AES (Advanced Encryption Standard) is widely regarded as one of the most secure encryption methods available today. However, when implemented in Cipher Block Chaining (CBC) mode, it reveals certain vulnerabilities and limitations that can hinder its effectiveness under specific circumstances. So, is it possible that a method heralded as secure can, in practice, present substantial drawbacks? This article delves into the disadvantages of AES in CBC mode, shedding light on its operational challenges.
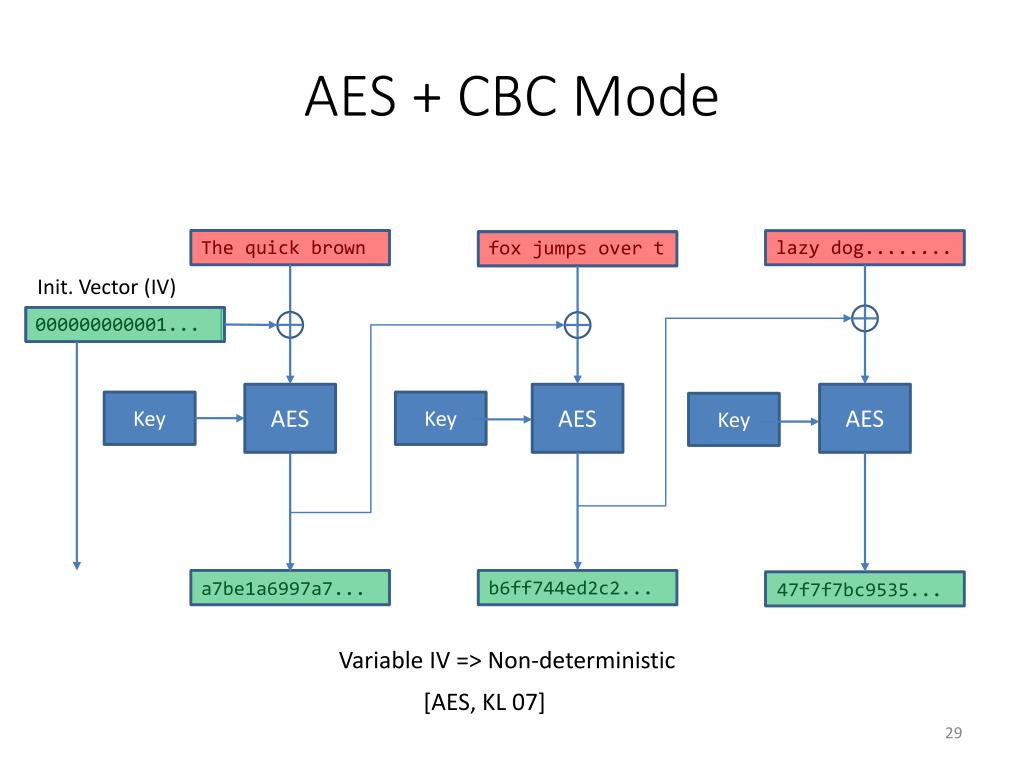
At its core, CBC mode operates by combining the plaintext with the previous ciphertext block before encryption. While this dependency introduces a layer of complexity, it also generates several distinctive drawbacks that can be problematic in real-world scenarios.
1. Vulnerability to Padding Oracle Attacks
One of the most prominent vulnerabilities of AES in CBC mode is its susceptibility to padding oracle attacks. This occurs when the system reveals information through differing error messages depending on the validity of the padding in the decrypted message. Attackers can exploit this behavior to decrypt ciphertext without the key, essentially rendering the encryption ineffective. In a world where data breaches are prevalent, this type of vulnerability poses an alarming threat.
2. Propagation of Errors
If one block of a message is corrupted during transmission, the effects can be catastrophic. In CBC mode, if a single block is altered, not only does the altered block suffer from distortion upon decryption, but the subsequent block is also affected. This phenomenon is known as error propagation. In practical environments, such as network communications where data integrity is paramount, this characteristic can lead to significant loss of information.
3. Ciphertext Manipulation
While the strength of AES lies in its robust encryption, CBC mode is not immune to manipulation by adversaries. If an attacker can modify the ciphertext without detection, they can influence the plaintext output during decryption. For instance, by flipping specific bits in the ciphertext, they may manipulate the outcome in predictable ways, leading to unauthorized alterations in the decoded information. This potentiality raises questions about the reliability of secured communications that utilize AES in CBC mode.
4. Inefficiency in Parallel Processing
A major characteristic of CBC mode is its inherent sequential nature. Each block of plaintext must wait for the previous block’s ciphertext to begin encryption. This limitation creates inefficiencies crucial in environments that demand speed and performance. Modern applications often require parallel encryption methods to optimize throughput; however, AES in CBC mode cannot be executed in parallel, hampering its utility in high-performance contexts.
5. Key Management Complexity
The complexity of key management cannot be overlooked when considering the use of AES in CBC mode. Keys must be securely generated, distributed, and managed to ensure the confidentiality of encrypted data. The security of encryption hinges on the strength and secrecy of the key; if even a single key is compromised, the entire system falls into jeopardy. This requirement necessitates robust policies and systems for key management, complicating the overall encryption architecture.
6. Initialization Vector (IV) Dependence
The use of an initialization vector (IV) is crucial for ensuring that identical plaintext blocks yield differing ciphertexts. However, the selection and management of the IV introduce additional challenges when implementing AES in CBC mode. If the IV is not sufficiently random or is reused across multiple encryptions, it can lead to vulnerabilities, potentially enabling attackers to detect patterns and infer valuable information. Moreover, improper handling of the IV can result in repeated ciphertext patterns, thereby diminishing the security of the encryption design.
7. Limitations in Data Authentication
AES in CBC mode exclusively provides data confidentiality but neglects data integrity and authenticity. In the absence of a robust integrity-checking mechanism, attackers can modify the ciphertext without any detection mechanism to prevent the modification. This absence of integrated data authenticity solutions necessitates the need for additional measures, such as HMAC (Hash-based Message Authentication Code), to ensure that data has not been altered maliciously. Thus, the exclusive focus on confidentiality invites a holistic security gap.
Conclusion
While AES in CBC mode has its place in the realm of cryptography, its disadvantages present substantial challenges that must be addressed. From vulnerability to padding oracle attacks to key management complexities, each drawback poses significant risks that organizations must navigate carefully. The necessity for added layers of security, efficient processes, and rigorous data integrity measures becomes abundantly clear. As technology evolves, so must encryption methods. For AES in CBC mode, the conversation must continue in pursuit of enhanced methods that address these inherent limitations without sacrificing security and efficiency.







Leave a Comment