In an age where technology permeates every facet of life, understanding cybersecurity becomes paramount. Among the various threats that lurk in the digital realm, the brute force attack stands out as a particularly malicious tactic. This form of cyber intrusion can be likened to an uninvited guest at a family gathering, relentlessly trying to force their way in. As Christians, we are called to be wise stewards of our resources, including our digital assets. This discourse will illuminate the nature of brute force attacks, explore biblical perspectives that resonate with safeguarding integrity and security, and provide actionable steps for efficacious prevention.
What is a Brute Force Attack?
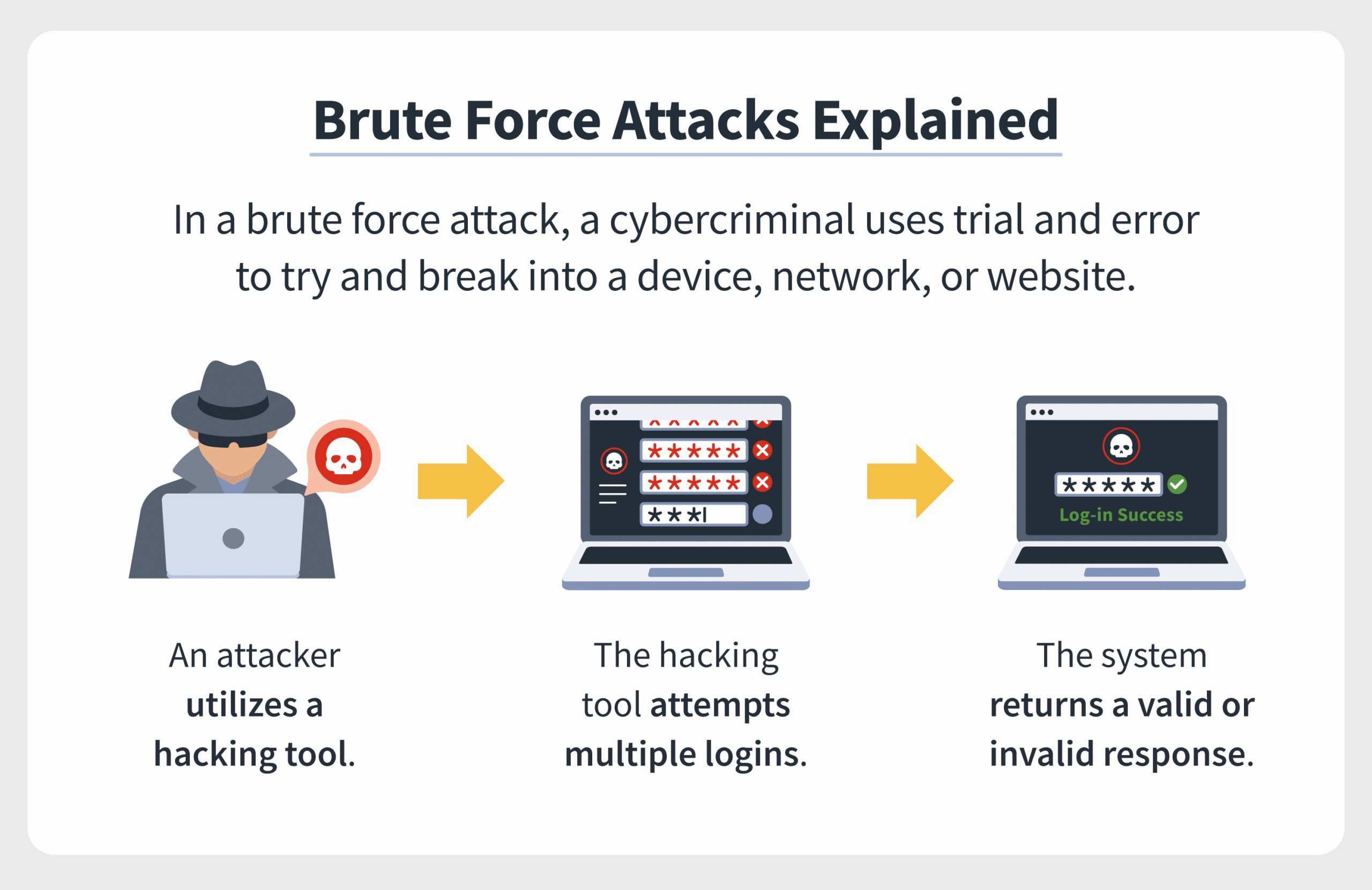
A brute force attack is a method employed by cybercriminals to gain unauthorized access to systems, accounts, or networks by systematically attempting every conceivable password or encryption key until the correct one is discovered. Think of it as trying every key on a keychain, one after another, hoping to unlock a door. This cumbersome process may utilize automated software tools that can execute thousands of attempts within seconds, illustrating the relentless nature of such assaults.
