus giving rise to specialized standards such as the Suite B Cryptography.
Moreover, the evolution of technological paradigms has prompted the development of advanced encryption methods. As our technological capabilities burgeon, so too do the threats that exploit these advancements. Cybercriminals are perpetually advancing, developing new methodologies to circumvent security measures. Consequently, encryption standards must evolve to counteract these emerging threats. This is where the principles of cryptographic agility come into play. By having a variety of encryption standards, organizations can adapt to new challenges swiftly, ensuring that security remains resilient amid an ever-shifting threat landscape.
The diverse requirements for regulatory compliance further necessitate the existence of multiple encryption standards. Regulatory frameworks such as GDPR (General Data Protection Regulation) and HIPAA (Health Insurance Portability and Accountability Act) impose stringent requirements on how organizations must handle sensitive data. Different sectors face varying legislative demands regarding data protection. For instance, the financial sector adheres to standards defined by the Payment Card Industry Data Security Standard (PCI DSS), which may differ significantly from the health sector’s own governing laws. The multitude of encryption standards serves to ensure compliance across various jurisdictions and industries, offering a mosaic of security approaches that are finely tuned to meet specific legal obligations.
Considering interoperability is also crucial in the discussion of encryption standards. Businesses often operate in multi-vendor environments; different entities may utilize different cryptographic solutions. A uniform approach would be inefficient and could potentially introduce vulnerabilities during data exchange. Encryption standards are designed with interoperability in mind. For example, the use of the RSA algorithm in conjunction with secure protocols such as HTTPS enables disparate systems to communicate securely while maintaining data integrity. This necessitates the standardization of encryption methodologies across platforms to foster functional collaboration without jeopardizing security.
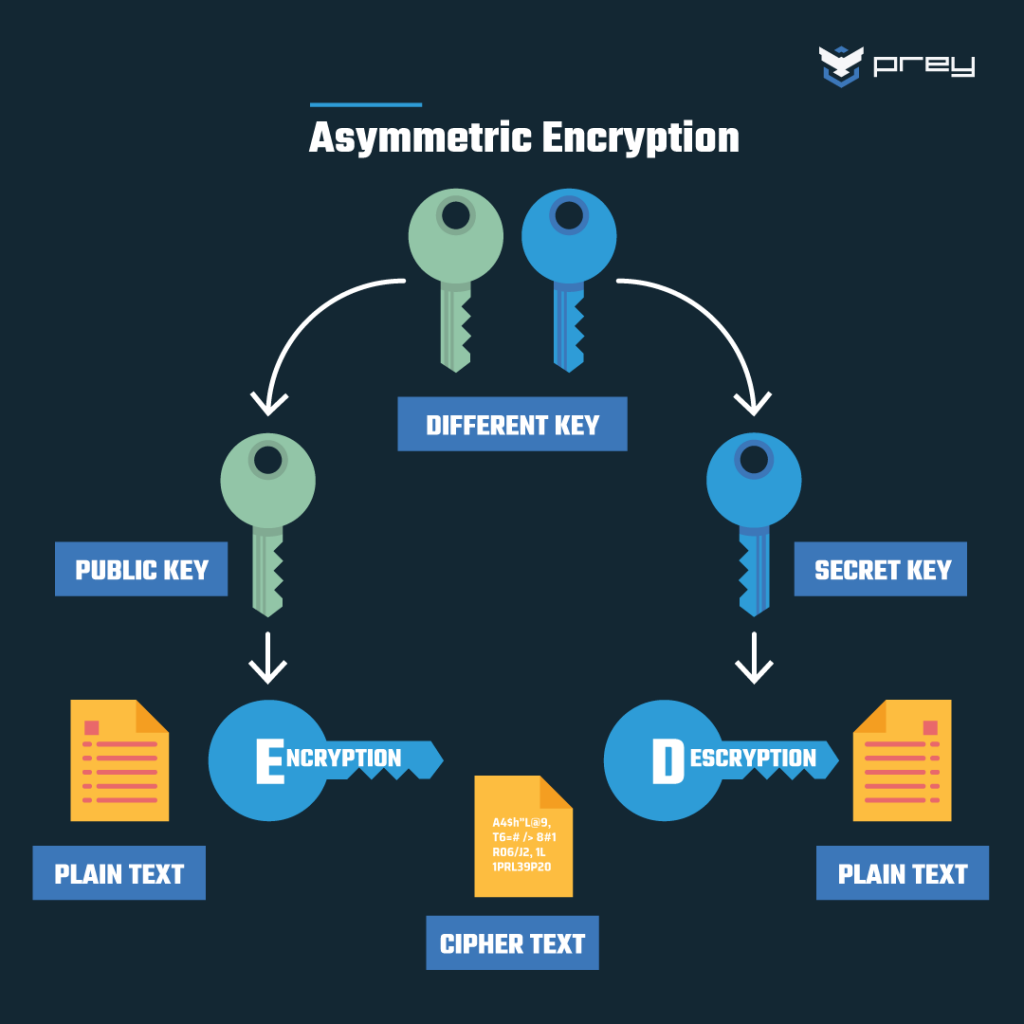
A vital aspect of cryptographic methods lies in their performance trade-offs. Various encryption techniques offer different balances of speed, efficiency, and security. For instance, symmetric encryption tends to be faster than asymmetric encryption but often requires secure key distribution. Meanwhile, asymmetric methods, while slower, provide greater convenience for key management, making them more suitable for specific applications like digital signatures and secure email communications. This variation is critical in real-world implementations; organizations may opt for a hybrid approach that synergistically integrates several encryption standards. Hence, the diverse ecosystem of encryption protocols allows organizations to tailor their security strategies based on operational requirements and constraints.
Furthermore, the principles of quantum computing are ushering in a new paradigm of cryptography. Traditional encryption methods, such as RSA and ECC (Elliptic Curve Cryptography), may face obsolescence with the impending advent of quantum computing capabilities, which threaten the foundational mathematics of these algorithms. To counter this vulnerability, the field of post-quantum cryptography is gaining traction. The development of new encryption standards resilient to quantum attacks underlines the urgency to adapt and innovate within cryptographic practices. This proactive approach serves to bolster security in a landscape that continues to evolve at an unprecedented rate.
In addition to technological and regulatory considerations, the notion of user trust plays a significant role in the proliferation of encryption standards. End users must feel assured that their sensitive data is secure. Various industries, particularly those that handle vast amounts of personal information, must prioritize transparency and security. The existence of bespoke encryption standards allows organizations to showcase their commitment to protecting consumer data, engendering trust and credibility in their operations. For example, the use of end-to-end encryption in messaging applications not only protects users’ conversations from prying eyes but also reinforces users’ confidence in the integrity of the platform.
In summation, the diverse landscape of encryption standards is not merely a byproduct of technological complexity, but rather a necessity borne out of multifarious data handling requirements, regulatory landscapes, and performance needs. As cyber threats become increasingly sophisticated, and as data privacy regulations tighten, the variety of encryption protocols serves a crucial role in maintaining the integrity and confidentiality of information. It fosters adaptability, enables compliance, and cultivates consumer confidence, ensuring that entities can navigate the intricate web of digital security with resilience and precision. In a world that is perpetually interconnected, it is through this diversity of encryption standards that robust security can be achieved.







Leave a Comment