In the vast sea of the internet, where countless ships navigate daily, security serves as the lighthouse guiding the way. Just as sailors must trust their navigation systems to prevent perilous encounters with hidden rocks, developers must ensure the integrity of their mobile and web applications. One of the most critical navigational tools in this realm is SSL pinning. It acts as an anchoring mechanism, ensuring that the connection between an app and its server remains steadfast and secure. This article delves into the concept of SSL pinning and elucidates why it is indispensable for modern applications.
1. Understanding the Basics of SSL Pinning
To truly appreciate SSL pinning, one must first comprehend Secure Sockets Layer (SSL) and its successor, Transport Layer Security (TLS). These are protocols designed to establish a secure communication channel over an insecure network. In essence, they serve to encrypt data transmitted between a client and a server, safeguarding it from prying eyes.
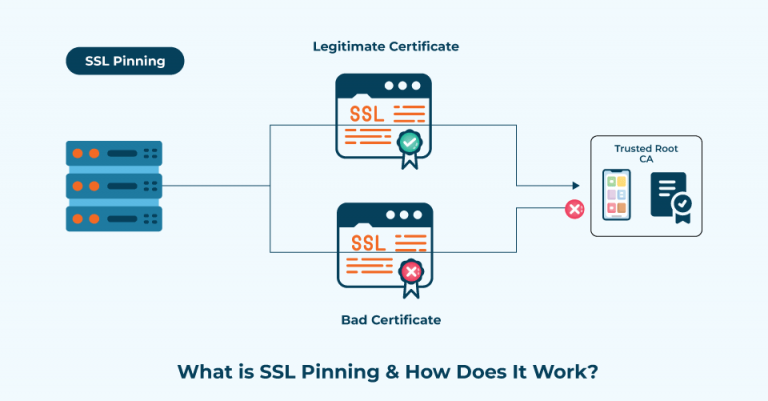
However, SSL alone does not provide complete security. A fundamental weakness arises when attackers can imitate legitimate servers, redirecting innocent users to malicious entities. This is where SSL pinning emerges as a defensive bastion. By hardcoding the expected SSL certificates or public keys within the application, developers effectively tell the app, “Only trust these specific certificates.” Should an illegitimate certificate appear, the connection is severed, and the app protects user data from potential exposure.
2. The Types of SSL Pinning
In the domain of SSL pinning, two primary methodologies exist: public key pinning and certificate pinning. Each method possesses unique advantages, akin to choosing between two different blades for a sword, each serving a distinct purpose.
Public Key Pinning: This technique involves storing the hash of a public key rather than the entire certificate. By doing so, developers provide greater flexibility in case the server’s certificate is renewed or changed. The app continues to accept connections with the same public key, effectively reducing maintenance efforts while maintaining robust security.
Certificate Pinning: This method requires embedding the actual SSL certificate into the app. While it offers an additional layer of security, it can create challenges when certificates need to be updated. If proper foresight isn’t exercised, developers might inadvertently render the app inoperable if the pinned certificate expires or becomes invalid.
3. The Importance of SSL Pinning
In an era characterized by escalating cybersecurity threats, the importance of SSL pinning cannot be overstated. The ramifications of failing to implement such measures can be severe, equating to a ship navigating without a rudder—destined for turmoil. Here are several reasons highlighting its critical nature:
Mitigation of Man-in-the-Middle Attacks: This pernicious attack involves an intermediary intercepting communication between the user and the server. By deploying SSL pinning, developers create a formidable barrier, rendering such attacks significantly more challenging to execute.
User Confidence: In the eyes of the users, trust is paramount. An application that prioritizes security through SSL pinning showcases its commitment to safeguarding user data. This assurance can bolster user loyalty and encourage positive word-of-mouth, akin to a fortress that stands resilient against external threats.
Compliance with Regulations: In many industries, regulatory frameworks mandate strict adherence to data protection policies. Incorporating SSL pinning can help organizations fulfill these obligations, thus avoiding potential fines and reputational damage.
4. Implementation Strategies
Embedding SSL pinning within an application involves numerous strategic considerations. This endeavor requires not only technical prowess but also foresight and planning:
Employ Robust Development Frameworks: Many modern development frameworks offer built-in SSL pinning capabilities. Utilizing these frameworks can simplify implementation while ensuring adherence to best practices.
Regular Updates: It is imperative to keep a vigilant eye on SSL certificates. Regularly scheduled updates and maintenance help avoid pitfalls associated with certificate expiration. Developers must establish a comprehensive update strategy comparable to routine ship inspections for navigational accuracy.
Testing and Validation: A crucial phase of implementation involves rigorous testing to guarantee that SSL pinning functions seamlessly without compromising the user experience. Simulating potential attacks through penetration testing can unearth vulnerabilities and fortify defenses.
5. Challenges and Considerations
While SSL pinning delivers notable advantages, it is not devoid of complexities. Developers face challenges akin to navigating treacherous waters:
Certificate Management: As certificates expire and need to be rotated, continuous management is necessary to ensure that applications remain functional without user disruption.
Debugging Difficulties: During the development and testing phases, SSL pinning can complicate debugging efforts. Developers may encounter hurdles when trying to identify issues due to the stringent security protocols in place.
Fallback Mechanisms: Caution must be exercised to implement fallback mechanisms that can gracefully handle certificate errors, ensuring that user experience remains intact even when security measures activate.
6. Conclusion
In the intricate world of digital interactions, where data transverses countless channels, the significance of SSL pinning is akin to securing a vital supply route during times of conflict. By implementing SSL pinning, developers not only protect sensitive user data but also forge a reputation of trust and reliability in their applications. As technology evolves and cyber threats proliferate, those who prioritize security through SSL pinning will find themselves well-equipped to sail smoothly through the turbulent waters of the digital age.








Leave a Comment