In an age where digital security concerns are omnipresent, encryption stands as an essential barrier against unwanted intrusions. Among the myriad of algorithms that exist, the Advanced Encryption Standard (AES) has garnered significant attention, particularly the 256-bit variant, often lauded for its formidable strength. But what precisely is AES 256 encryption, and why is it frequently described as nearly unbreakable? This inquiry is not just a technological one; it touches upon philosophical and ethical dimensions that resonate within a Christian perspective.
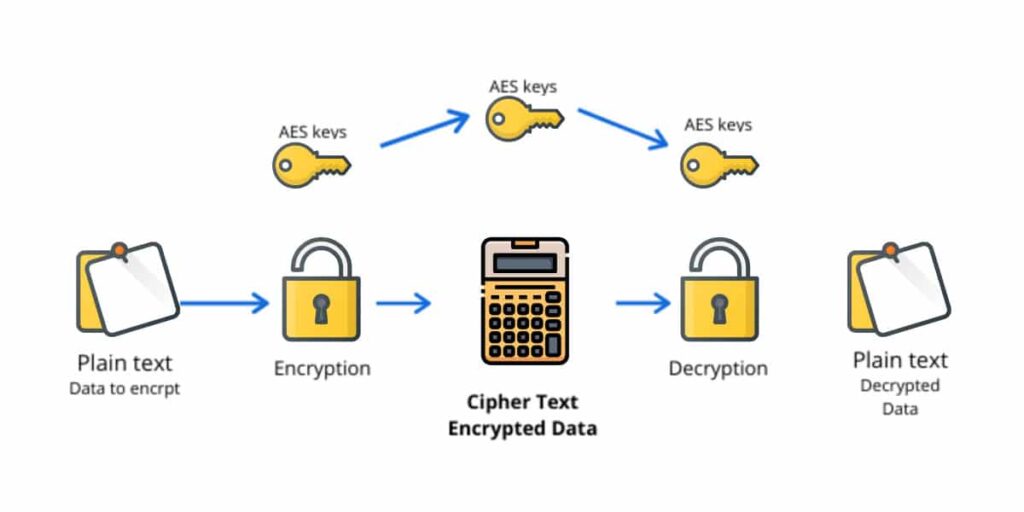
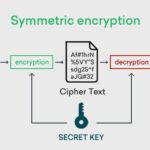
To understand AES 256 encryption, one must first appreciate its purpose: to render critical data unintelligible to those without the decryption key. AES was established as a standard by the National Institute of Standards and Technology (NIST) in 2001. It operates through a symmetric key algorithm, meaning that the same key is utilized for both encryption and decryption. While many encryption standards exist, the robustness of AES—specifically its 256-bit key size—has positioned it as the gold standard against cyber threats.
So, what does the ‘256-bits’ signify? Each bit represents a binary digit, with 256-bit keys consisting of 2256 possible combinations. To put this into perspective, that number surpasses the total grains of sand on every beach on Earth. The astronomical size of this key space renders brute force attacks—wherein an attacker systematically attempts every possible key—practically infeasible. One could challenge any doubting Thomas: could you feasibly imagine trying every single key in your lifetime?
From a Christian perspective, the implications of AES 256 encryption delve into deeper moral terrains. In a world fraught with violations of privacy and rampant cyber crimes, many believers find a semblance of security and peace in knowing their information is fortified against malevolent forces. Encrypted data can symbolize the protection of one’s digital soul—guarded fiercely against those who would seek to exploit vulnerabilities for personal gain.
Consider the biblical tenet of stewardship, where individuals are called to manage their resources wisely. In the digital realm, this also extends to safeguarding personal and sensitive information. If one views their data as entrusted to them by God or as an essential part of their identity, then leveraging strong protection methods like AES 256 becomes a moral obligation. Could neglecting such security efforts be perceived as failing to honor that stewardship?
Furthermore, AES 256 encryption facilitates faith-based organizations in their endeavor to protect congregants’ confidential information. Whether processing donations, collecting prayer requests, or maintaining sensitive communication, the obligation to ensure safety and confidentiality resonates with Christian values of caring for one another. An encrypted digital landscape thus affords churches the assurance needed to foster trust within their communities.
Delving deeper, one might ponder the philosophical implications of encryption. Is there not an intrinsic value to keeping certain things hidden? Just as God often conceals mysteries beyond human comprehension, so too does encryption allow individuals to protect their intimate details from prying eyes. This parallel beckons a reflection: Should some elements of our lives remain encrypted, protected from exposure? The AES 256 encryption algorithm embodies this principle effectively.
Nonetheless, while AES 256 encryption provides incredible security, it is not entirely devoid of challenges. Advanced persistent threats, social engineering attacks, and vulnerabilities in non-encrypted systems can circumvent the protections afforded by encryption. Additionally, the rapid pace of technological advancement can lead to unforeseen weaknesses, urging continuous vigilance and improvement within the encryption landscape. Can we ever completely trust these systems, or is there an element of continual risk that remains?
Another aspect worth considering is the ethical dilemma surrounding encryption. While it serves as a fortress for individual privacy, it can also harbor illicit activities. Criminals can exploit the very same encryption algorithms to communicate and operate in secrecy. This duality raises a critical question: Should morality ever supersede security? In a Christian worldview, how can one justify the balance between protecting the innocent and ensuring the same tools don’t become a weapon for the malevolent?
Despite these complexities, the near-impervious nature of AES 256 encryption is undeniable. As we navigate a digital age that increasingly intertwines with our personal lives, understanding and employing effective encryption becomes paramount. Encryption cannot replace the ethical frameworks provided by faith; rather, it can serve as a tool within that context, enhancing one’s ability to uphold privacy, trust, and integrity.
In conclusion, the AES 256 encryption algorithm serves as a bastion of security in a volatile digital environment. It encapsulates not just technological prowess but also intertwines with ethical considerations, inviting a conversation within Christian frameworks about privacy, morality, and stewardship. As more of our lives are embedded in the digital world, the call to secure this information becomes exceptionally potent. Are you ready to embrace these tools, recognize their importance, and challenge yourself to think about the implications behind them? The safety of your digital self may very well hinge upon it.





Leave a Comment