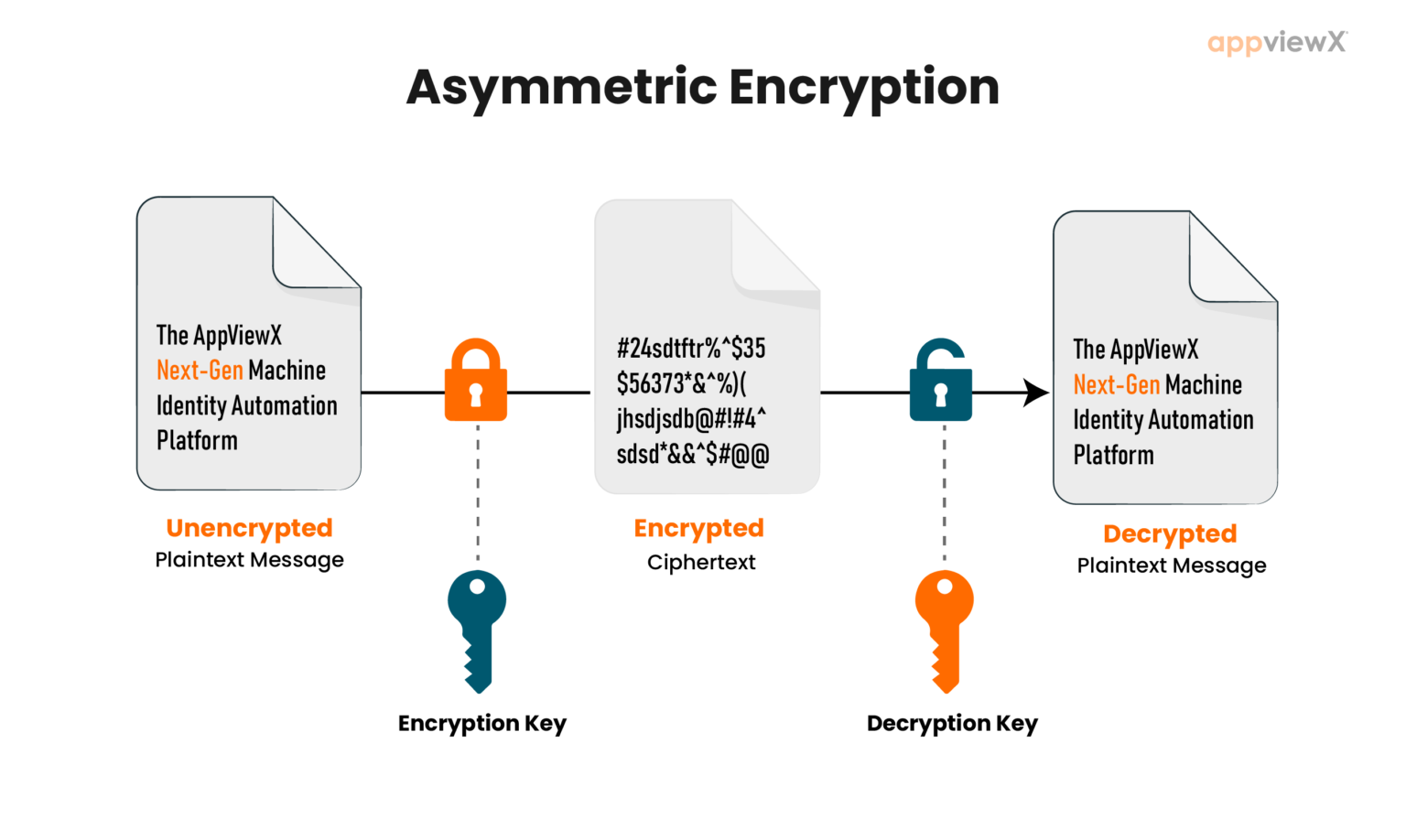
In the landscape of cryptography, asymmetric encryption stands as a formidable colossus—an impenetrable bastion that safeguards digital interactions with an adeptness that belies its complexity. Unlike its symmetric counterpart which employs a singular key for both encryption and decryption, asymmetric encryption deftly wields two distinct keys: a public key, accessible to anyone, and a private key, which remains clandestine, known only to the owner. This duality of keys not only underpins its security but also carves a distinct niche within the realm of data protection.
