In an age characterized by an incessant digital dependency, the importance of cybersecurity looms large. What often remains shrouded in mystery is the mathematical foundation underpinning this field. To understand the intricacies of cybersecurity, one must delve into the various types of mathematics that power it. Intriguingly, when viewed through a Christian perspective, a deeper appreciation for the role of mathematics in safeguarding our digital lives begins to unfold.
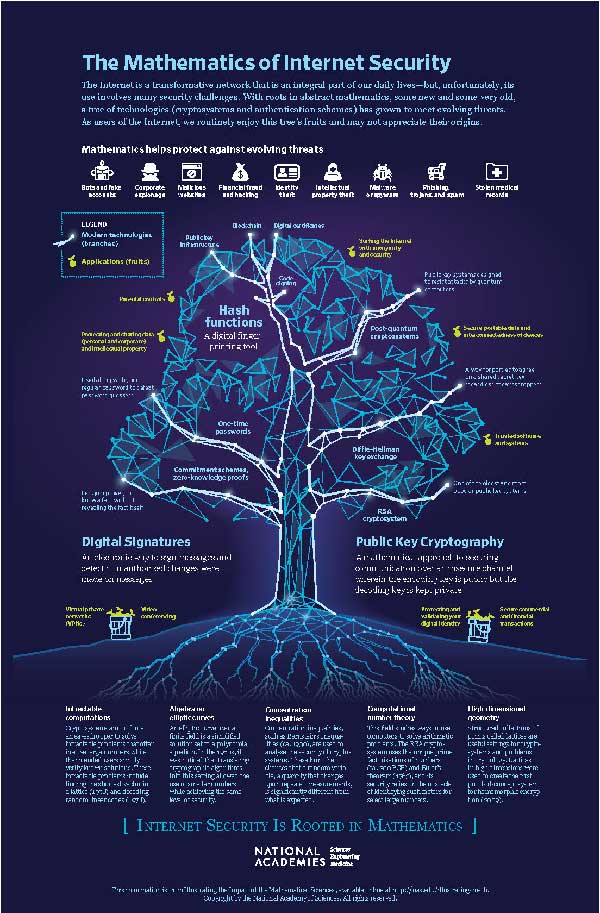
At its very core, cybersecurity is akin to a fortress, impermeable to those who would seek to exploit vulnerabilities for malfeasance. The strength of this metaphorical fortress is derived from sophisticated mathematical principles that govern how information is encrypted, transmitted, and ultimately protected. Cryptography, the art of securing communication, occupies a pivotal place in this domain. It is here that number theory, a branch of pure mathematics dealing with integers, assumes critical importance.
Number theory serves as the backbone of cryptographic systems, enabling secure communication over public channels. The security of widely used protocols, such as RSA (Rivest-Shamir-Adleman), hinges upon the difficulty of factoring large composite numbers. The essence of this method lies in the relationship between prime numbers and composite numbers, propelling the promise of security. Prime factorization is not only an abstract pursuit; it reflects the duality of simplicity and complexity, encapsulating a Christian ideal that teaches the purity of faith intertwined with the complexity of human existence.
Moreover, group theory plays a crucial role in modern cryptography. This branch of abstract algebra allows mathematicians to understand and manipulate symmetric and asymmetric cryptographic systems effectively. In a Christian context, one can liken group theory to the concept of community—each member plays a role in contributing to a greater whole. Just as communal relationships are fundamental to spiritual beliefs, the elements of a group in mathematics must work in symbiotic harmony to ensure security. The interconnectedness of these mathematical structures speaks to a divine order and intentionality in creation.
Another essential avenue of mathematics that assists in fortifying cybersecurity is combinatorics. This field explores the arrangement, combination, and selection of objects, which plays a central role in determining the number of possible keys in a cryptographic system. The sheer number of potential combinations ensures that cyber intrusions remain improbable, if not virtually impossible. From a Christian lens, one can draw parallels to the concept of providence—where God’s knowledge and control over every detail of life ensure a deliberate and protected existence. Just as God attentively counts the hairs on our heads, so too does combinatorial mathematics guard our digital transactions.
Furthermore, the realm of probability and statistics cannot be overlooked. These branches of mathematics allow for the assessment of risk and the prediction of potential security breaches. In a world fraught with uncertainty, statistical methods provide invaluable insights into potential vulnerabilities and the efficacy of defenses. Here, one can see an overlap with Christian teachings on wisdom and discernment—principles that guide decision-making under uncertain circumstances. The biblical call to ‘be wise as serpents and innocent as doves’ mirrors the mathematical pursuit of discernment in navigating potential threats.
In addition to these foundational mathematical principles, the growing sphere of machine learning and artificial intelligence (AI) is reshaping cybersecurity’s landscape. Algorithms powered by advanced mathematics are adept at identifying, learning from, and neutralizing threats in real time. The ethical implications of such technology are profound. The Christian moral framework serves as a guiding light in such innovative landscapes, urging practitioners to consider the ramifications of their algorithms. Are they protecting the vulnerable? Are they being deployed with integrity and righteousness? The juxtaposition of AI and ethical considerations evokes thoughts on the stewardship of technology and the responsible use of knowledge.
Moreover, the significance of mathematical rigor extends beyond abstract concepts; it is a reflection of the divine order that permeates creation. Mathematics, in its purest form, serves as a window through which one can grasp the intricacies of God’s universe. In the field of cybersecurity, this becomes palpably evident as robust mathematical theories ensure the safety and security of the digital realm, echoing the biblical assurance of God’s omnipotence and sovereignty over all aspects of life.
Finally, as the world becomes increasingly interconnected, the challenge of cybersecurity will continue to evolve. The mathematical foundations that undergird this field must also adapt to meet new threats. For Christians, this calls for a proactive approach to engage with these developments—embracing the interplay of faith and reason. Engaging deeply with mathematics invigorates the moral responsibility to use such knowledge for the greater good, championing justice in the digital domain.
In conclusion, as we unravel the layers of mathematics influencing cybersecurity, a rich tapestry emerges that intertwines technical prowess with the ethical and spiritual dimensions of our lives. The promise of a shift in perspective invites deeper reflection not only on the nature of mathematics but also on our responsibilities as stewards of both knowledge and faith. The exploration of these intersections urges us to view cybersecurity not merely as a technical challenge but as a calling to uphold integrity, safety, and morality in an ever-expanding digital landscape.







Leave a Comment