Encryption, at its core, is a fascinating and intricate practice aimed at safeguarding information from prying eyes. As the digital world expands, understanding the fundamental elements that constitute any encryption method unveils not just the complexity of information security but also the critical role it plays in our daily lives. This exploration invites you to engage with intricate ideas that may forever alter your view of how data protection weaves into the fabric of modern communication.
To begin, it is essential to recognize that every encryption method is built upon several core elements. These components meticulously intertwine to create secure communication protocols. The first critical element is the plaintext. Plaintext refers to the original message or data that is intended for transmission. It serves as the foundation of the entire encryption process. Understanding plaintext is akin to recognizing the raw ingredients required before crafting a masterful dish. Without it, the entire edifice of encryption would lack substance.
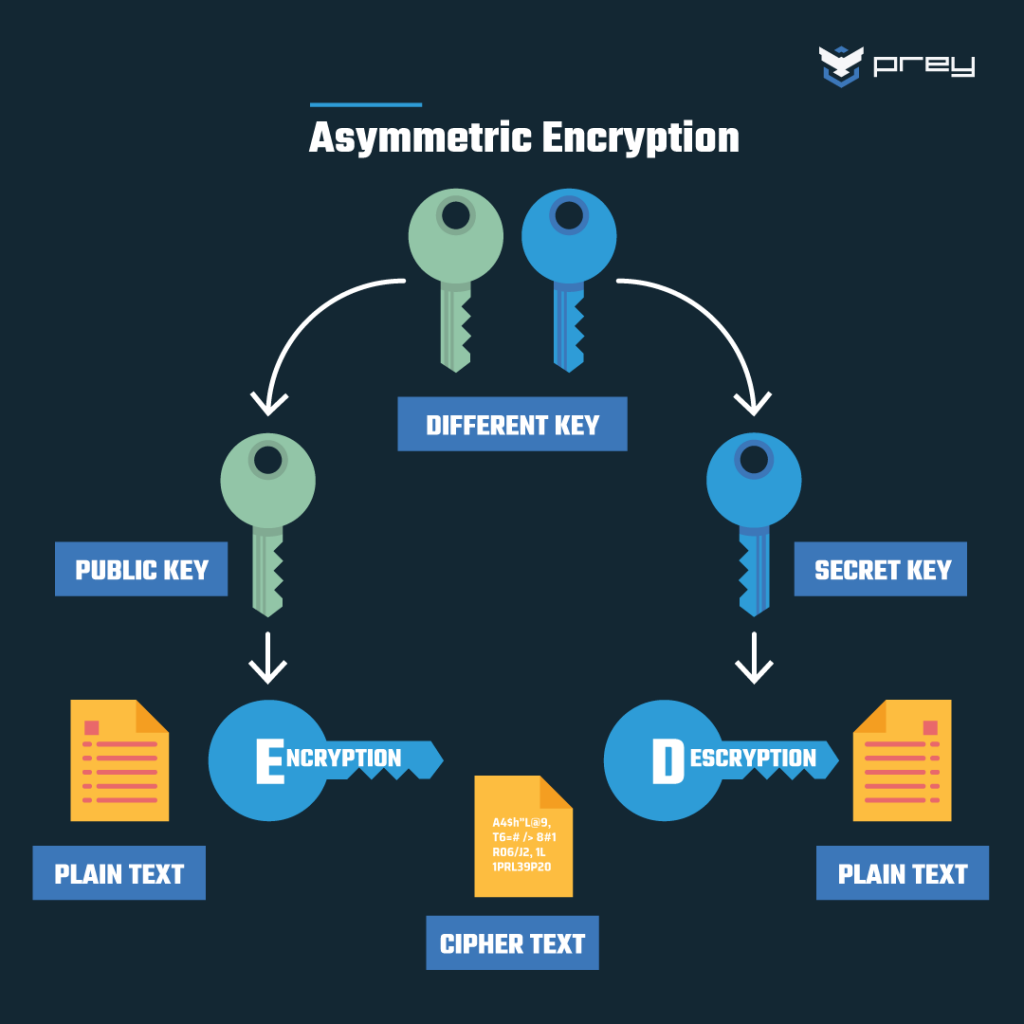
The second element is the cipher. A cipher is the algorithm or mathematical procedure utilized to convert plaintext into ciphertext. It functions as a transformative agent, reshaping information to ensure confidentiality. Ciphers can be subdivided into two primary categories: symmetric and asymmetric. Symmetric ciphers utilize the same key for both encryption and decryption, whereas asymmetric ciphers employ a pair of keys—a public key for encryption and a private key for decryption. This distinction is vital, as it highlights the divergent approaches to securing sensitive information.
