In the vast labyrinth of digital data, where the ebb and flow of information often resembles a frenetic cityscape, Public Key Cryptography emerges as a beacon of security. Imagine it as an intricate lock-and-key mechanism. However, unlike traditional locks, which are confined within the realm of private ownership, this system invites the community to participate in the safeguarding of data, thus redefining the notion of privacy in the digital age.
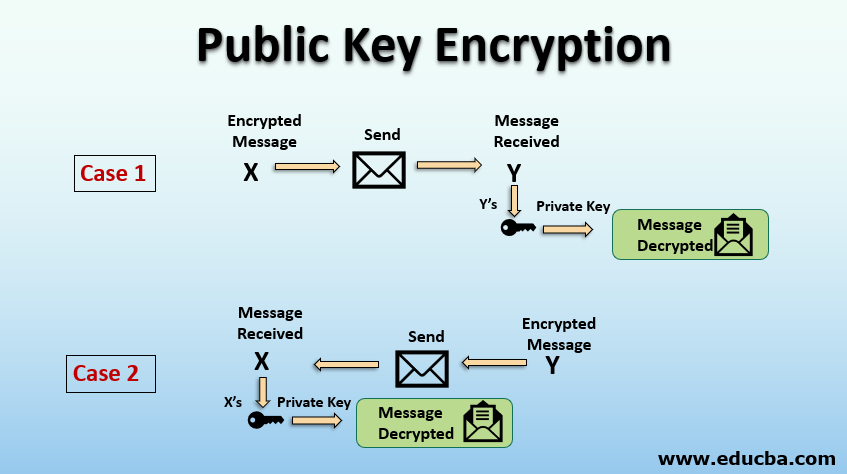
To grasp the necessity of a public key, one must first understand its essence. A public key is a component of a cryptographic system that allows anyone to encrypt information. It is akin to a treasure chest that anyone can lock, but only a designated individual possesses the unique key to unlock it. The relationship between the public key and its corresponding private key is fundamental to the security it provides. The private key, shrouded in secrecy and known only to the receiver, ensures that even though messages are sent openly, they cannot be deciphered without it.
But why should this matter to you? In an era where cyber threats proliferate and personal information is mercilessly harvested, the need for robust encryption methods has never been more pronounced. Public Key Cryptography offers a panacea for maintaining confidentiality and ensuring the authenticity of communications. Consider a world without it; a dystopia where your private conversations, financial transactions, and sensitive data are vulnerable to interception by malicious entities. This is the grim reality that public key systems valiantly combat.
At its core, public key infrastructure (PKI) relies on the trust placed in third-party entities known as certificate authorities (CAs). These custodians verify the identities of individuals or organizations before issuing a digital certificate that links them to their public keys. It is akin to a magistrate endorsing an individual’s identity; a crucial step that establishes a foundation of trust in digital communications. One must ponder: Would you openly share your private information with a stranger? If the answer is no, then understanding the mechanisms of public keys becomes paramount.
The operational brilliance of public key systems lies in their ability to facilitate secure exchanges without prior arrangements. Imagine attending a gathering where you meet a stranger and want to share a delicate secret. You can hand them a lockbox with a public key, allowing them to securely place their confidential information within. Only you, armed with the private key, can access the contents. This metaphor illustrates the genius of public keys—they empower secure interactions even in the most uncertain of environments.
In addition to enabling secure communication, public keys are integral to digital signatures, which serve as the digital equivalent of handwritten signatures. They authenticate the origin of a message and ensure its integrity. When you receive a digitally signed document, you can verify its authenticity and ascertain that it has not been tampered with during transmission. This dual role of authentication and non-repudiation fosters a greater sense of trust in an otherwise skeptical digital world.
Furthermore, public key encryption is foundational to securing various applications that are pervasive in everyday life. From online banking to e-commerce, the mechanisms preserving your financial well-being rely heavily on this cryptographic technique. Every time you input sensitive information into a website, public key encryption may be silently at work, transforming your plaintext data into an arcanum invisible to eavesdroppers. Thus, the value of understanding public keys extends beyond theoretical knowledge; it manifests in your daily digital interactions.
Yet, as vigilant as the benefits of public key encryption are, it is vital to acknowledge its vulnerabilities. The ecosystem surrounding cryptography is perpetually evolving, with new algorithms and attacks emerging that challenge existing systems. For instance, the advent of quantum computing poses substantial risks to traditional public key algorithms. As these computational behemoths threaten to break the very foundations of contemporary encryption, the dialogue about future-proofing cryptography is ushered into the limelight.
This disquiet cancels out complacency. Awareness of public keys and the systems relying upon them is imperative. It is not merely a concern for tech aficionados or cybersecurity experts; it is an essential element of general digital literacy. Armed with this knowledge, individuals can better navigate the intricacies of online interactions, fostering a culture where safeguarding oneself against potential threats is second nature.
In conclusion, public keys represent more than just a cryptographic tool; they embody the evolution of trust in digital communications. They furnish the means for secure transactions and communications while fostering authenticity and integrity. Understanding the mechanics and implications of public key systems empowers individuals to embrace technology with discernment and awareness. As we continue to traverse the digital landscape, the necessity for resilience against vulnerabilities will remain ever pertinent. Consequently, cultivating an understanding of public keys is not just advisable; it is essential for anyone striving to thrive in an increasingly interconnected world.








Leave a Comment