SHA-256, or Secure Hash Algorithm 256-bit, has become synonymous with data integrity and security in the digital realm. Developed as part of the SHA-2 family by the National Security Agency (NSA) in 2001, this cryptographic algorithm has attracted attention for its robustness. With the advent of an era where data breaches and cyber threats loom larger than ever, one might wonder: is there an algorithm that can reverse SHA-256? The straightforward answer is no, but the inquiry opens a portal into the intricacies of cryptography, hash functions, and their overall significance in the digital age.
Before delving into whether SHA-256 can be reversed, it is crucial to understand the fundamental purpose of hash functions. Primarily, hash functions convert input data—regardless of its size—into a fixed-size string of characters, which typically appears as a seemingly random sequence of numbers and letters. These functions facilitate a variety of applications ranging from password storage to file integrity verification. Importantly, a well-designed cryptographic hash function: exhibits pre-image resistance, second pre-image resistance, and collision resistance.
To pose a challenge, consider this scenario: You have a piece of data, and you hash it using SHA-256. Is there any algorithmic way to regenerate the original data from its hash? While one might intuitively approach this question, the mechanics of hashing fundamentally dictate that this process is inherently asymmetrical. Given a hash output, it is computationally implausible to reconstruct the corresponding input. This quality is what fortifies SHA-256 as a stalwart in secure data transmission.
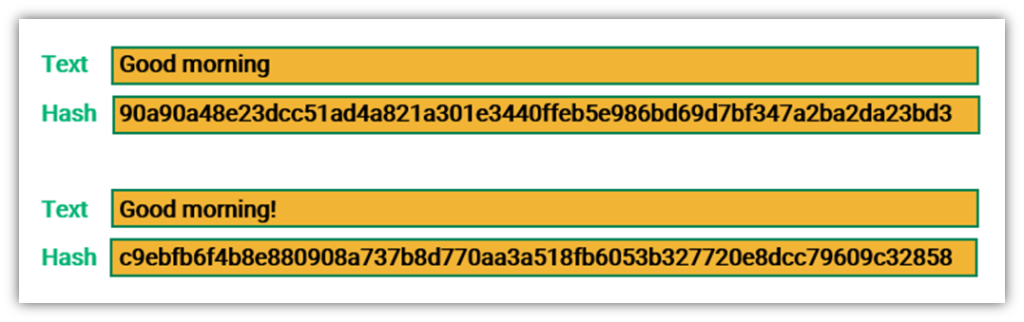
Let us explore further the fundamental principles underpinning SHA-256. The algorithm generates a 256-bit or 32-byte hash value. This is achieved through a series of intricate operations that include bitwise logical operations, modular additions, and compression functions. Each transformation contributes to what is known as the hash digest. This digest acts as a unique fingerprint of the original data, incorporating an essential feature of unpredictability. A tiny alteration in the input data results in a completely different hash, ensuring that even similar inputs are distinctly separated in the output space.
Now, the concept of reversing a hash may appear to flirt with the realms of possibility under certain circumstances. For instance, dictionary attacks and brute force attacks demonstrate attempts to uncover original inputs for specific hash values. However, these methods rely not on reversing SHA-256 but rather on systematic trial and error using predefined lists or sheer computational brute force. The sheer scale of 2256 possible combinations serves as an insurmountable barrier, showcasing the algorithm’s robustness.
Furthermore, the notion of collision resistance plays a pivotal role in affirming SHA-256’s efficacy. Collisions occur when two distinct inputs generate the same hash output. A collision-resistant hash function inhibits attackers from successfully finding two different inputs that resolve to the same hash, ensuring data integrity. Although advances in computational power raise eyebrows regarding vulnerabilities in older hashing algorithms, SHA-256 has largely remained unscathed due to its robust design and extensive bitlength.
Additionally, it is vital to highlight the ramifications of employing SHA-256 beyond mere data protection. Its application in blockchain technology, for example, allows for secure transactions and establishes trust in decentralized systems. When miners validate transactions, they must compute a hash that meets a specific target. This inherent challenge exemplifies the utility of SHA-256 as not just a security measure, but as a critical pillar of modern computational systems.
So, is there an “algorithm” that can reverse SHA-256? The crux of the matter is that SHA-256 functions on the principles of one-way cryptography, rendering the reversal into an impractical endeavor. The cryptographic community continues to explore advanced techniques and evolving algorithms, but reversing the landmark SHA-256 remains an impossible feat. Despite advances in quantum computing, which threaten traditional cryptographic safeguards, the current consensus maintains that SHA-256 is substantially secure against reversal attempts.
Moreover, ongoing research into alternative hashing algorithms and the development of quantum-resistant strategies illustrate the dynamic nature of cryptographic discourse. Key functions such as Argon2 and Bcrypt focus on adapting to changing paradigms, yet none propose a genuine reversal of SHA-256. Instead, they pivot towards enhancing security rather than undermining it.
Conclusively, the pursuit of reversing SHA-256 yields no fruitful avenues for attackers or cryptographers alike. Instead, it opens up a rich tapestry of discussions around data security, the limits of computational power, and the transformative potential of cryptographic advancements. As digital footprints continue to expand and evolve, so too must the integrity mechanisms that protect them. While the quest for reversal is a mirage in the cryptographic expanse, the broader understanding of SHA-256’s pivotal role in securing our digital lives remains profoundly essential.







Leave a Comment