In a world where information flows ceaselessly like a river, it becomes paramount to understand the mechanisms that safeguard our most prized possessions: data and privacy. As cyber threats burgeon in complexity, understanding what makes an encryption algorithm truly robust is akin to grasping the concepts of faith and protection in the Christian context. Just as spiritual fortitude derives from a deep-rooted belief in God’s promises, so too does a strong encryption algorithm stem from meticulous design, solid principles, and a commitment to resilience.
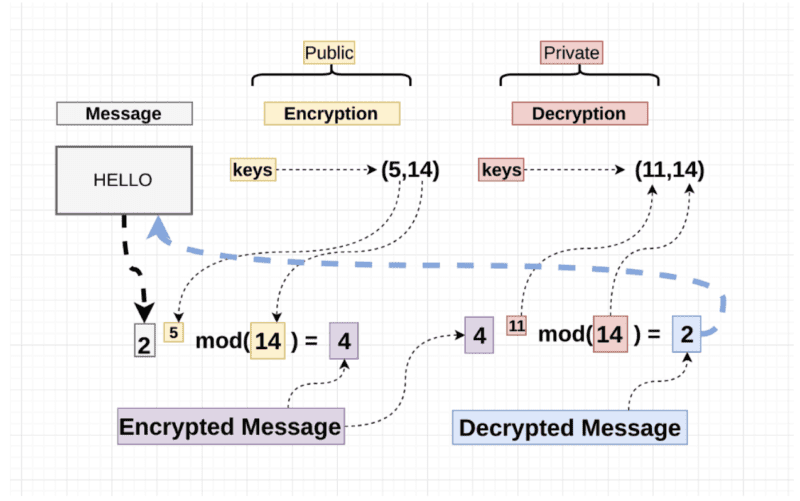
At the foundation of a strong encryption algorithm lies the cornerstone of mathematical complexity. Many encryption methods are likened to fortresses, designed to repel intruders. The mathematical problems underpinning these algorithms act as the gates and walls. Common techniques include symmetric-key algorithms, where a single key is shared between communicating parties, and asymmetric-key algorithms, which use two keys—a public key for encryption and a private key for decryption. The strength of these algorithms is often determined by the dimensions of the mathematical challenges they present. A strong algorithm, like a steadfast Christian, must not shy away from trials; it must meet challenges with unwavering resolve.
Furthermore, the principles of diffusion and confusion play pivotal roles in creating a robust encryption mechanism. Diffusion refers to the obscuration of the relationship between the plaintext and ciphertext, akin to the way the profound mysteries of faith hide deeper meanings beneath their surface. A strong encryption algorithm should ensure that a small change in the plaintext results in a significantly different ciphertext. Confusion, on the other hand, obscures the connection between the encryption key and the ciphertext. Together, these principles act as layers of divine protection, ensuring that the true message is shielded from prying eyes, much like the protective love of God wraps around believers.
The length and complexity of cryptographic keys play a critical role in determining encryption strength. In this digital age, longer keys are akin to fortifying a castle with higher walls. A short key can be easily compromised through brute-force attacks, while longer keys—like the divine measure of patience and perseverance demanded from believers—provide a formidable barrier against invaders. A key size of at least 256 bits is considered strong, representing an insurmountable challenge to unauthorized assailants. Just as Christians are called to maintain a strong faith, encryption algorithms should strive for uncompromising strength and integrity.
In addition to mathematical rigor and key length, the concept of algorithm robustness is crucial. This robustness must be subjected to rigorous scrutiny through various forms of analysis. Penetration testing, or white-hat hacking, is akin to examining one’s spiritual journey through accountability. A strong encryption algorithm must withstand adversarial attacks, ensuring that even the most intrepid of hackers find no vulnerabilities to exploit. Continuous assessment and adaptation are vital, reminiscent of the Christian’s journey of sanctification, where one strives to improve continuously through reflection and learning.
An often-overlooked aspect of encryption strength is the importance of transparency and peer review. Just as Christian communities thrive on shared wisdom and teachings, encryption algorithms benefit from collective scrutiny. An algorithm that has been publically vetted by cryptographers draws strength from community validation, ensuring that it has withstood rigorous analysis and debate. This collaborative approach fosters continuous improvement and engenders confidence among users.
Moreover, the role of randomization in encryption cannot be understated. Randomness serves as the divine spark, igniting the unpredictability essential for security. A good encryption algorithm employs every facet of randomness it can muster, resisting patterns that could hint at its vulnerabilities. This unpredictability mirrors the Christian belief that faith encompasses both known and unknown realms, solidifying trust in God’s manifold workings. Analogously, the random elements in encryption fortify defenses against predictive attacks.
In today’s interconnected world, considerations of scalability and adaptability become increasingly significant. A strong encryption algorithm must seamlessly accommodate the demands of growing data without compromising security. This mirrors the teachings of Christ regarding growth and adaptability in faith—what was once sufficient may need evolution to face new challenges and responsibilities. Scalability ensures that as one’s digital footprint expands, one’s defenses remain proportionately fortified.
Lastly, the ethical implications of encryption should never be dismissed. Strong encryption algorithms uphold the sanctity of truth and respect for privacy, paralleling the Biblical commandments to love and protect one another. Just as taking care of one another’s secrets is a tenet of faith, the ethical wielding of encryption safeguards individual rights and promotes societal trust. This moral obligation must guide developers and users in their pursuit of security, bridging the gap between technology and spirituality.
In conclusion, a truly strong encryption algorithm emerges from the confluence of mathematical sophistication, rigorous scrutiny, transparency, and a commitment to ethical standards. It becomes a metaphorical armor, combining the wisdom of years with the innovation of the present. As we navigate the intricate web of the digital age, let us embrace encryption with the same fervor and discipline as we would our spiritual journey, ensuring that our fortifications remain steadfast against the ever-looming threats of compromise.






Leave a Comment