Data encryption is an indispensable facet of contemporary cybersecurity, safeguarding sensitive information from unauthorized access. This article delves into the myriad forms of data encryption methods, elucidating their functionalities, advantages, and optimal use cases. Understanding these various techniques is crucial for anyone looking to fortify their data security landscape.
1. Symmetric Encryption
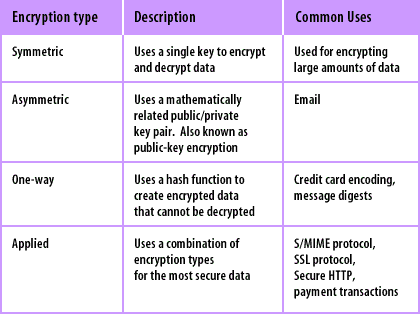
Symmetric encryption employs a single key for both encryption and decryption processes. This method is notably efficient, as it allows for rapid data processing. Key algorithms in this category include the Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Triple DES (3DES). AES has gained favor due to its robust security measures and versatility. However, the primary drawback is the necessity of securely sharing the key among parties without interception, which can pose logistics and security challenges.
2. Asymmetric Encryption
In stark contrast to symmetric encryption, asymmetric encryption utilizes a pair of keys: a public key and a private key. The public key encrypts the data, while the private key is employed for decryption. The RSA algorithm is the most renowned example of this method. As vital as it is secure, asymmetric encryption facilitates secure data exchanges over insecure channels, such as the internet. However, the encryption and decryption processes are considerably slower than those of symmetric encryption, making it less suitable for encrypting large volumes of data.
3. Hash Functions
Hash functions are a unique category of encryption techniques that transform input data into a fixed-size string of characters, which typically appears alphanumeric. This method is one-way; once data is hashed, it cannot be reversed to its original form. Examples include SHA-256, SHA-1, and MD5. Hash functions exert significant influence on data integrity checks and password storage schemes. However, it is crucial to note that older algorithms like MD5 and SHA-1 are deemed vulnerable, necessitating the adoption of more secure alternatives.
4. Digital Signatures
Digital signatures utilize asymmetric encryption to verify the authenticity and integrity of a message. They provide non-repudiation, ensuring the sender cannot deny sending the message. This method is widely utilized in various protocols, including Secure Sockets Layer (SSL) and Secure Hypertext Transfer Protocol (HTTPS). A digital signature is created by hashing the message and then encrypting the hash with the sender’s private key. This ensures that any alteration to the original message will invalidate the signature, thus safeguarding against tampering.
5. End-to-End Encryption
End-to-end encryption (E2EE) is a method that guarantees only the communicating users can read the messages. In this paradigm, data is encrypted on the sender’s device and only decrypted on the recipient’s device. This fortify-segmented communication is increasingly implemented in messaging applications like WhatsApp and Signal. By ensuring data remains encrypted during transmission, E2EE substantially mitigates the risks associated with interception by third parties.
6. File Encryption
File encryption refers to the process of transforming files into a secured format that cannot be accessed without an appropriate decryption key or password. Popular file encryption tools include VeraCrypt and BitLocker. This method is pivotal for individuals and organizations that store sensitive data on their devices or in cloud environments. It is particularly effective in protecting data from unauthorized access due to physical theft or cyberattacks.
7. Whole Disk Encryption
Whole disk encryption is an expansive technique where an entire storage device is encrypted, ensuring that all contents are protected without the need for separate encryption for each file. Solutions like BitLocker (for Windows) and FileVault (for macOS) provide this level of security. This method is particularly advantageous for laptops and mobile devices, which are prone to theft and loss, thus preserving the confidentiality of all data stored therein.
8. Database Encryption
Database encryption focuses on securing sensitive data within specific databases. Rather than encrypting entire files or disks, this method encrypts individual elements or fields in a database. Tools such as Transparent Data Encryption (TDE) are employed to manage the encryption and decryption processes without requiring changes to the database structure. This is quintessential in environments where data integrity and compliance with regulations, such as GDPR or PCI-DSS, are paramount.
9. Cloud Encryption
As organizations increasingly migrate to the cloud, cloud encryption has arisen as a pivotal mechanism for safeguarding data stored remotely. Cloud encryption solutions protect data both at rest and in transit. Providers typically offer tools that allow users to encrypt their data before uploading it to a cloud service. This prevents unauthorized access, insider threats, and ensures compliance with various regulatory requirements, adding a significant layer of security.
Conclusion
Exploring the diverse types of data encryption methods reveals a profusion of strategies designed to enhance data security. From symmetric and asymmetric encryption to specialized techniques such as hashing and digital signatures, each method serves distinct purposes and is better suited for different scenarios. By selecting the appropriate encryption technique, individuals and organizations can significantly reduce their vulnerability to cyber threats, ensuring the integrity and confidentiality of sensitive information in an age where data breaches remain increasingly prevalent.







Leave a Comment