In the digital age, where our interactions are increasingly mediated by the internet, the integrity and confidentiality of data have become paramount. This concern propels discussions around Transport Layer Security (TLS) and its role in mitigating Man-in-the-Middle (MITM) attacks. What if I told you that while encryption may bolster your online security, its efficacy depends not only on its existence but also on its implementation? This consideration poses a puzzling challenge: how effective are our defenses against these increasingly sophisticated intrusion attempts?
Let’s begin by dissecting what TLS is and how it operates. TLS is a cryptographic protocol designed to provide end-to-end security for internet communications. It encrypts the data transmitted between a client and a server, ensuring that even if intercepted, the information remains incomprehensible to unauthorized individuals. By utilizing a combination of asymmetric and symmetric encryption, TLS secures the channels through which sensitive data travels — be it credit card information during an online purchase or personal messages between friends.
Encryption relies primarily on two key mechanisms: public key infrastructure (PKI) and session keys. In the initial stage, PKI establishes a secure exchange of authentication credentials. This system generates a pair of keys: a public key, which can be disseminated freely, and a private key, which is kept secret by the server. When a client wishes to establish a secure connection, it uses the server’s public key to encrypt a session key. This session key provides symmetric encryption for the duration of their interaction, enabling faster data transfer while maintaining security.
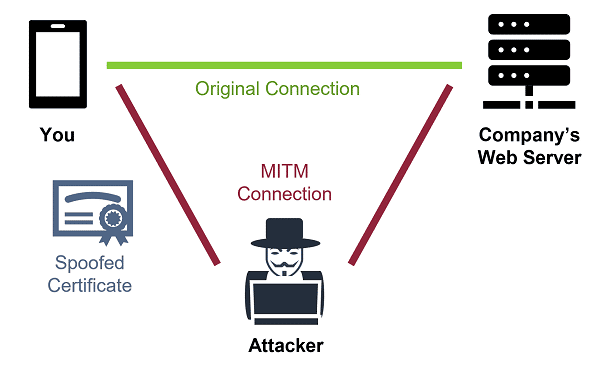
Despite TLS’s robust architecture, vulnerabilities still exist, particularly regarding MITM attacks. In a standard MITM scenario, an assailant intercepts the communication between the client and server. They can eavesdrop on the data transmitted or even manipulate the messages being exchanged, masquerading as the legitimate entities. Imagine typing your credit card number into a website, only to find that you gave it not to the retailer but to an unknown hacker. Such scenarios emphasize the critical role of validation certificates and the importance of a secure connection indicator, such as HTTPS.
However, beneath the appealing facade of encryption lies a cavalcade of intricacies. Users often overlook the procedural protocols surrounding TLS implementation. For instance, if a website lacks a valid TLS certificate, or if the browser warns users about potential security issues, complacency may lead individuals to disregard these alerts. This negligence is fertile ground for the opportunistic tactics employed in MITM attacks. An awareness of these concerning realities obliges us to question: Are we truly vigilant when it comes to our online security?
Mitigating MITM attacks necessitates adopting best practices beyond mere encryption. Regular updates to software and security protocols can help shield networks from exploitation. Additionally, employing multi-factor authentication (MFA) can serve as an extra layer of protection. By requiring users to verify their identity through another channel—such as a text message or email—MFA significantly diminishes the likelihood of unauthorized access. Yet, in a world replete with cyber threats, one must ponder: how many users will consider these additional steps necessary?
Furthermore, the advent of public Wi-Fi networks introduces another layer of complexity to the TLS equation. While these networks offer convenience, they are also notoriously insecure. An unprotected Wi-Fi connection can provide a fertile hunting ground for cybercriminals who may initiate MITM attacks while users engage in everyday online activities. Given this reality, it is prudent to consider: when using public networks, how often do users prioritize a secure connection?
Despite the presence of these challenges, advancements in TLS continue to evolve. Modern protocols like TLS 1.3 have strengthened defenses against potential exploits. By streamlining the handshake process and reducing the number of round-trips required to establish a secure connection, TLS 1.3 enhances both speed and security. This upgrade counteracts several known vulnerabilities, including those associated with downgrading attacks, where a perpetrator forces a connection to revert to a less secure version of the protocol. Yet the question remains: are we fully harnessing the capabilities of these advanced protocols across all platforms?
Ultimately, while TLS provides a formidable line of defense against MITM attacks, its mere existence is insufficient. The onus lies on end-users, developers, and organizations alike to foster a culture of awareness. Bolstering cyber hygiene—consciously practicing secure behaviors online—is vital to thwart the incessant efforts of malicious actors. Initiatives around education and awareness can play a pivotal role in cultivating this culture, preparing everyday individuals to recognize the signs of potential threats.
In conclusion, the interplay between TLS, encryption, and the omnipresent threat of MITM attacks underscores a vital narrative about digital security. It calls upon us to remain constantly vigilant and proactive. In an age rife with cyber threats, the challenge is clear: as we traverse the digital landscape, how will we ensure that the encryption we trust remains impenetrable against intrusion?







Leave a Comment