The allure of asymmetric encryption can be likened to the art of a masterful puppeteer. The puppeteer manipulates an intricate web of strings, controlling a symphony of movement that, while visible, remains capriciously beyond the grasp of the audience. Similarly, the public key orchestrates the encryption while maintaining the sovereignty of the private key, ensuring that only the intended recipient of the message can unveil its contents. This intricate dance of keys invokes not merely security but also a trust paradigm in digital interactions—one that is increasingly paramount in today’s interconnected world.
Democratization of Cryptography
Asymmetric encryption heralds a new dawn of accessibility. No longer does one need to navigate the convoluted alleys of key exchange protocols inherent in symmetric systems. The public key is disseminated freely—a veritable open door through which anyone may send secured messages. This democratization serves as an incubator for innovation, enabling anyone with access to the internet to participate in cryptographically secure communication. Akin to distributing a lock to every member of a community while retaining the sole key to one’s own abode, asymmetric encryption allows the efficacious sharing of information with minimal fear of interception.
Impeccable Security Mechanism
The enigmatic foundation of asymmetric encryption lies in the mathematical prowess that drives its security. The algorithms, often based on formidable number theory concepts like large prime factorization or elliptic curves, create complexities that fortify security. The probability of deriving the private key from the public key is as seemingly improbable as decoding the genetic makeup of a diamond. It is this unyielding strength against brute force attacks that empowers its usage in high-stakes environments, including financial transactions and confidential governmental communications.
The robustness of asymmetric encryption is further amplified by the phenomenon of key length. As our computational capabilities burgeon, so does the breadth of potential cipher keys. Cipher lengths, which often span several hundred to thousands of bits, create an impenetrable barrier that exponentially increases the time and resources required to breach encryption. Thus, as computational speeds accelerate, so too does the evolution of encryption standards, perpetuating a cat-and-mouse dynamic in cryptographic defenses.
Non-repudiation: Laying Claim to Identity
In our modern age, where identity is but an ephemeral concept often manipulated by the faceless eternity of the cyberspace, asymmetric encryption introduces a robust mechanism of authentication and non-repudiation. The signature that is appended to an electronically transmitted message with a private key serves not merely as a marker but as an irrevocable claim of authorship. Just as an artist cannot disavow their creation, a sender cannot deny the legitimacy of their digital fingerprint. This aspect is invaluable in contractual agreements, where the veracity of consent holds paramount significance. The assurance that one party cannot later dispute their commitment enhances the trust inherent in digital transactions.
Facilitating Digital Signatures
The potency of asymmetric encryption further materializes in the field of digital signatures. In its essence, a digital signature not only authenticates but also assures message integrity. When a message is signed with a private key, any alteration disavows the signature’s authenticity, alerting the recipient to potential tampering. In this context, the digital signature becomes more than mere verification; it transforms into a bulwark against malfeasance. Think of it as a wax seal on a scroll, signifying authenticity and protection—a gesture that has endured since the days of antiquity.
Challenges and Future Prospects
However, not all that shines is gold. Asymmetric encryption, while powerful, is not devoid of limitations. The computational overhead associated with encryption and decryption processes is markedly higher than symmetric methods, where the single key algorithm tends to be less resource-intensive. Furthermore, as cryptographic threats evolve, including the specter of quantum computing, the framework of asymmetric encryption faces potential exposure. Quantum algorithms could one day eclipse existing encryption methodologies, necessitating advancements in post-quantum cryptography—an area currently under extensive research.
Nonetheless, the landscape remains vibrant with solutions, including hybrid models that meld asymmetric and symmetric encryption’s strengths, striking a balance between security and efficiency. The promise of quantum-resistant algorithms brings hope for resilience against future threats, solidifying asymmetric encryption’s place in the pantheon of cryptographic mechanisms.
The uniqueness of asymmetric encryption lies not solely in its technical sophistication but in the value it provides—a safeguard of identity, an assurance of integrity, and a facilitator of trust. As we traverse an increasingly digital future, the power of asymmetric encryption endures, offering a beacon of security in an ever-evolving landscape fraught with uncertainty.







Leave a Comment