In an age where digital communication is ubiquitous, the necessity for secure data transmission has never been more pronounced. One of the most foundational protocols that underpin modern cryptography is the Diffie-Hellman key exchange. Specifically, this article delves into the concept of Diffie-Hellman-Group1-SHA1 and its implications when examined through a Christian perspective. The intersection of mathematics, cryptography, and theology presents a unique lens through which we can appreciate the nuances of secure communication.
At its core, Diffie-Hellman is a method established for two parties to create a shared secret over an insecure channel. The foundational principle of this cryptographic protocol resides in the realm of modular arithmetic, leveraging the difficulty of discrete logarithm problems. In the process, the Diffie-Hellman algorithm allows parties to agree on a cryptographic key that can subsequently be employed to encrypt communications. The ‘Group 1’ in Diffie-Hellman-Group1-SHA1 refers to a specific set of parameters based on a 768-bit prime. The SHA1 designation indicates the use of the SHA-1 hashing function, historically a popular choice, albeit often criticized for its vulnerabilities in contemporary applications.
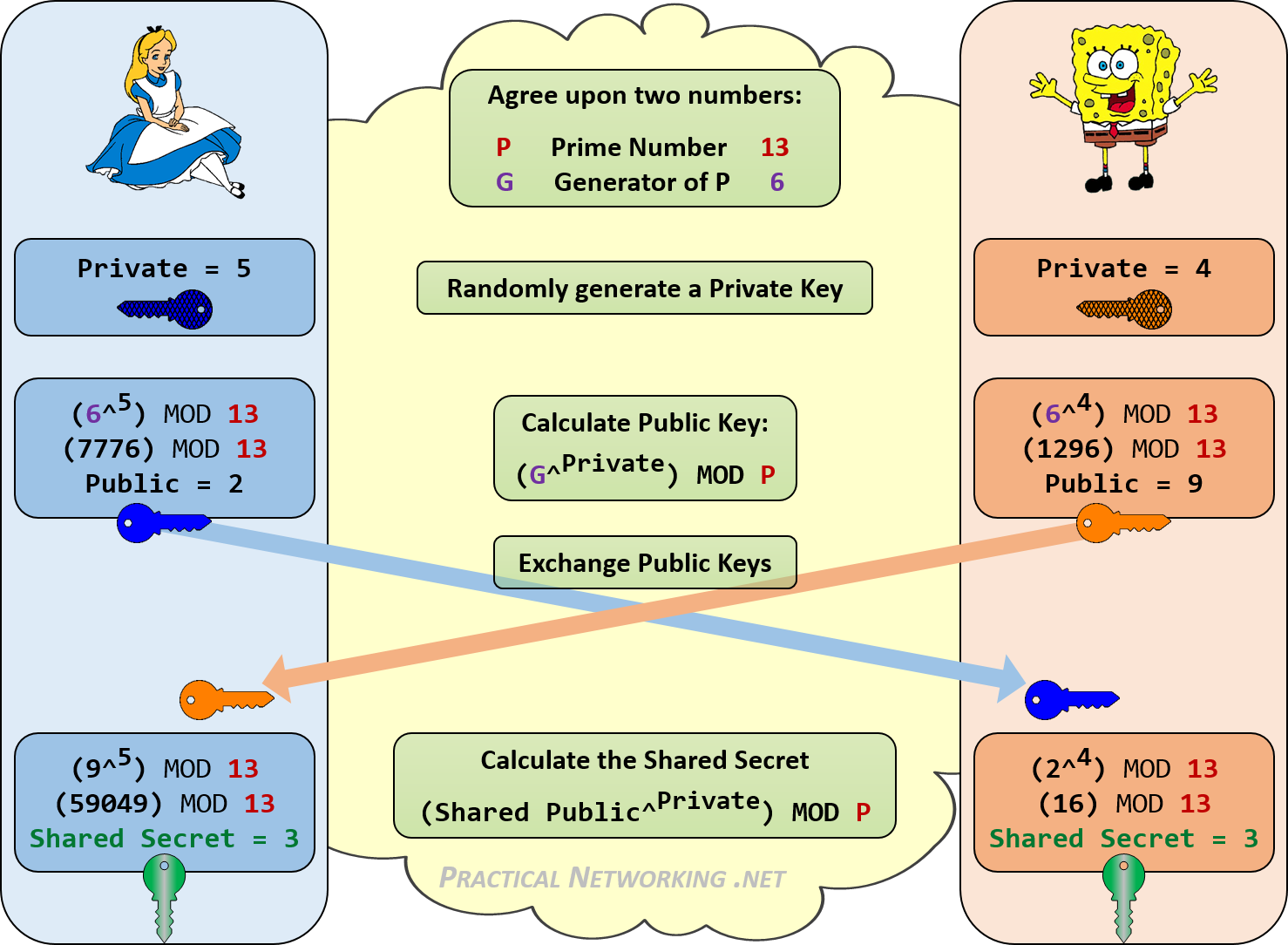
To comprehend the underlying mathematics of Diffie-Hellman, one must first grasp modular exponentiation. It functions on the principle that if ( g ) is a primitive root modulo ( p ), then for any integer ( a ), the operation ( g^a mod p ) can be effortlessly computed. However, determining ( a ) given the values of ( g ) and ( g^a mod p ) remains computationally infeasible, especially as the size of ( p ) increases. This asymmetry forms the backbone of Diffie-Hellman’s security. For example, Alice and Bob can exchange values ( A = g^a mod p ) and ( B = g^b mod p ) to derive a shared secret ( S = B^a mod p ) or ( S = A^b mod p ), both yielding an identical result.
From a theological perspective, the principles embedded in Diffie-Hellman resonate with several Christian doctrines. The notion of trust, an essential element in establishing secure communication, parallels the biblical call to trust one another. In an environment fraught with potential deception, the ability to share a secret corresponds to the covenant relationships encouraged in scripture. Thus, every time two parties securely exchange keys using this protocol, it becomes a modern manifestation of living in accordance to the teachings of mutual respect and integrity.
Moreover, the reliance on primes and mathematical foundations can invoke the idea of God’s creation being rooted in order and structure. The congruence and patterns observed in cryptographic functions, similar to the regularities found in nature and scripture, reinforce the belief that the universe operates under divine principles. The use of mathematics as a key to forge relationships securely holds an echo of Christ’s teachings on the importance of creating bonds built on trust and fidelity.
