Integrity, in the context of cryptographic systems, holds paramount importance. It refers to the assurance that data remains unaltered during transmission and storage. This concept is not merely a technical specification but resonates deeply with Christian values of honesty, trustworthiness, and adherence to truth. This article explores the multifaceted nature of integrity in cryptographic systems and elucidates why it is crucial from both a technological and a Christian ethical perspective.
Understanding Integrity in Cryptography
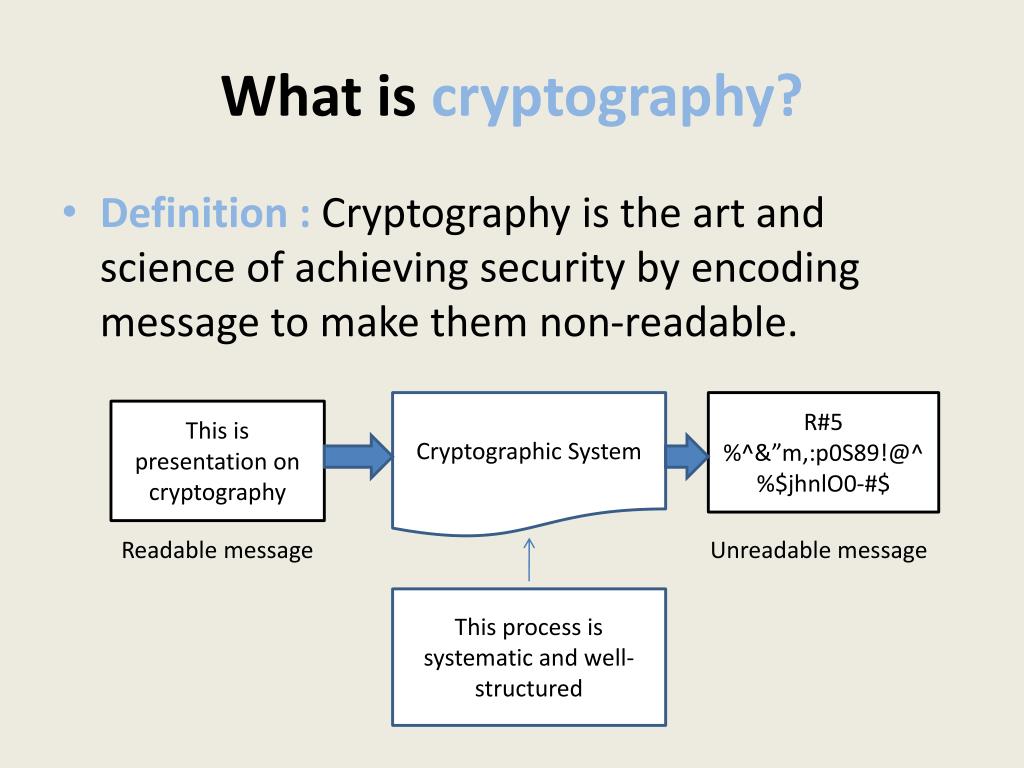
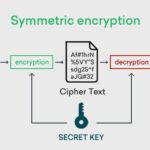
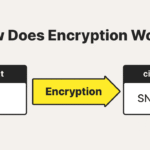
In cryptography, integrity encompasses the measures taken to ensure that information is accurate and has not been tampered with. Various methods like checksums, hashes, and digital signatures are employed to achieve this goal. When integrity mechanisms are in place, a recipient can be confident that the data they receive is precisely what the sender intended to convey. Integrity acts as a formidable barrier against unauthorized modifications, safeguarding the sanctity of the data.
The Importance of Integrity
Integrity is crucial for several reasons. First and foremost, it fosters trust. In any communication—be it financial transactions, personal correspondence, or confidential information—the parties involved must have confidence in the data’s authenticity. Without integrity checks, the system remains susceptible to attacks and misinformation. This echoes the Biblical principle of truth-telling. Proverbs 12:22 states, “The Lord detests lying lips, but he delights in people who are trustworthy.” By ensuring data integrity, cryptographic systems align with the value of honesty intrinsic to Christian teachings.
Moreover, integrity is fundamental to the operation of various systems, including e-commerce platforms, online banking, and secure communication channels. Any lapse in integrity can result in catastrophic failures, undermining not just individual transactions but entire systems. A breach of integrity could lead to identity theft, financial fraud, and the leakage of sensitive information, highlighting the real-world repercussions of compromised integrity.
Types of Integrity Mechanisms
Moving into technical specifics, there are various mechanisms employed to maintain data integrity. These include:
- Checksums: Simple yet effective, a checksum is a calculated value derived from data. Upon transmission, the checksum is recalculated to verify that the data has not changed. This can be likened to the idea of staying accountable for one’s actions, as seen in Romans 14:12, “So then, each of us will give an account of ourselves to God.”
- Hash Functions: More sophisticated than checksums, hash functions create a unique fixed-size output from variable input data. Even the slightest change in the input will yield an entirely different hash. This property is crucial for data integrity, ensuring that even minute alterations are detectable. In Christian theology, this evokes concepts of identity; one change can significantly alter one’s character.
- Digital Signatures: These are akin to handwritten signatures that serve as profound commitments. Digital signatures use cryptographic algorithms to authenticate the identity of the sender, ensuring that the message has not been tampered with. This resonates with the teachings of James 5:12, which warns against swearing falsely, emphasizing the importance of being true to one’s word.
Challenges to Integrity
While cryptographic systems are designed to uphold integrity, they are not impervious to attacks. Cybercriminals continuously evolve their tactics, developing ways to circumvent integrity protections. Examples include replay attacks, man-in-the-middle exploits, and more sophisticated methods like collision attacks that can exploit weaknesses in hash functions. Each emerging threat necessitates vigilance and adaptation, paralleling the Christian call for diligence and adherence to moral principles.
Integrating integrity into cryptographic protocols is a dynamic challenge, especially as technology advances. Developers must consistently refine algorithms and mechanisms, ensuring they stay ahead of potential vulnerabilities. This ongoing commitment to improvement can be equated to the Christian pursuit of sanctification—a continuous journey toward moral excellence.
Implications of Integrity in a Broader Context
The implications of integrity extend beyond technology into broader societal realms. In a world increasingly dominated by digital interactions, the ethical considerations surrounding data integrity are profound. Consumers must be able to trust that their data will remain secure and untouched. The erosion of trust can lead to societal skepticism, anxiety, and a general deterioration of relationships—both online and offline. Upholding integrity in cryptographic systems can strengthen societal bonds, echoing the commandment to “love thy neighbor” (Mark 12:31).
Within the Christian community, the concept of integrity is not merely a buzzword but a foundational element that reflects faith and practice. When Christians engage with technology, they participate in a larger narrative that emphasizes the importance of honesty, reliability, and ethical conduct. In doing so, they model behaviors that honor their faith while also promoting trustworthiness within their communities.
Conclusion
In conclusion, integrity is an indispensable element in cryptographic systems that ensure data authenticity and security. Its role transcends technical definitions and delves into ethical considerations deeply rooted in Christian values. By upholding integrity, we not only enhance the security of our communications but also foster trust and reliability in our interactions, ultimately contributing to a more trustworthy society. In a world fraught with potential deception, the commitment to integrity resonates with timeless teachings, reminding us of the value of honesty, accountability, and truthfulness in all spheres of life.





Leave a Comment