In the contemporary age of information technology, the relevance of encryption cannot be overstated. Cryptography serves as the bedrock for securing sensitive information, and at its core lies the concept of a cryptographic key. This article explicates what constitutes a secure key and the consideration that goes into determining its appropriate length.
Before delving into the intricacies of key security, it is essential to comprehend the role of a cryptographic key. In simple terms, a key acts as a unique identifier that secures data by either encrypting or decrypting plaintext. The strength of this key directly correlates to the level of security it provides. A key that is susceptible to exposure can severely undermine the trust in the entire encryption system.
One of the foremost attributes that contribute to a key’s security is its entropy. Entropy, in the context of cryptography, measures the unpredictability or randomness of the key. A secure key must possess a high level of entropy to thwart adversaries attempting to employ brute force attacks. Brute force attacks involve systematically checking all possible keys until the correct one is found. For instance, a key with low entropy might follow predictable patterns or sequences, making it a prime target for attackers. Thus, randomness is a premium quality in key generation.
Moving beyond mere randomness, key length is another pivotal aspect that influences security. As computational capabilities evolve, so too do the methods employed by potential attackers. Consequently, what was once considered a robust key length may no longer suffice against modern attacks. Encryption algorithms like AES (Advanced Encryption Standard) embrace manifold key lengths, often ranging from 128 bits to 256 bits. In well-designed cryptographic systems, each additional bit of key length exponentially magnifies the number of possible combinations, thereby enhancing security. Empirical evidence suggests that a key length of at least 256 bits is recommended for applications requiring long-term confidentiality.
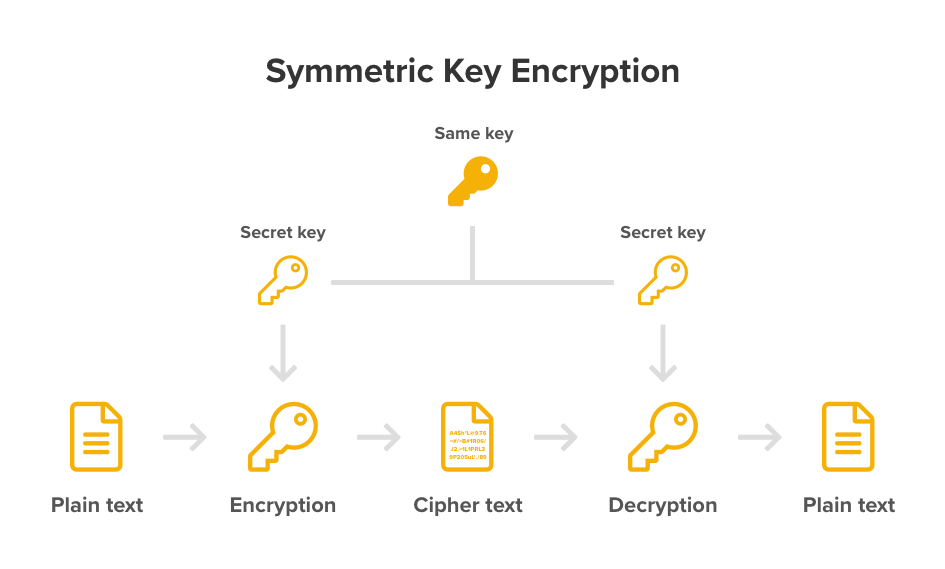
The choice of encryption algorithms also plays an indispensable role in securing keys. Different algorithms possess varied strengths, weaknesses, and operational contexts. For instance, symmetric key algorithms, which utilize a single key for both encryption and decryption, require that both parties securely share this key. In contrast, asymmetric key algorithms employ a pair of keys — a public key for encryption and a private key for decryption. Each approach has implications on key security and management. Symmetric algorithms, while faster, necessitate robust key exchange mechanisms, while asymmetric methods, despite being computationally intensive, mitigate key distribution problems.
Furthermore, the method of key management must be scrutinized to ensure the integrity of security practices. Key management encompasses the generation, distribution, storage, and destruction of cryptographic keys. If any of these processes are flawed, even the most robust key could become compromised. For example, storing keys on a local device without encryption or sufficient access controls can lead to unauthorized access. Therefore, implementing industry-standard protocols for key lifecycle management is imperative in maintaining a secure environment.
Key Rotation and Expiry: Another aspect worth mentioning is key rotation and expiry. Over time, continuous usage of the same key can make it susceptible to exposure or compromise. Therefore, implementing a policy for periodic key rotation serves as a proactive measure against evolving threats. A typical rotation cycle varies based on the sensitivity of the data being protected, but best practices suggest frequent changes to keep potential vulnerabilities at bay.
Moreover, encapsulating keys within hardware security modules (HSMs) or utilizing hardware-based encryption can bolster key security. HSMs are physical devices that manage and safeguard digital keys, providing an extra layer of security—physically and logically. Leveraging such dedicated resources significantly diminishes the probability of key compromise via software vulnerabilities.
Final Thoughts: The question of what makes a key secure is multifaceted, conflating various elements such as randomness, key length, algorithm choice, management practices, and environmental controls. As threats evolve, so too must the strategies for ensuring cryptographic key security. Organizations and individuals alike should remain vigilant in their efforts to adapt to advancements in both technology and adversarial techniques skirting the edges of legality.
In conclusion, setting a definitive standard for key lengths should not merely reflect historical practices but should be influenced by a contemporary understanding of computational limitations and security imperatives. While 128 bits may still hold relevance for certain scenarios, transitioning towards longer keys, such as 256 bits, will offer substantial assurance against future threats. With the proliferation of data breaches and cyberattacks, a robust cryptographic architecture is not merely desirable; it is essential.








Leave a Comment