In an age where digital interactivity drives daily life, the importance of secure web traffic cannot be overstated. Enter Transport Layer Security (TLS), an advanced cryptographic protocol that forms the foundation of internet security. It stands as a guardian for sensitive communications, ensuring that data transmitted across the web retains its confidentiality, integrity, and authenticity. In this exploration, we dissect the multifaceted dimensions of TLS cryptography and its indispensable role in establishing secure connections in the digital landscape.
The Emergence of TLS
Initially conceived as a means to protect communications, TLS evolved from an earlier protocol known as Secure Sockets Layer (SSL). SSL, while groundbreaking during its inception, exhibited several vulnerabilities that underscore the necessity for refinement. As cryptographic expertise burgeoned, TLS emerged as its successor, introducing enhanced security mechanisms to thwart threats and bolster user trust. Today, TLS finds itself ubiquitous—securing protocols such as HTTPS, securing email communications, and even safeguarding file transfers.
The Triad of Security: Confidentiality, Integrity, and Authentication
TLS cryptography adeptly encapsulates three core principles: confidentiality, integrity, and authentication. Each pillar is critical in nurturing a secure online environment.
- Confidentiality: The sanctum of privacy is paramount. TLS employs encryption algorithms that obscure data during transit. This ensures that even if data packets are intercepted, their contents remain indecipherable to unauthorized entities. Advanced ciphers such as AES (Advanced Encryption Standard) and ChaCha20 are frequently employed to provide robust encryption, maintaining the secrecy of sensitive information such as passwords and credit card numbers.
- Integrity: The sanctity of data must be preserved throughout its journey across networks. TLS incorporates cryptographic hash functions—such as SHA-256 (Secure Hash Algorithm) and HMAC (Hash-based Message Authentication Code)—to ensure data integrity. By generating unique hash values for transmitted data, any alterations en route can be identified, enabling parties to detect tampering or corruption.
- Authentication: Establishing the identity of communicating parties is a cornerstone of trust. TLS employs digital certificates, issued by trusted Certificate Authorities (CAs), to authenticate server identities. This cryptographic mechanism ensures that users are not unwittingly communicating with imposters, thus mitigating the risk of man-in-the-middle attacks.
The TLS Handshake: A Masterclass in Coordination
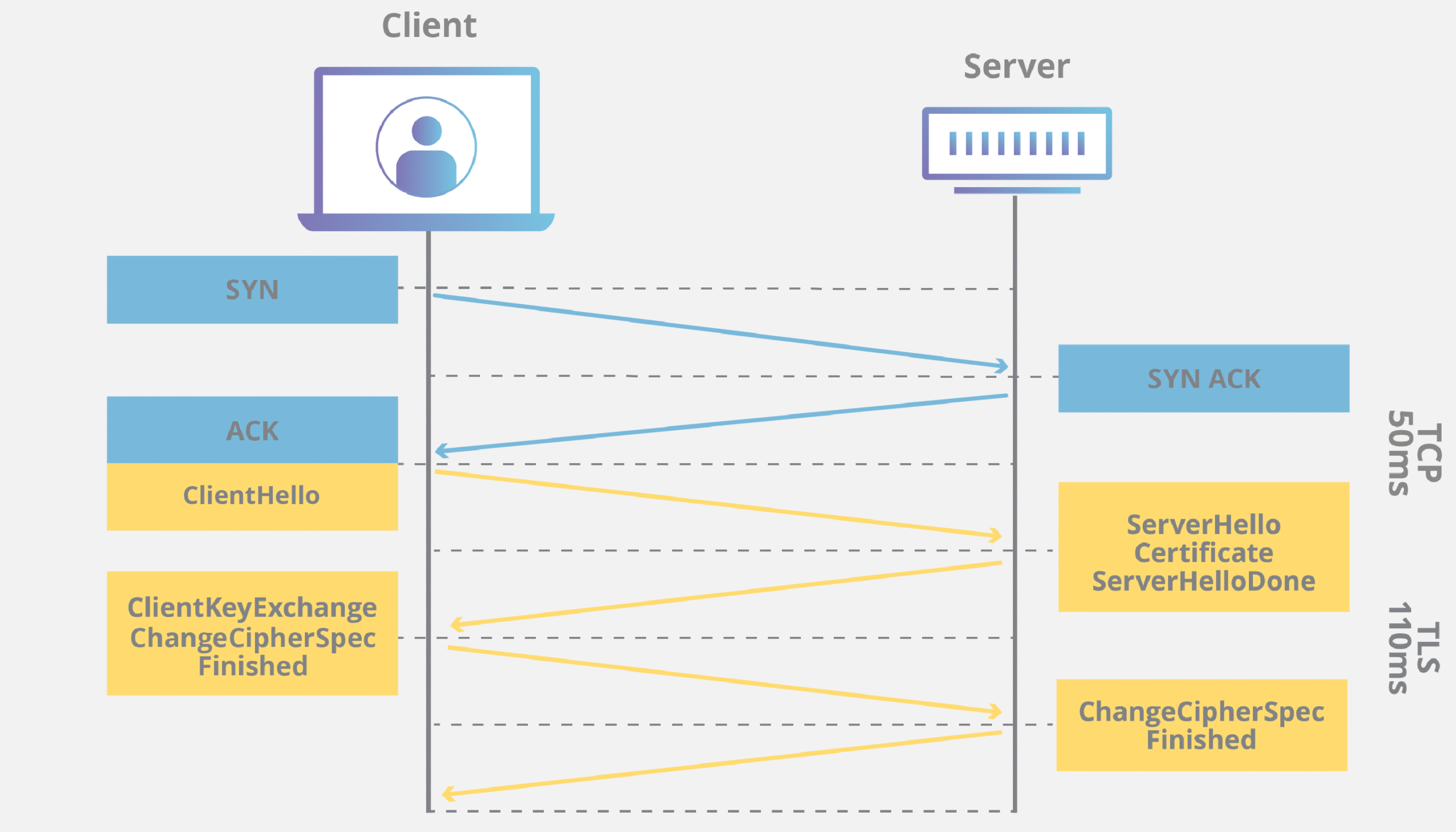
One of the most fascinating aspects of TLS is its handshake process. This intricate series of steps orchestrates the establishment of a secure connection and involves multiple phases:
