In the intricate realm of cryptography, encryption algorithms serve as the cornerstone for securing digital information. This extensive discourse examines various encryption algorithms, categorizing them into three distinct segments: the good, the bad, and the broken. Each type of algorithm is explored in a manner that unveils both its strengths and vulnerabilities, providing a comprehensive lens through which to assess their practicality and reliability in safeguarding data.
The Good: Robust Encryption Protocols
The “good” algorithms represent the pinnacle of security in cryptographic standards, designed to withstand prying eyes while ensuring the confidentiality and integrity of data.
AES (Advanced Encryption Standard)
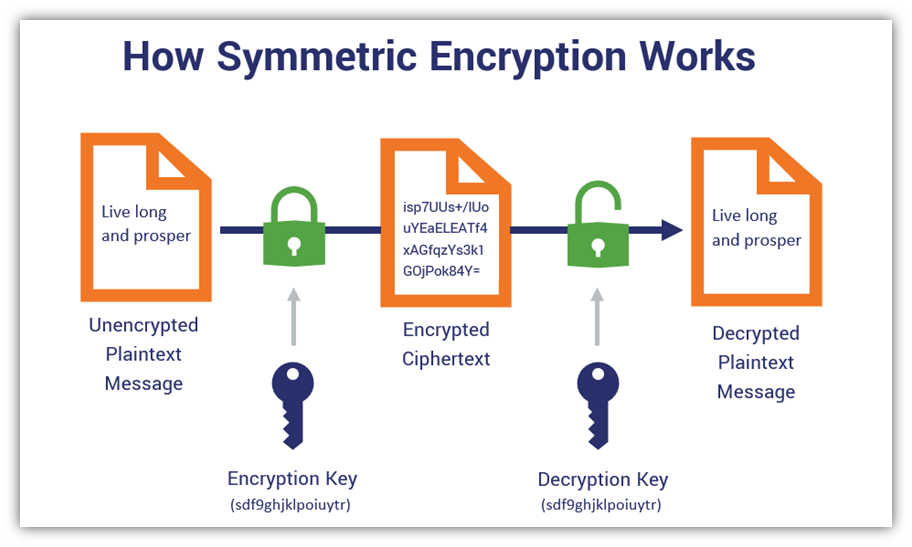
Firstly, there is the Advanced Encryption Standard (AES), which has become the gold standard in symmetric encryption. AES employs block ciphers that encrypt data in fixed-size blocks, typically 128 bits. Its versatility allows for key sizes of 128, 192, or 256 bits, corresponding to various security requirements. The algorithm’s exhaustive structure ensures that brute-force attacks are virtually infeasible, particularly when utilizing larger key sizes. The National Institute of Standards and Technology (NIST) recommended AES after an extensive evaluation process, affirming its resilience against cryptanalytic attacks.
Furthermore, the widespread adoption of AES across various industries—from financial institutions to government agencies—highlights its reliability. AES’s efficiency in both software and hardware implementations adds another layer of appeal, as it performs exceptionally well on a range of devices without compromising security.
RSA (Rivest-Shamir-Adleman)
Next in the lineup is the RSA algorithm, a cornerstone of asymmetric encryption frequently employed for secure data transmission and digital signatures. RSA’s foundation lies in the mathematical intricacies of prime factorization; its security hinges on the difficulty of decomposing a large composite number into its prime constituents. Unlike symmetric algorithms, RSA utilizes a pair of keys: a public key for encryption and a private key for decryption.
What sets RSA apart is its ability to facilitate secure communications over untrusted networks, making it a popular choice for SSL/TLS protocols that underpin websites’ security. Despite its computational intensity, RSA remains integrated into many cryptographic systems due to its robust security characteristics and the ease with which it enables key exchange.
Elliptic Curve Cryptography (ECC)
Further enhancing the landscape of secure encryption is Elliptic Curve Cryptography (ECC), which offers a powerful alternative to traditional methods like RSA. By leveraging the mathematical properties of elliptic curves over finite fields, ECC provides equivalent security with significantly smaller keys. This compactness makes ECC highly efficient, especially in environments where computing resources or bandwidth is limited.
Its rise in popularity, particularly in mobile devices and IoT applications, stems from its ability to provide strong security without taxing system resources. The allure of ECC promises streamlined operations without sacrificing encryption integrity, establishing it as a formidable contender in modern cryptography.
The Bad: Algorithms Failing to Meet Current Standards
DES (Data Encryption Standard)
Data Encryption Standard (DES) is a prime example of an algorithm that has steadily declined in relevance. Originally adopted as a federal standard in the 1970s, DES utilizes a 56-bit key, which, given today’s computational capabilities, is laughably inadequate. The encryption process employs a Feistel network, which, while innovative at the time, has been rendered vulnerable due to advancements in cryptanalysis and brute-force attack techniques that can crack DES in a matter of hours.
Consequently, DES has been largely phased out in favor of more secure algorithms such as AES. Nonetheless, its historical significance in the cryptographic landscape cannot be overlooked, as it set the stage for future developments in encryption technology.
3DES (Triple DES)
In response to DES’s vulnerabilities, Triple DES (3DES) was introduced to bolster security by applying the DES algorithm three times with different keys. However, while it significantly enhances security over its predecessor, 3DES suffers from the same fundamental drawbacks—sluggish performance and susceptibility to specific types of attacks. As a result, its use is being deprecated, with security experts recommending the transition to more efficient algorithms.
The Broken: Algorithms That Should Be Avoided
Even more disconcerting are algorithms that are fundamentally flawed, rendering them dangerous choices for securing information. These algorithms exhibit severe vulnerabilities that should preclude any practical application.
RC4
RC4 is a stream cipher that, despite enjoying widespread use in its heyday, has been deemed broken due to devastating cryptographic flaws. Vulnerable to various attacks, including biases in the generated keystream, RC4 is no longer considered a viable option for securing sensitive data. Major protocols like SSL and WEP have consequently withdrawn support for RC4, urging developers to seek more secure replacements.
WEP (Wired Equivalent Privacy)
Wired Equivalent Privacy (WEP) was designed to provide a secure wireless network. However, due to numerous weaknesses in its key management and encryption processes, WEP has been rendered obsolete. Attacks against WEP can occur in mere minutes, leading to widespread acknowledgment of its inadequacy. As a result, it has been replaced by more secure standards such as WPA2 and WPA3, which employ stronger encryption methods and more robust protection against unauthorized access.
Conclusion
In summation, understanding the landscape of encryption algorithms is paramount for individuals and organizations alike in ensuring the confidentiality and integrity of their data. The good algorithms, characterized by their robustness and widespread acceptance, pave the way for secure communications. The bad algorithms, while still in existence, exemplify the necessity for ongoing vigilance and progression within the field of cryptography. Ultimately, the broken algorithms are stark reminders of the importance of continual evolution in security practices, as technology rapidly advances alongside potential threats.








Leave a Comment