In the realm of cryptography, where security meets the intricate dance of data integrity, the concept of a message digest stands as a sentinel against the lurking threats of unauthorized access and data tampering. But what precisely is a message digest? It is more than just an abstract construct; it embodies the quintessence of ensuring that digital information remains unscathed. Let’s embark on an exploration to unveil the multifaceted nature of message digests, their operational mechanics, significance, and the transformative implications they hold for data security.
A message digest, at its core, represents a condensed version of data produced by a hash function. When any piece of content—be it a short text message, a lengthy document, or an intricate software package—undergoes hashing, the outcome is a fixed-size string of characters, commonly referred to as a digest. This digest is not just a representation; it encapsulates the essence of the original data, serving as a unique fingerprint that betrays no information about the content itself but offers a powerful means of verification.
To understand the significance of message digests, we must first examine the concept of hashing. Hash functions are algorithmic processes that take input data of arbitrary size and convert it into an output of fixed size, typically represented in hexadecimal form. Cryptographic hash functions exhibit critical attributes: determinism, non-invertibility, and collision resistance. Determinism ensures that the same input consistently produces the same output, while non-invertibility indicates that it is computationally infeasible to reconstruct the original data from the hash. Collision resistance further fortifies this mechanism by guaranteeing that two distinct inputs do not yield the same hash output. This triumvirate of properties is crucial for maintaining the sanctity of data in the digital age.
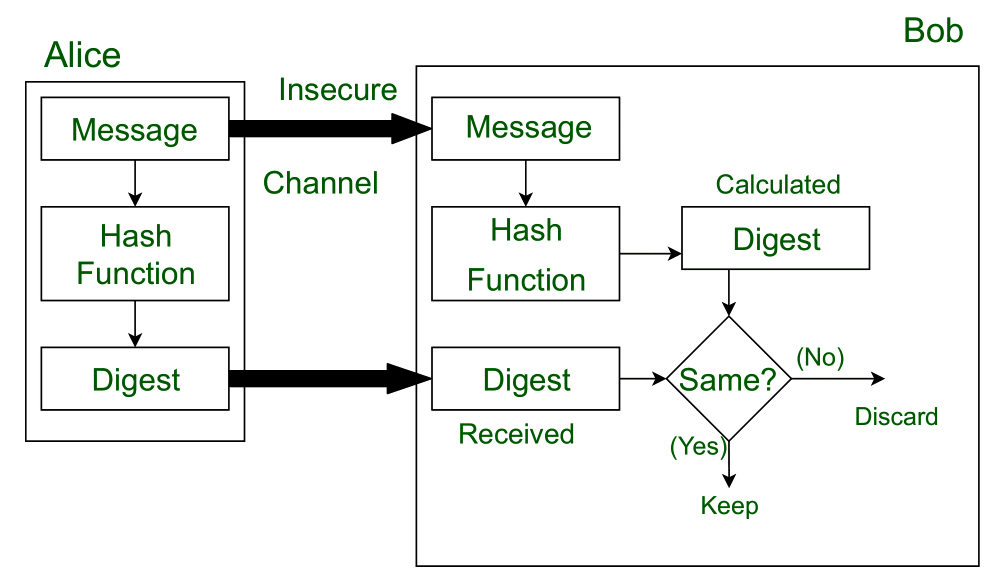
One of the principal utilizations of a message digest lies in data integrity verification. When transmitting sensitive information across the internet or storing it in databases, the threat of alteration—either maliciously or accidentally—looms large. By generating a message digest from the original data before transmission and sharing it alongside the content, the recipient can independently compute the digest of the received data. If both digests match, the information has remained untarnished; if they diverge, tampering is evident. This mechanism fosters a robust model of trust, pivotal in e-commerce transactions and digital communications.
In addition to integrity, semantic implications arise in relation to authentication. Imagine accessing a secure online account. Instead of transmitting your password directly—a perilous endeavor prone to interception—systems often utilize message digests. In this scenario, the password is hashed into a digest, which is then stored in the server. Upon user login, the entered password undergoes hashing, and the resulting digest is compared to the stored variant. This method ensures that even if an attacker compromises the database, only hashed values are accessible, thereby safeguarding user credentials.
Evolving from mere data protection, message digests find application in a plethora of domains. Digital signatures, for instance, utilize message digests as part of cryptographic protocols to validate authenticity. When signing a document, the signer hashes the content, and the output is then encrypted with their private key. The recipient decrypts the signature using the corresponding public key and verifies the digest, providing assurance of both origin and integrity.
Furthermore, blockchains, the backbone of cryptocurrencies and decentralized finance, rely heavily on message digests to maintain a transparent and secure ledger. Each block contains a hash of the previous block, ensuring a cohesive chain of information. This structure not only bolsters data integrity but also renders it immutable; altering any single block requires recalculating the hashes of all subsequent blocks, an endeavor computationally prohibitive due to the consensus mechanisms employed.
However, as the landscape of cybersecurity evolves, so does the scrutiny of message digests. Consider the implications of potential vulnerabilities. As computational power surges with advancements in technology, attacks such as collision attacks—where two distinct inputs result in the same digest—become plausible. This has led to the abandonment of older hash functions, like MD5 and SHA-1, in favor of more robust alternatives, such as SHA-256 and SHA-3. The landscape is always shifting, and so too must the methods we employ to safeguard our digital world.
The dialogue surrounding message digests is enriched by the dichotomy between their utility and the emerging vulnerabilities. As we reflect on their transformative role in cryptography, it invites contemplation about the future of data security. How will the interplay between innovation and threat evolve? The advent of quantum computing looms large, potentially unravelling conventional encryption methods, including those grounded in hash functions.
In conclusion, message digests symbolize a pivotal innovation in the field of cryptography, encapsulating the essence of data in a compact form while ensuring its integrity and authenticity. They stand at the intersection of necessity and vulnerability, pushing the boundaries of what is possible in the realm of digital security. As technology advances, the concepts of hashing and message digests will likewise necessitate evolution, prompting continual reassessment and adaptation. The journey does not end here; it merely heralds a new chapter of inquiry into the mercurial balance between protection and threat in the digital landscape.








Leave a Comment