The story of cryptography is as old as civilization itself, filled with enigmas that have perplexed scholars and spies alike. Among these is RSA, a cornerstone of modern encryption, whose very name prompts a plethora of questions regarding its origins, functionality, and significance. What makes RSA 1024 particularly salient in discussions of information security? This article embarks on a journey through time, illuminating the intricacies of RSA while emphasizing its historical roots and its pivotal role in contemporary cryptography.
To grasp the essence of RSA, one must first traverse back to the late 20th century, a period characterized by burgeoning technological advancements and equally burgeoning security challenges. In 1977, Ron Rivest, Adi Shamir, and Leonard Adleman—three formidable computer scientists—introduced the RSA algorithm, a name derived from their initials. This revolutionary algorithm was not merely an improvement upon earlier cryptographic methods; it signified a paradigm shift in how information could be securely transmitted over public networks.
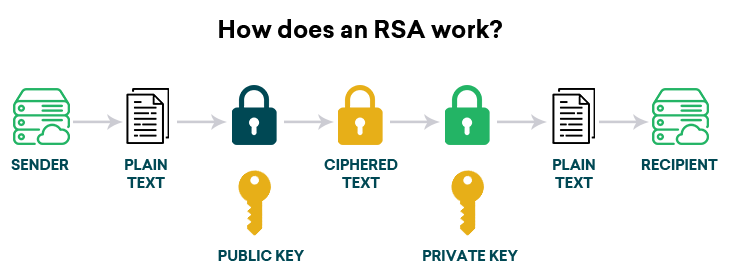
The conceptual foundation of RSA lies in the realm of number theory, a discipline that explores the intricate properties of numbers, particularly prime numbers. RSA leverages the mathematical phenomenon of factorization, challenging the notion of secrecy in the digital age. At its core, the algorithm utilizes a pair of keys: a public key for encryption, accessible to anyone wishing to send secure messages, and a private key for decryption, maintained solely by the recipient. This dual-key system is the essence of public-key cryptography, which ensures that even if a malicious actor intercepts the encrypted message, it remains indecipherable without the corresponding private key.
The question arises: Why is the number 1024 significant when discussing RSA? The numeral 1024 refers to the length of the key used in the RSA encryption process, measured in bits. A 1024-bit key may initially appear arbitrary, but its significance is underpinned by the delicate balance between security and performance. In the ever-evolving landscape of technological capabilities, the strength of a cryptographic key is paramount. The greater the key length, the more formidable the challenges an adversary faces when attempting to breach the encryption. A 1024-bit key was considered adequately secure for many years, especially during an era when computational power was significantly less potent than it is today.
However, as computational advancements gathered momentum, the security afforded by 1024-bit keys began to wane. The advent of powerful machines and sophisticated algorithms ushered in a new chapter in the arms race between cryptographers and hackers. This prompted the cryptographic community to advocate for longer key lengths. Consequently, 2048-bit and even 4096-bit keys emerged as the new standards for secure communications, rendering 1024-bit keys increasingly obsolete. The shift underscores a fundamental tenet in cryptography: the perpetual cat-and-mouse game between those safeguarding information and those attempting to compromise it.
Yet the historical significance of RSA 1024 transcends its vector of security. Its development was emblematic of a broader trend toward democratization in cryptography. Prior to RSA, encryption methods were predominantly confined to military and government agencies. RSA propelled the concept of secure communication into the realm of civilians and corporations, forever altering the landscape of electronic communication. The algorithm not only facilitated the rise of secure e-commerce and online banking but also laid the groundwork for secure communications that permeate our lives today.
Moreover, RSA’s influence resonates beyond the confines of its algorithmic prowess. It has become a symbol of the intricate relationship between mathematics and computer science. The underlying principles of RSA have inspired a vast array of subsequent cryptographic innovations, enriching the tapestry of encryption with diverse methodologies. Variants and successors bearing testimony to RSA’s enduring legacy have emerged, expanding its foundational concepts while ensuring that secure communication is accessible and robust.
Yet, with great innovation comes great responsibility. The implementation of RSA and its successors necessitates an acute awareness of socio-political dynamics. The balance of encryption strength and regulatory oversight poses philosophical questions regarding privacy, security, and the role of technology in society. As stakeholders grapple with these dilemmas, the conversation surrounding RSA continues to evolve, reflecting the public’s growing concerns over digital privacy and security.
Looking to the future, one must ponder: What does the evolution of RSA signify for upcoming generations of cryptographic algorithms? As advancements in quantum computing loom on the horizon, the very foundation of traditional cryptography may be called into question. Quantum computers, capable of performing computations at incomprehensible speeds, threaten to dismantle the security promised by RSA and similar algorithms. This impending quantum era signals a tumultuous juncture, necessitating innovations that transcend current methodologies.
In conclusion, the origins of RSA and the relevance of 1024-bit keys invite intrigue and contemplation. More than just a cryptographic algorithm, RSA represents a convergence of mathematics, computer science, and societal shifts—an emblem of empowerment in an interconnected world. The journey of RSA illustrates both the triumphs and trials of securing information, providing a lens through which we can view the complexities of modern cryptography. As we forge ahead, the legacy of RSA serves as a reminder that the pursuit of secure communication is an ever-evolving endeavor, requiring constant vigilance, innovation, and a deep understanding of the implications that accompany technological advancement.







Leave a Comment