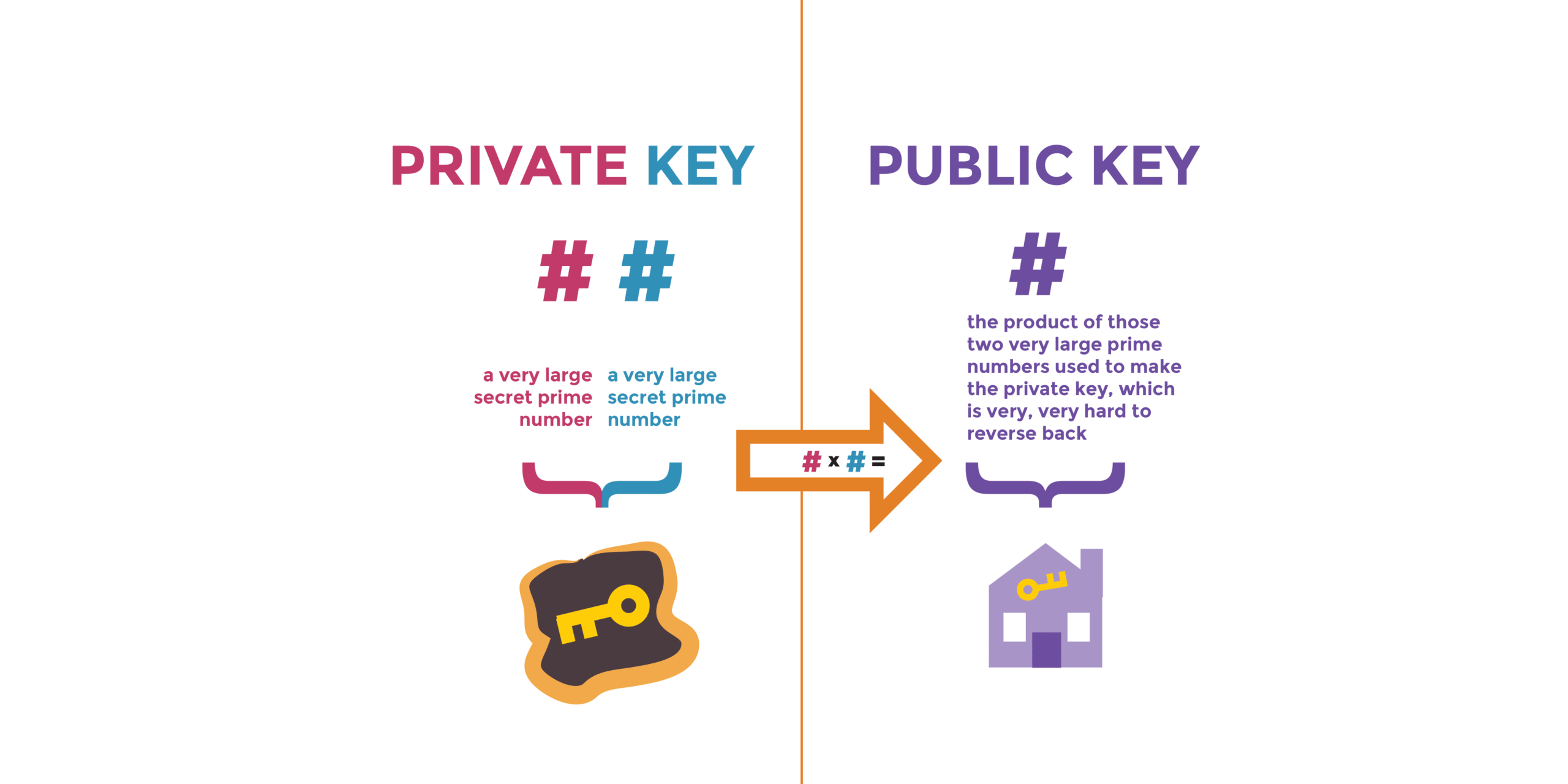
In the digital wilderness of the 21st century, the interplay between privacy and connectivity has given birth to a complex yet fascinating realm of cryptography. At the forefront of this field lie two fundamental constructs: private keys and public keys. These keys inhabit a symbiotic relationship, akin to that of a knight and their trusted steed — one is cloaked in secrecy while the other roams freely, forging connections in a turbulent digital landscape.
