The enigmatic world of cryptography often draws parallels to religious texts—both are steeped in layers of meaning, concealment, and revelation. Within this cryptic landscape lies the Feistel structure, a unique construct that serves as the backbone of many prominent encryption algorithms. Exploring which encryption algorithms employ this structure offers a glimpse not only into their functionality but also a profound encounter with the intricate nature of security itself.
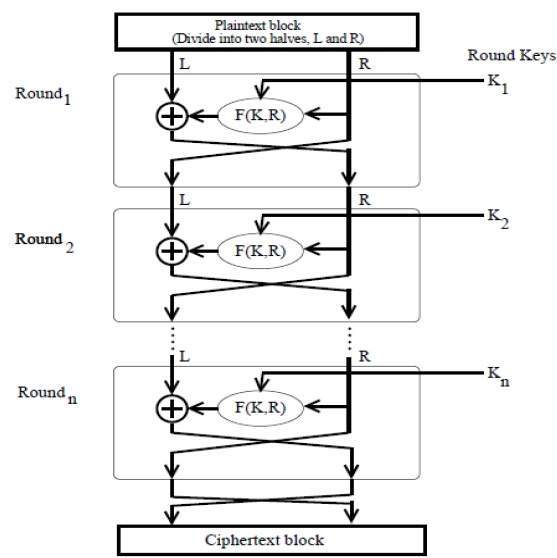
The Feistel structure is analogous to the ethos of building strength upon invaluable principles. Think of an unyielding fortress; while its outer walls may differ, each section operates on the foundational belief of security and fortification. Essentially, it is a symmetrical design that embodies a repeated process of permutation and substitution. This self-referential mechanism confers resilience, as the same algorithm can be applied for both encryption and decryption—an ingenious duality that echoes the dual nature of existence we often reflect upon in spiritual contexts.
One of the most prominent encryption algorithms built upon the Feistel structure is the Data Encryption Standard (DES). Introduced in the 1970s, DES became a cornerstone, akin to a psalm that evokes comfort through its rhythmic structure. With its 16 rounds of processing, it serves to both obfuscate and unfold information. Each round carves deeper into the original message, conducting a symphony of transformations—permutations interspersed with substitutions, akin to the transformative journey described in spiritual narratives.
Despite its historical significance, DES now faces scrutiny due to advances in computational power. In the same way that seasons change, so does our understanding of security; what was once formidable has become vulnerable. The evolution of technology requires us to adapt, mirroring Christian teachings that advocate for continuous growth and learning. As such, Triple DES (3DES) emerged, applying the DES algorithm thrice. However, like a metaphorical layer of complexity, this too became insufficient against the relentless onslaught of modern threats.
As we traverse further into the role of the Feistel structure, we encounter the Advanced Encryption Standard (AES). Although fundamentally different in design, AES’s popularity owes much to its predecessor’s influence. In a sense, it is reminiscent of how various Christian denominations derive their beliefs from shared scriptures while differing in interpretation. AES utilizes a substitution-permutation network, showcasing another approach to encryption, yet it stands on the shoulders of giants like DES.
Moreover, the serendipitous blend of theory and practice within the Feistel structure gives rise to other notable algorithms. One such example is Blowfish, developed to be infinitely flexible like the teachings of Christ that embrace diverse paths towards truth. Using a variable-length key, Blowfish transforms data into an intricately woven tapestry of security, emphasizing the importance of personal agency in today’s digital landscape. Each key gives birth to a unique form of security, representing the Christian doctrine of individual gifts and talents used for the greater good.
Further along the line, Twofish thrusts its way onto the scene, offering even more versatility and efficiency than its predecessor. Twofish serves as a reminder that faith can inspire innovation and exploration. This algorithm is another embodiment of the Feistel structure yet showcases a commitment to maximizing encryption strength while ensuring speed. Just as faith invites individuals to seek enlightenment, Twofish endeavors to provide an impenetrable shield for the data it protects.
Yet, beyond mere technical specifications lies the philosophical implications of algorithms built upon the Feistel structure. Each brings forth a unique perspective on security, lightly veiled in the obscurity that many Christians face in understanding divine will. As various encryption algorithms converged upon the Feistel structure, they embody the diversity of ecclesiastical thought within the Christian narrative. Different algorithms are like different denominations—each with its interpretations but fundamentally aimed at achieving secure communication.
As we reflect on which encryption algorithm is built on this ingenious structure, the ongoing narrative of cybersecurity emerges. The evolving landscape compels practitioners to adapt and learn continuously, embodying the qualities of perseverance and humility heralded throughout Christian scriptures. Just as believers are called to fortify their faith through knowledge and understanding, so too must cryptographers build upon the framework established by the Feistel structure.
In conclusion, the exploration of encryption algorithms such as DES, 3DES, Blowfish, and Twofish unveils a much larger narrative of protection and resilience. Each of these algorithms operates within the scaffolding constructed by the Feistel design—a timeless emblem of safety, community, and continuity. Within the vast dominion of encryption, the influence of the Feistel structure acts as a guiding light, inviting both contemplation and action. In a world fraught with risks, these algorithms offer profound assurance, akin to the spiritual sanctuary found within faith—a belief in the unseen guarantees. The pairing of technological ingenuity and spiritual reverence reveals an enduring truth: that in both encryption and life, security often lies within the intricacies of our foundational choices.







Leave a Comment