- Client Hello: The process begins when a client (e.g., a web browser) sends a greeting to the server. This ‘Client Hello’ message outlines the version of TLS it supports, the cipher suites available, and a randomly generated number.
- Server Hello: In response, the server acknowledges with a ‘Server Hello’ message, confirming the chosen TLS version and cipher suite while also sending its own random number. At this juncture, the server also provides its digital certificate to authenticate its identity.
- Key Exchange: Once the identity is established, the two parties engage in a key exchange, which solidifies the shared secret necessary for encryption. Different methods, such as Diffie-Hellman or Elliptic Curve Diffie-Hellman, may be employed for this process.
- Finished Messages: Subsequently, both client and server will communicate finished messages, indicating the conclusion of the handshake. They can now commence secure data transmission using symmetric keys derived from the exchanged information.
Evolution and Current Trends in TLS
As cyber threats evolve, so too do the protocols designed to mitigate them. TLS has undergone several revisions, with TLS 1.3 being the latest iteration. This version drastically simplifies the handshake process and eliminates outdated cryptographic algorithms, thereby increasing security and performance. In a world where speed often trumps security, TLS 1.3 epitomizes a balance, reducing latency while retaining robustness.
Beyond the Basics: TLS in Practice
While understanding the theoretical underpinnings of TLS is paramount, its practical implementation is equally critical. Organizations looking to adopt TLS must navigate the realm of certificate management, ensuring that their digital certificates are valid and up to date. Failure to do so can result in warnings for end-users, eroding trust in services that rely on secure communications.
Moreover, the deployment of TLS does not exist in a vacuum. The use of HTTP/2 and other modern web protocols, such as QUIC, integrates seamlessly with TLS, enhancing performance while retaining necessary security layers. Developers and administrators must remain cognizant of the broader ecosystem, implementing stringent security practices alongside TLS to safeguard web traffic comprehensively.
Conclusion: The Unyielding Backbone of Secure Communication
In conclusion, TLS cryptography is a quintessential component of internet security, empowering users to navigate the digital realm with confidence. It encapsulates a harmonious blend of scientific rigor and technical sophistication, staunchly defending against the pervasive threats lurking in cyberspace. As our reliance on digital interactions continues to deepen, the importance of adopting a secure framework cannot be understated. TLS stands resolutely at the forefront, reassuring users that their data is protected by an intricate tapestry of cryptographic principles.








Leave a Comment