Private keys serve as the vigilant guardians of your digital fortress. They are unique, secretive arcs of data that whisper the essence of your identity, akin to the delicate strands of a spider’s web awaiting the slightest vibration. Within the context of public key cryptography, the private key is used to encrypt and decrypt messages. It’s imperative that this key remains clandestine; exposing it is tantamount to providing an intruder with the very blueprint of your sanctuary.
Conversely, public keys are the heralds of your digital existence, inviting communication while ensuring that interactions occur within a framework of security. Accessible and distributable, public keys allow users to share their identities and establish secure channels without compromising the integrity of their private keys. If we continue with our metaphor of the knight and steed, the public key is the knight’s crest, boldly displayed to signal trustworthiness to potential allies.
To illuminate this duality further, let us delve into the workings of public key infrastructure (PKI). Here, public keys are generated mathematically in tandem with their corresponding private keys. Think of it as a complex dance where two partners are paired perfectly; when one partner moves, the other responds. This meticulous coordination ensures that encrypted messages intended for a particular recipient can only be decoded by the rightful owner of the private key. When you send an encrypted email, for instance, your message is enveloped within the public key of the recipient. Only their private key can unravel the encryption, revealing the precious content within.
Let’s wander deeper into the practical applications of private and public keys. Imagine a quaint village where everyone communicates through locked boxes. The public key is the lock that everyone in the village can use to secure messages they wish to send. When someone locks their message inside the box using your public key, only your private key can unlock and read the message. This ensures that even if the box were intercepted, the contents remain sealed, preserving confidentiality.
Digital signatures exemplify another remarkable domain where private and public keys intertwine. In this scenario, the sender employs their private key to create a signature that encapsulates the essence of the message. This signature is then verified by the recipient using the sender’s public key. Hence, a digital signature not only asserts that the message originated from the claimed sender but also guarantees that it remains unaltered in transit. It functions like an ancient seal; unbroken, it attests to authenticity and integrity.
Consider the implications of blockchain technology, where public and private keys underpin the very fabric of decentralized finance (DeFi) and non-fungible tokens (NFTs). In this realm, individuals wield private keys as their digital dominions. Ownership of cryptocurrencies or digital assets is denoted by the possession of the corresponding private key. Losing this key renders one’s fortunes inaccessible, exemplifying the precarious balance of power in a decentralized ecosystem. Meanwhile, public keys facilitate transactions, allowing users to send and receive assets across the blockchain, serving as their digital address.
The allure of private and public keys does not merely lie in their functionality but also in the romance of security they offer in an increasingly perilous digital world. The notion that one can communicate freely and securely embodies a fundamental human aspiration — the quest for privacy amid openness. However, this equilibrium requires diligence. With great power comes great responsibility; handling private keys necessitates vigilance and proper storage practices, often encapsulated in hardware wallets or secure software solutions.
As we traverse this intricate landscape, it becomes abundantly clear that understanding the intricacies of private and public keys is paramount. They exemplify the delicate balancing act between security and accessibility, privacy and connectivity. The knight with a steadfast steed might be an apt metaphor, but even they are not immune to the challenges posed by an evolving landscape riddled with threats. In the realm of cryptography, safeguarding your keys is tantamount to fortifying your castle — had the attackers breached the walls, your treasures would surely be a mere whisper in the wind.
In conclusion, the synthesis of private and public keys represents an elegant solution to the age-old concerns of communication: security, integrity, and authenticity. As the digital universe expands and converges, the need for cryptographic awareness becomes increasingly salient. Our ability to protect ourselves hinges not only on technological advancements but also on our understanding of the very tools at our disposal. Every user must become the custodian of their own keys, vigilant in the face of potential threats, ensuring that their voice within the vast digital expanse remains secure, resonant, and unequivocally theirs.







Leave a Comment