In the digital age, the importance of securing online communications cannot be overstated. Imagine navigating the vast ocean of the internet without any protection against lurking threats. What if, instead of sailing smoothly, you were surrounded by pirates ready to intercept your valuable cargo? This allegory aptly parallels the perils of unsecured connections. Transport Layer Security (TLS), an advanced cryptographic protocol, acts as your digital guardian, ensuring that your online interactions remain confidential and secure. But what does TLS specifically protect you from? Let’s explore this intriguing landscape.
To understand TLS’s protective capabilities, we first need to delve into its fundamental purpose. At its core, TLS is designed to safeguard data transmitted over the internet. This involves multiple layers of protection, including encryption, authentication, and integrity checks. But how exactly do these components work to shield users from various online threats? Let’s break this down into discernible categories.
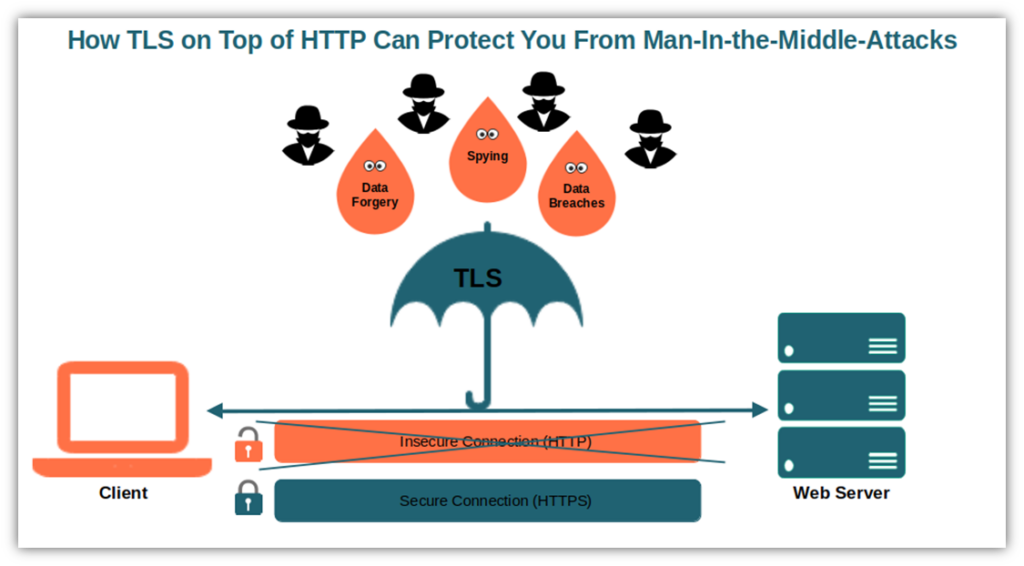
One of the most critical threats that TLS addresses is the eavesdropping of sensitive information. Picture a scenario where a user is shopping online, entering credit card details and personal information. Without TLS, this data is transmitted in plain text, easily accessible to anyone intercepting the communication. This is akin to sending a postcard with your personal messages visible to passersby. TLS encrypts this sensitive data, transforming it into a coded format incomprehensible to unauthorized individuals. The encryption ensures that even if data is intercepted, it remains protected by layers of cryptographic complexity.
Moreover, TLS provides a robust shield against man-in-the-middle (MITM) attacks. These attacks occur when an adversary secretly intercepts and relays messages between two parties, typically to steal information or inject malicious content. Imagine having a conversation with a friend, unaware that a third party is eavesdropping and altering your words. TLS thwarts this scenario by ensuring that both parties authenticate each other before any data exchange occurs. This mutual authentication creates a trusted connection, reinforcing the integrity of the communication.
In addition to protecting data from eavesdroppers and MITM attacks, TLS also helps maintain the authenticity of websites. When users visit a TLS-secured website, they can verify its legitimacy through digital certificates issued by trusted Certificate Authorities (CAs). Without this mechanism, navigating the internet would be akin to wandering through a marketplace where every vendor is masked, making it impossible to distinguish between genuine businesses and fraudulent ones. TLS enables users to confirm that they are indeed communicating with the intended website, thereby reducing the risk of falling victim to phishing scams and other deceptive practices.
But wait — what about data integrity? This aspect of TLS ensures that information remains unaltered during transmission. Imagine sending a legal document via email; if someone were to modify the document in transit, it could lead to severe legal ramifications. TLS employs cryptographic hashes to detect any unauthorized alterations, alerting users if the data they receive differs from the original. This layer of security provides peace of mind, assuring users that the information exchanged is precisely as intended.
As we navigate further into the benefits of TLS, one cannot ignore the importance of user trust. In a world rife with data breaches and cyberattacks, users are becoming increasingly wary of where they share their information. Secure connections foster an environment of trust; when users see that a website employs TLS (indicated by the familiar padlock symbol in the browser’s address bar), they are more likely to engage in transactions and share sensitive information. This trust translates into higher engagement rates and a better overall online experience, enhancing the digital economy.
However, it’s essential to recognize that no security protocol is infallible. While TLS significantly mitigates risks, the digital landscape is constantly evolving, and attackers are always on the hunt for vulnerabilities. Therefore, users must remain vigilant and adopt a multifaceted approach to online security. This includes utilizing antivirus software, being cautious about sharing personal information, and ensuring that their devices are up to date with the latest security patches.
Yet, the question lingers — how does one ensure that they are consistently protected by TLS? One crucial step is verifying the presence of the protocol on websites. Users should always look for URLs that begin with “https://” rather than the unsecured “http://.” The added ‘s’ signifies a secure, encrypted connection underlined by TLS. Additionally, understanding the implications of certificate warnings is vital; if a browser indicates that a certificate is invalid, it should serve as a red flag, raising doubts about the site’s authenticity.
In conclusion, TLS stands as a formidable bastion against an array of online threats, ranging from eavesdropping and MITM attacks to data integrity breaches and trust issues. By encapsulating data in an encrypted cocoon, authenticating communications, and ensuring the authenticity of websites, TLS plays a pivotal role in securing the digital interactions of millions of users worldwide. While it certainly helps to fortify one’s online presence, it is essential to remain proactive and integrate other security practices into one’s digital routine. As the online world continues to evolve, so too must our understanding of the tools available to protect ourselves in this vast, unpredictable sea.






Leave a Comment