In the expansive realm of cryptography, where the protection of sensitive data takes center stage, the intricate ballet of encryption unfolds. Among the myriad components that stitch together this tightly woven fabric of digital security, two stand out with understated yet pivotal significance: the keys and the algorithms. Each plays a crucial role, akin to the twin pillars of a grand architectural marvel, supporting the edifice of secure communications. Failure to comprehend or appreciate these components is tantamount to embarking on a voyage without a compass—rife with uncertainty and peril.
Imagine, if you will, the encryption key as a key to a treasure chest buried deep within the sands of time. This key is not only essential to unlock the chest but is also unique to its specific lock. In cryptographic terms, a key is a piece of information that determines the output of a cryptographic algorithm. It is an integral element, an enigmatic token that, when paired with the correct algorithm, can obfuscate the meaning of data, converting it into a seemingly nonsensical string of characters. Without the right key, the encoded data remains an inscrutable riddle, a cipher that taunts any who would attempt to decipher its secrets.
The relationship between the key and the data can be illustrated through a vivid metaphor. Consider a symphony orchestra where the encryption algorithm serves as the conductor. The conductor, through varied gestures and movements, brings the musicians into harmony, guiding them to produce a melodious rendition of a composition. The encryption key, in this analogy, represents the individual musicians, each bringing their unique sound, yet harmonizing beautifully under the conductor’s guidance. Each note sung by the musicians is akin to encrypted data, understandable only to those who possess the conductor’s score—the key.
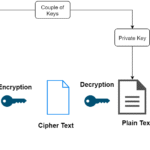
Unveiling the nuances of keys leads us to an important distinction: symmetric and asymmetric encryption. Symmetric encryption utilizes a single key for both encryption and decryption. This method, while efficient and fast, carries the inherent risk of key exchange. Should the key fall into the wrong hands, the guardian of the data stands vulnerable, akin to leaving a treasure map lying about for just anyone to find. The challenge, therefore, is to protect this key during transmission and storage, ensuring it remains in the hands of the rightful owner.
Conversely, asymmetric encryption bifurcates this relationship by employing a pair of keys: a public key and a private key. The public key acts like a lock that anyone can use to secure a message intended for the owner of the private key, who alone has the means to unlock it. This method enhances security, as the public key does not need to be kept secret, allowing for safer communications over open channels. However, the complexity of managing two keys can be daunting, creating a tapestry of logistical challenges that security professionals must navigate.
Next, we transition to the algorithms—the intricate recipes that govern the process of encryption. These algorithms, which include the likes of Advanced Encryption Standard (AES), Rivest Cipher (RC4), and the Data Encryption Standard (DES), weave the cryptographic magic that enshrouds our data. The robustness of an algorithm determines how effectively it can withstand attacks from adversaries, who are constantly probing for vulnerabilities, seeking to exploit weaknesses.
Algorithms can be imagined as the locksmiths of the digital world. Each locksmith brings a unique set of tools, honed through experience and innovation. A reliable locksmith can craft secure, intricate locks capable of withstanding an onslaught of breaking and entering attempts. Similarly, a strong encryption algorithm must remain resilient against cryptographic attacks, such as brute force attempts, where adversaries systematically try all possible keys, hoping to stumble upon the right one.
Yet, it’s not merely the strength of the algorithms that warrants attention but also their operational efficiency. In an age where speed and accessibility reign supreme, an algorithm must encode and decode data quickly without compromising its security. The efficiency of the algorithm resembles the brisk tempo of a well-rehearsed orchestra, delivering a performance that captivates the audience while ensuring every note is played flawlessly.
As we delve deeper into this cryptographic labyrinth, we discover that the interplay between keys and algorithms is both symbiotic and essential. While the strength of a key dictates the potency of an encryption, the robustness of an algorithm shapes how efficiently that key can pulse through the veins of data, securing it against prying eyes. A relationship entrenched in trust yet fraught with risks, the collaboration of these two elements forms the bedrock of our digital security landscape.
In a world increasingly driven by data, the importance of understanding encryption’s basic components cannot be overstated. Keys serve as the guardians, while algorithms act as the vigilant sentinels, tirelessly working to protect our most sensitive information. Ignoring these components is to sail the turbulent seas of the digital age unprepared, veering off course into treacherous waters populated by data pirates and surveillant entities.
In conclusion, embracing the duality of keys and algorithms within encryption is essential for anyone striving to protect their digital treasures. Like the intricate gears of a well-crafted clock, they work together to keep time—securely and efficiently guarding our secrets. Grasping this relationship not only fortifies defenses but also empowers you to navigate the complexities of modern cryptography with confidence, illuminating the path toward a more secure digital future.






Leave a Comment