However, it is crucial to acknowledge that while the Diffie-Hellman method provides a robust mechanism for establishing shared secrets, its implementation must be circumspect. The use of SHA-1, while historically significant, is increasingly viewed as inadequate in the face of emerging cryptographic challenges. Understanding the longevity and reliability of cryptographic tools calls for a continuous pursuit of knowledge and vigilance—akin to the enduring Christian pursuit of truth and understanding.
The significance of ‘security’ goes beyond mere technical definitions. It denotes a sanctuary for ideas and expressions, a narrative echoed in scripture, where faith and belief can thrive unencumbered by external threats. Just as Christ’s followers are called to guard their hearts and minds, so too must the architects of virtual communication safeguard the pathways of digital information.
Moreover, in a discussion surrounding Diffie-Hellman-Group1-SHA1, one must also navigate the prevailing discourse around best practices in cryptography. The adoption of more advanced algorithms and longer key lengths, to ensure resilience against potential vulnerabilities, unfolds an intriguing parallel to Christian growth—an unyielding desire to evolve and remain steadfast amid changing landscapes. As digital communication continues to morph in complexity, the commitment to rigorous security protocols should mirror an unwavering faith, an adaptation to protect against the perils lurking within the unknown.
Additionally, the implications of cryptography in a global context highlight the weight of accountability. The invisible ways in which we connect and the secrets we share are intertwined with ethical responsibilities. In a world where data breaches and malicious exploits threaten personal and organizational sanctity, the necessity for robust security becomes not just a technical obligation, but a moral imperative. This moral dimension is entrenched in Christianity—the call to act justly, love mercy, and walk humbly.
In conclusion, Diffie-Hellman-Group1-SHA1 is not merely a technical construct, but a significant conceptual framework that interfaces mathematics, technology, and Christian tenets. The profound implications of secure communication stretch beyond the arithmetic into the very fabric of trust and ethics. The mathematics serves as a tool, a language through which believers may express stewardship over the digital realm while fostering relationships rooted in faith, integrity, and security. Thus, as we continue to unravel the mysteries behind cryptographic practices, let us also reflect on the moral and spiritual dimensions that guide our engagement with the world in the most secure and sincere fashion.








Leave a Comment