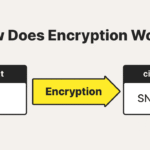
Encryption, a practice as ancient as written communication itself, serves as the bedrock of modern data security. It encompasses various techniques that transform understandable information into a format that is unrecognizable to unauthorized users. Throughout history, encryption has continually evolved, often in response to the growing complexity of communication and the need for privacy. In this exploration, we elucidate the earliest forms of encryption and juxtapose them with contemporary methods that are still prevalent today.
The roots of encryption can be traced back to the earliest civilizations. Archeological finds reveal that the Egyptians employed hieroglyphs as a form of coded language. While not a systematic encryption technique, the use of symbols to convey hidden meanings laid foundational principles. This early form of encoding demonstrated humanity’s primal need to shield sensitive information from prying eyes.
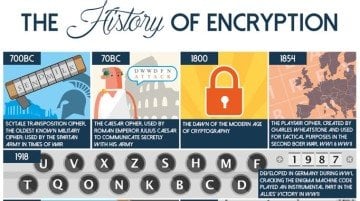
One of the most iconic forms of encryption from antiquity is the Caesar cipher, attributed to Julius Caesar. This substitution cipher involved shifting letters in the alphabet by a fixed number. For instance, with a shift of three, ‘A’ would become ‘D,’ ‘B’ would morph into ‘E,’ and so on. The simplicity of this technique made it accessible, yet its predictability rendered it vulnerable to decryption efforts—an illusory veil over the conveyed message. Despite its flaws, the Caesar cipher epitomizes the balance between ease of use and the necessity for confidentiality.
Ancient Greece also contributed to early encryption practices through the invention of the scytale, a device used by the Spartans. The scytale utilized a wooden staff around which a strip of parchment was wound. The letters would be inscribed along the length of the strip, and when unwound, the text would appear jumbled. Only a recipient with a matching staff of the same diameter could decode the message. This ingenious apparatus highlights the innovative spirit behind ancient encryption methods.
As communication extended beyond geographical confines, new encryption methodologies emerged. The Arab mathematician Al-Kindi is renowned for his work on cryptanalysis in the 9th century. He introduced frequency analysis, a technique that analyzes the frequency of letters and letter combinations in a ciphertext. This significant advancement allowed cryptanalysts to break previously steadfast ciphers by mapping letter frequency to known linguistic patterns. Al-Kindi’s contributions paved the way for future generations of cryptographers.
The Renaissance era ushered in a wave of sophisticated encryption techniques. One notable innovation was the Vigenère cipher, which employed a polyalphabetic substitution method. It utilized a keyword to determine the shifting of letters, making it significantly more secure than earlier techniques. However, even the Vigenère cipher succumbed to the analytical prowess of cryptanalysts, showcasing the perpetual arms race between encryption and decryption. The interplay between the two disciplines shaped the clandestine world of espionage and communication, a theme that resonates through history.
Fast forward to the 20th century, and the landscape of encryption underwent a seismic shift with the advent of modern computing. Traditional ciphers were supplanted by algorithms that harnessed complex mathematical concepts. The introduction of public-key cryptography, pioneered by Whitfield Diffie and Martin Hellman in 1976, revolutionized the field. This method eliminated the need for secure key exchanges, allowing users to communicate securely via an asymmetric key pair—one public and one private. This paradigm shift represented not just an advancement in encryption mechanisms, but also a profound transformation in societal communication structures.
Fast becoming a staple in everyday life, the Advanced Encryption Standard (AES) emerged as the gold standard for securing digital data. Adopted by the U.S. government in 2001, AES employs symmetric key encryption, meaning that the same key is used for both encryption and decryption. Its robustness and efficiency have led to widespread use across various applications, from secure banking to safeguarding sensitive governmental communications. The algorithm’s resilience against brute-force attacks ensures a level of security that meets the demands of a data-driven age.
As we analyze this historical tapestry of encryption, it is compelling to observe the continuity of encryption principles across epochs. The techniques first developed millennia ago laid the groundwork for the intricacies of today’s encryption practices. However, the dynamic nature of technology means that new challenges continually arise. The burgeoning field of quantum computing poses a threat to conventional encryption methods, inspiring ongoing innovation and the urgent necessity for quantum-resistant algorithms.
Furthermore, the importance of ethical considerations in encryption cannot be overstated. As encryption technology becomes more sophisticated, so too do the exploits of those with nefarious intentions. The double-edged sword of encryption raises philosophical questions about privacy, security, and the public interest. Debates surrounding encryption backdoors, intended to allow law enforcement access to secure communications, illustrate the ongoing tension between security and liberty, a dialogue that is as ancient as encryption itself.
In summary, the journey of encryption from rudimentary hieroglyphs to formidable modern algorithms illustrates the relentless human endeavor to secure information. Techniques that have evolved, adapted, and transformed stand testament to a continual quest for privacy and security in an increasingly interconnected world. The exploration of historical methods and their contemporary counterparts reveals the intricate dance between innovation and vulnerability—a narrative that will undoubtedly persist as we traverse the uncertain future of digital communication.





Leave a Comment