Another indispensable component is the key, which acts as the catalyst for the cipher’s transformation process. The key is essentially a string of bits that determine the output of the encryption algorithm. Its importance cannot be overstated, for the strength of an encryption method hinges significantly on the key’s length and complexity. A longer, more complicated key exponentially increases the difficulty of unauthorized decryption. In a world rife with ever-evolving hacking techniques, the selection and management of cryptographic keys constitute a fundamental aspect of maintaining secure communications.
Besides the aforementioned elements, the ciphertext deserves meticulous attention. Ciphertext is the outcome of the encryption process, the transformed data that appears unintelligible to anyone without the corresponding key. Similar to a cloak shielding valuable treasures, ciphertext secures the integrity of the original information. The relationship between plaintext and ciphertext is one of transformation—a compelling dance between accessibility and security. An understanding of this relationship enables individuals to appreciate the underlying mechanisms of communication safety.
Furthermore, an often-overlooked element in encryption methodologies is the role of initialization vectors (IVs). IVs are random values incorporated into the encryption process to ensure that identical plaintext inputs yield different ciphertext outputs. This provision not only enhances security but also mitigates vulnerabilities associated with repeated patterns in data. Consequently, IVs contribute positively to the unpredictability of ciphertext and bolster the defense against cryptographic attacks.
Equally pertinent is the aspect of authentication. In the realm of encryption, authentication verifies the source and integrity of the transmitted data. This element is paramount in confirming that the received information has not been altered during transit. By incorporating mechanisms such as digital signatures or message authentication codes (MACs), encryption methods ensure that recipients can trust the authenticity of the data they receive. The interplay between encryption and authentication underscores the multi-faceted nature of secure communications.
It is also essential to consider the encryption protocols that govern how data is encrypted and exchanged. Various protocols, such as Secure Socket Layer (SSL), Transport Layer Security (TLS), or Pretty Good Privacy (PGP), dictate the rules and formats for implementing encryption in digital communications. Each protocol has its unique features, strengths, and weaknesses, forming a tapestry of security solutions tailored for different practical applications.
Now, as we delve deeper, we encounter the concept of entropy. In cryptography, entropy quantifies the unpredictability or randomness of data. A higher level of entropy in encryption contributes to greater security, as it renders the resultant keys and ciphertext challenging to predict or replicate. This concept underlines the importance of randomness in cryptography and serves as a reminder that predictability is the enemy of security.
Lastly, an often underestimated element is the human factor. Regardless of how sophisticated an encryption method may be, its efficacy is heavily reliant on user behavior and policy implementations. Poor key management, inadequate user education, and failure to follow best practices can compromise even the most robust encryption methods. As a result, organizations must cultivate a culture of security awareness that transcends technical prowess and emphasizes user responsibility.
In summation, the elements that constitute any encryption method—plaintext, ciphers, keys, ciphertext, initialization vectors, authentication, protocols, entropy, and the human factor—interact in a dynamic landscape of information security. Recognizing the significance of each component fosters a deeper understanding of the complexities of encryption. As the digital realm evolves, so does the need for secure methods of communication, beckoning us to embrace the intricacies and to remain vigilant in our approach to safeguarding information.







Leave a Comment