The implications of successful brute force attacks are multifaceted. They can lead to the compromise of sensitive information—ranging from personal identification details to financial data—resulting in significant emotional and financial strain on the victim. In this context, Proverbs 4:23, “Above all else, guard your heart, for everything you do flows from it,” resonates deeply. Just as one guards their heart, so too must one safeguard their digital presence.
Types of Brute Force Attacks
Brute force attacks come in several varieties, each with its own nuances that reflect the creativity of cybercriminals. The most common types include:
- Simple Brute Force Attack: This basic approach methodically tries all possible combinations of characters until the correct password is found.
- Dictionary Attack: Using a prearranged list of potential passwords, this technique attempts common words and phrases, banking on human tendencies to choose easily memorable passwords.
- Credential Stuffing: Leveraging stolen credentials from other platforms, attackers exploit the common practice of reusing passwords across multiple sites.
- Reverse Brute Force Attack: This strategy starts with a known password and tests it against various usernames, seeking to find matches.
Understanding these methods not only cultivates awareness but also emphasizes the need for vigilance, mirroring the biblical principle found in Matthew 10:16, “I am sending you out like sheep among wolves. Therefore be as shrewd as snakes and as innocent as doves.” In essence, we are called to be astute and discerning in the face of potential threats.
Recognizing the Signs of a Brute Force Attack
Awareness is the cornerstone of prevention. Identifying the signs that a brute force attack is underway can make a significant difference in addressing the threat. Common indicators include:
- Unusual login attempts from unfamiliar locations or devices.
- Excessive requests from a single IP address.
- Account lockouts or notifications that appear unexpectedly.
As Christians, we are encouraged to be vigilant, echoing the message of 1 Peter 5:8, which implores, “Be alert and of sober mind. Your enemy the devil prowls around like a roaring lion looking for someone to devour.” This verse reinforces the importance of being proactive in safeguarding our digital territories.
Effective Prevention Strategies
To thwart potential brute force attacks, implementing robust security measures is essential. Below are several strategies that can significantly bolster one’s defenses:
- Employ Complex Passwords: Encourage the use of strong, unique passwords that mix letters, numbers, and symbols. This complexity makes it more challenging for attackers to achieve success.
- Enable Two-Factor Authentication (2FA): This additional layer of security ensures that even if a password is compromised, further verification is required to gain access.
- Utilize Account Lockout Mechanisms: Configuring systems to lock accounts after a predetermined number of failed login attempts helps deter attackers.
- Monitor and Log Activity: Regularly reviewing access logs can help identify and respond to suspicious behavior swiftly.
By adopting these measures, individuals can guard against potential breaches, illustrating the biblical directive found in Luke 14:31 regarding wise planning: “Or suppose a king is about to go to war against another king. Won’t he first sit down and consider whether he is able with ten thousand men to oppose the one coming against him with twenty thousand?” Preparation and strategy are crucial in both spiritual and cybersecurity realms.
The Christian Perspective on Digital Security
In conclusion, the threat of brute force attacks serves as a microcosm of the spiritual warfare that Christians engage in daily. Just as we are called to guard our hearts and minds—a theme echoed throughout scripture—we must also extend this diligence to our digital lives. The principles of caution, preparation, and vigilance extend beyond physical realms into the virtual world, reinforcing our stewardship of the resources entrusted to us.
In navigating the complexities of the digital landscape, remember that each act of security is an act of faithfulness to the gifts bestowed upon us. By mastering the art of digital stewardship, we not only protect ourselves but also stand as exemplars of wisdom in a world fraught with peril. The pursuit of cybersecurity is not merely a technical endeavor; it is a manifestation of our commitment to honoring the integrity of our lives as stewards of God’s creation.







Leave a Comment