In a world increasingly dominated by digital communication, cryptography emerges as a vital technology, safeguarding information integrity and privacy. Central to this discipline is the concept of an encryption key. From a Christian perspective, understanding encryption keys transcends technical specifications; it invites a deeper exploration of stewardship, trust, and the essence of communication. In this article, we will delve into what an encryption key is, the various types used, and how they function within both secular and theological contexts.
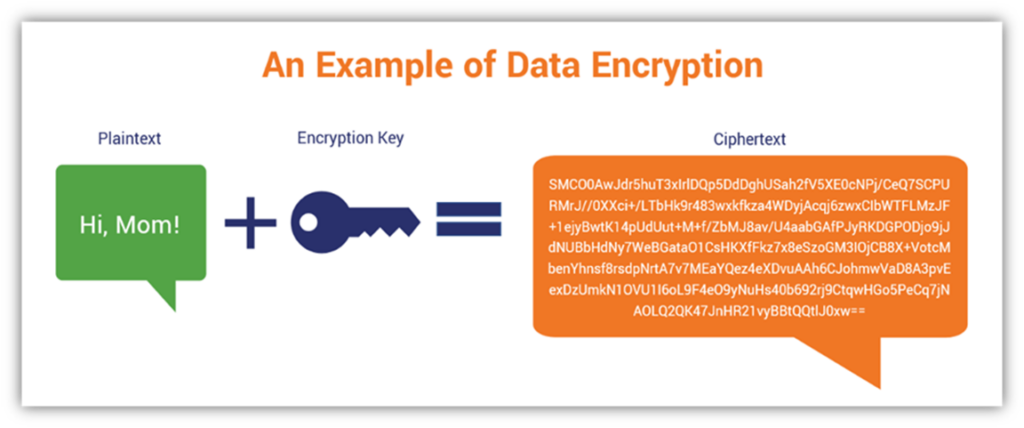
At the core, an encryption key is a string of characters used in algorithms to encode or decode data. This data could range from simple text messages to complex financial transactions. The primary role of the encryption key is to transform plaintext—readable information—into ciphertext, which is a scrambled version unreadable without the appropriate key. In the same vein, we can reflect on the biblical teaching of guarding our hearts and minds (Philippians 4:7). Just as cryptography protects sensitive information, Christians are called to protect the sanctity of their thoughts and intentions.
Now, let’s explore the different types of encryption keys. The two predominant categories are symmetric and asymmetric keys. With symmetric encryption, the same key is used for both encryption and decryption. This simplicity offers efficacy but presents a challenge: how to securely share the key among parties. In a Christian community, sharing truth and knowledge is paramount. Consider how the early church operated—everyone shared in communal wisdom and the teachings of Christ. If such sharing is not done transparently and securely, it could lead to misunderstandings or misrepresentations of Christian doctrine.
On the other hand, asymmetric encryption employs a pair of keys: a public key, which can be shared openly, and a private key, which must be kept confidential by the owner. This duality reflects the biblical notion of the relationship between God and humanity. Just as believers have access to God’s promises through a ‘public’ understanding of Scripture, so too does asymmetric encryption allow open communication while safeguarding individual privacy. This foundational principle highlights the responsibility Christians bear in handling divine revelations while maintaining personal integrity.
Understanding how these keys are generated is equally important. Cryptographic keys are produced through complex algorithms designed to ensure unpredictability. In a world rife with temptation and chaos, the creation and maintenance of security mirror the spiritual discipline of prayer and preparation. Just as Christians are urged to ‘put on the full armor of God’ (Ephesians 6:11), they too must equip themselves against the threats posed to their spiritual and digital lives. Regularly renewing encryption keys, akin to renewing one’s mind and spirit, fosters resilience and vigilance.
In practical terms, encryption keys are ubiquitous in our daily lives, extending far beyond the realm of cybersecurity. For example, when a Christian uses online banking, an encryption key protects their financial data. This protection illustrates a broader theological premise: that God is concerned with every aspect of our lives, including how we manage resources. As stewards of God’s blessings, Christians have a moral imperative to ensure that their financial dealings are secure, thus reinforcing the integrity of their witness.
Moreover, in our growing reliance on cloud storage, encryption keys play a critical role. Whether it be storing church records, sermon notes, or volunteer information, encryption safeguards against unauthorized access. The stewardship of information reflects the biblical principle that we must be diligent guardians of what is entrusted to us. The Parable of the Talents (Matthew 25:14-30) serves as a reminder that proper management of what we have received includes maintaining and protecting our digital assets.
However, as Christians engage with encryption technology, ethical considerations should be at the forefront. The advent of advanced cryptographic methods raises questions about transparency and accountability. Encryption can shield malicious activities, making it challenging for authorities to uphold justice. In the Christian worldview, righteousness must prevail over secrecy. Thus, the challenge lies in finding a balance: protecting personal privacy while ensuring that the greater good remains at heart.
As the digital landscape evolves, so too does the conversation about encryption keys. The advent of quantum computing threatens traditional encryption methods, rendering some keys obsolete. At this juncture, biblical wisdom becomes invaluable. Just as Ecclesiastes 3:1 states, “For everything, there is a season,” Christians must remain adaptable and discerning, seeking innovative ways to protect their information while upholding ethical standards. Continual learning and engagement in this area highlight the proactive nature of faith—encouraging believers to stay informed and equipped to navigate complex issues.
In conclusion, encryption keys serve as powerful tools in the preservation of data integrity and privacy. From a Christian perspective, the implications extend beyond technology; they encompass ethical stewardship, trustworthy communication, and a commitment to righteousness. As the digital age presses forward, navigating the intricate balance of security and transparency will be paramount. Embracing these principles fosters an environment conducive to not only safe interactions but also a reflection of divine values in an increasingly complex world. Understanding and applying the concept of encryption keys inspires deeper reflections on the nature of trust and the integrity of personal and communal relationships, both online and offline.







Leave a Comment