Transport Layer Security (TLS) is an essential cryptographic protocol designed to provide secure communication over a computer network. The advent of TLS 1.3 marks a significant evolution in this protocol, streamlining the handshake process, bolstering encryption standards, and enhancing overall performance. However, with each advancement in encryption technology, the specter of potential vulnerabilities looms. Can attackers genuinely breach TLS 1.3? This inquiry demands meticulous scrutiny.
The cryptographic community often positions TLS 1.3 as a robust guardian against adversaries. The protocol eliminates outdated cryptographic algorithms and encryption modes, introducing modernized primitives. One pertinent feature includes the use of Authenticated Encryption with Additional Data (AEAD) modes. AEAD merges confidentiality and authenticity checks into a single operation, substantially mitigating risks associated with traditional modes of operation, such as Cipher Block Chaining (CBC).
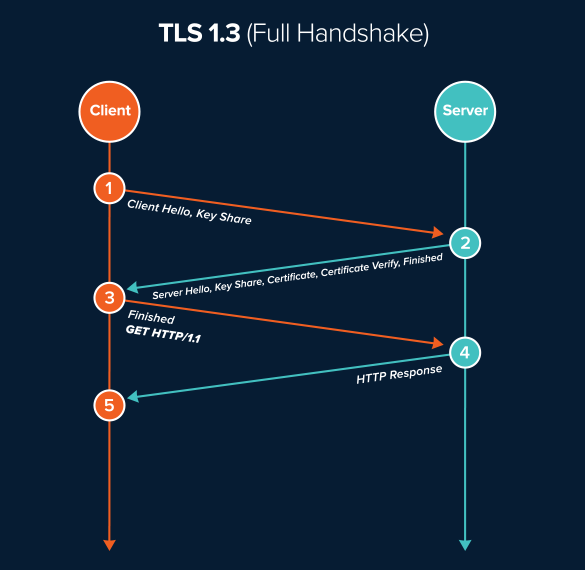
Additionally, the handshake process in TLS 1.3 has been optimized to reduce latency. By enabling zero round-trip time (0-RTT) resumption, returning clients can initiate communication with the server without the need for a full handshake, vastly improving performance. However, this innovation carries inherent risks. In scenarios where an impersonating attacker intercepts the initial communication, they might exploit replay attacks—a peril necessitating ongoing vigilance.
Another layer of complexity arises from the attack vectors prevalent in earlier TLS versions. Although improved, TLS 1.3 is not immune to sophisticated attacks. For instance, the potential for a Man-in-the-Middle (MitM) attack persists, particularly if the endpoint authentication mechanisms are compromised. Attackers may intercept communication between the client and server, manipulating data before it reaches its final destination. This possibility underscores the need for stringent verification protocols.
The conversation inevitably shifts to quantum computing—an emergent technology poised to disrupt various cryptographic schemes. Current public-key algorithms, such as RSA and elliptic-curve cryptography, underlie the security of TLS 1.3. However, the burgeoning capabilities of quantum machines threaten to unravel these traditional cryptographic constructs. Quantum algorithms, notably Shor’s algorithm, can efficiently factor large numbers, rendering RSA and similar protocols obsolete. Researchers are actively exploring post-quantum cryptographic alternatives; nevertheless, the timeline for widespread integration remains uncertain.
Moreover, the configuration of TLS 1.3 deployments can inadvertently introduce vulnerabilities. Misconfigured servers or weak cipher suites can expose data to potential breaches. Instances of lax security measures highlight the necessity for organizations to regularly audit their cryptographic implementations. Tools like automated pen-testing utilities can evaluate system resilience against known exploits.
The phenomenon of supply chain attacks also warrants attention. Attackers can compromise the software ecosystems surrounding TLS implementations. By targeting vulnerabilities in libraries or APIs integral to TLS operations, adversaries can execute covert attacks. Recent incidents have revealed such shortcomings, emphasizing the importance of maintaining vigilance across all facets of software development, from initial coding to final deployment.
Furthermore, the conversation surrounding regulatory compliance and security standards underlines the critical nature of encryption in contemporary digital architectures. Industries governed by strict regulations, such as financial services or healthcare, must adhere to rigorous security frameworks. TLS 1.3’s enhanced security features play a pivotal role in meeting these stringent standards. However, the effective implementation of these standards hinges on proper education and awareness among stakeholders.
End-user awareness is paramount. A strong encryption protocol cannot compensate for negligent user practices. For instance, an unaware user may fall prey to phishing attacks, inadvertently revealing sensitive information. Education campaigns that promote security hygiene, such as recognizing suspicious emails and employing strong, unique passwords, are vital elements in the broader strategy against cyber threats.
In conclusion, while TLS 1.3 represents a significant leap forward in the realm of secure communication, the efficacy of encryption must be continuously evaluated against emerging threats and the evolving technological landscape. Attackers may not currently possess an effortless method to penetrate TLS 1.3, but the dynamic nature of cyber threats necessitates perpetual adaptability and vigilance in cryptographic implementations. Furthermore, the responsibility to uphold security does not rest solely on the shoulders of cryptographers; it requires a collaborative effort from developers, corporate entities, and end-users alike. As we continue to traverse an increasingly interconnected world, the sanctity of data and secure communications must remain at the forefront of technological initiatives.








Leave a Comment