Data encryption is a fundamental concept in the realm of cybersecurity, yet it often baffles many. So, what does data encryption mean in simple terms? Imagine having a secret message that only you and your best friend can understand, while others look at it and see nothing but a jumble of meaningless characters. This is the essence of encryption. It transforms readable data into an unreadable format, ensuring that only authorized users can decipher the information. But what happens when the key to that cipher is lost? That’s the challenge of encryption, and it raises the question: Can your secrets remain safe even if the key is compromised?
To grasp data encryption fully, let’s delve deeper into its components, processes, and implications.
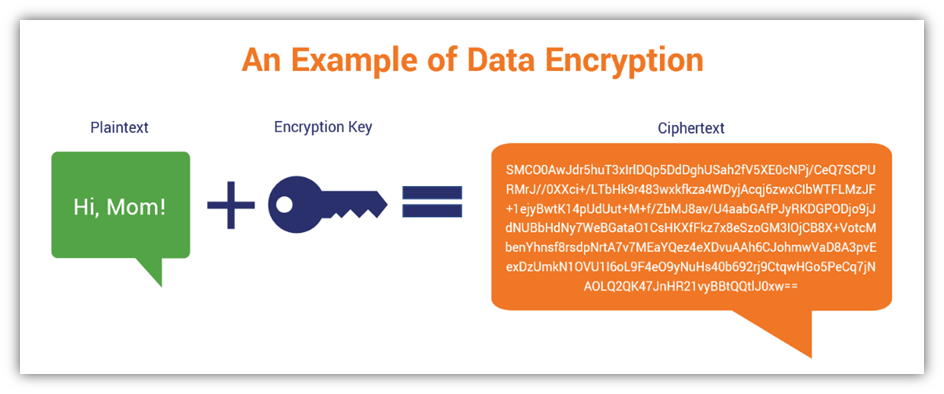
1. The Fundamentals of Data Encryption
At its core, encryption involves two primary components: plaintext and ciphertext. Plaintext is the original data that is intelligible and useful. It could be a message, a password, or even sensitive personal information. Ciphertext, on the other hand, is the scrambled version of this data, created through an algorithm known as an encryption algorithm.
Encryption algorithms employ mathematical functions to transform plaintext into ciphertext. There are various types of encryption, but the two most prevalent forms are symmetric and asymmetric encryption. In symmetric encryption, the same key is used to encrypt and decrypt the information. It’s like having one key that opens a lock; the keyholder must be trustworthy. Conversely, asymmetric encryption employs two keys: a public key, which can be shared widely, and a private key, which is kept secret. This dual-key system enhances security, enabling users to share their public keys without fear.
2. Real-World Applications of Encryption
Encrypting data is crucial in our increasingly digital world. Consider this: every time you shop online, conduct banking transactions, or share personal information over the internet, encryption is working behind the scenes to protect your data. Websites that start with “https” utilize a protocol known as SSL (Secure Socket Layer) to ensure that the data exchanged between clients and servers is encrypted.
Imagine sending your credit card number through an unencrypted channel. It would be akin to sending a postcard containing sensitive information—and anyone passing by could read it! However, when encryption is applied, your credit card details are securely encoded, rendering them useless to anyone intercepting the data.
Another widespread application is in messaging platforms. Apps like WhatsApp and Signal provide end-to-end encryption, which ensures that only the sender and recipient can read the messages exchanged. This scenario emphasizes the practicality and necessity of encryption in safeguarding communication in a world rife with potential cyber threats.
3. The Challenges of Encryption
While encryption serves as a robust shield against unauthorized access, it brings forth its own set of challenges. One major concern is key management. For symmetric encryption, if the key is leaked or lost, unauthorized actors may gain access to the encrypted data, rendering the encryption ineffective. With asymmetric encryption, users must ensure they’re guarding their private keys zealously. If someone gains access to this key, they can impersonate the user and decrypt sensitive information.
Another challenge lies in the balance between security and usability. Overly complex encryption may frustrate users, leading them to revert to less secure practices. For instance, a user might choose simpler passwords or omit security features if they find the process cumbersome. The dilemma is apparent: how do we maintain robust protection while ensuring that users can operate seamlessly?
4. The Future of Data Encryption
As technology evolves, so too does the landscape of encryption. With the rise of quantum computing, traditional encryption methods may soon face obsolescence due to their vulnerability to quantum algorithms. Researchers are actively exploring quantum-resistant encryption methods to combat this potential threat. This development poses another playful question: will we be prepared for a new era of cryptography that could outsmart our current safety measures?
Moreover, governments and organizations are increasingly recognizing the significance of encryption in protecting national security and sensitive data. While some policymakers advocate for strong encryption to safeguard privacy, others argue for “backdoors” that would allow authorities access to encrypted communications. This debate highlights the ongoing tension between privacy and security—can a compromise even be reached without eroding user trust?
5. Conclusion
In summary, data encryption is a powerful tool that secures information from prying eyes and potential breaches. The transformation of plaintext into ciphertext safeguards personal data, financial transactions, and communication across digital platforms. However, encryption is not without its challenges, ranging from key management to the evolving technological threats posed by quantum computing. As we forge ahead in an increasingly interconnected world, the quest for robust encryption practices will undoubtedly remain a priority. Those who embrace encryption not only contribute to their own security but also bolster the broader digital landscape against growing vulnerabilities. The question remains: Is the fortress of encryption impenetrable, or are there cracks we have yet to discover?








Leave a Comment