Mathematical cryptography is a robust field that underpins the security of modern digital communications. By employing rigorous mathematical principles, cryptographers can design systems that protect information from unauthorized access. This article delves into the foundational aspects of mathematical cryptography, elucidating key concepts and techniques while emphasizing their importance in the contemporary world.
At its core, cryptography is the art of encoding and decoding messages. Historically, it has evolved from simple ciphers to intricate algorithms that involve complex mathematical structures. The necessity for secure communication has birthed various types of cryptographic systems, each serving distinct purposes. We shall explore symmetric and asymmetric encryption, hash functions, digital signatures, and the breadth of their applications.
The first fundamental distinction in cryptographic methods is between symmetric and asymmetric encryption. Symmetric encryption, as the name implies, uses the same key for both encryption and decryption. This method is efficient and quick, making it suitable for encrypting large amounts of data. Notable symmetric encryption algorithms include the Advanced Encryption Standard (AES) and the Data Encryption Standard (DES). These algorithms utilize various mathematical routines and bit manipulations that transform plaintext into ciphertext, rendering it unreadable without the secret key.
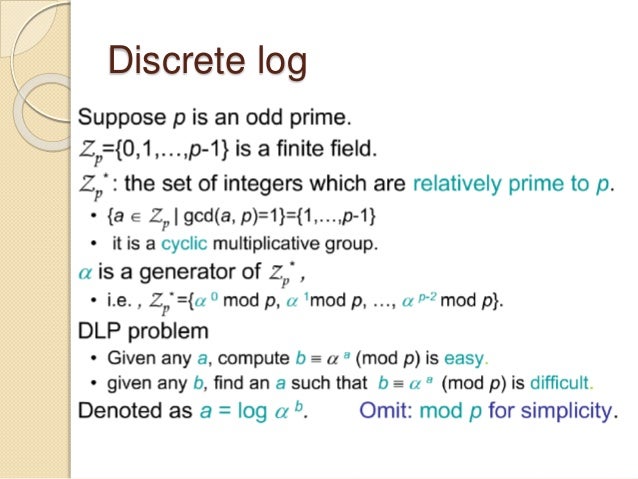
Conversely, asymmetric encryption, known as public-key cryptography, employs a novel approach that uses a pair of keys: a public key, which can be widely disseminated, and a private key, which must be kept secure. The wondrous property of this method is that data encrypted with the public key can only be decrypted by the corresponding private key. This mechanism relies heavily on mathematical problems such as integer factorization and the discrete logarithm problem, which are computationally intensive to solve without the private key. Prominent algorithms in this category include RSA and Elliptic Curve Cryptography (ECC), both of which are foundational to secure online communications and transaction verification.
A vital component of cryptography is the hash function, a mathematical function that transforms an input (or ‘message’) into a fixed-length string of characters, which is typically a digest that appears random. Hash functions play a critical role in ensuring data integrity. When data is sent over a network, the hash value can be computed and transmitted alongside the data. The recipient can then compute the hash value of the received data and compare it against the transmitted hash. If both values match, the data is deemed unchanged. Cryptographic hash functions, such as SHA-256 (Secure Hash Algorithm), provide specific properties like pre-image resistance and collision resistance, ensuring that it is computationally prohibitive to revert the hash to its original input or find two different inputs that produce the same hash.
Additionally, digital signatures are an amalgamation of the concepts of asymmetric encryption and hash functions. They function analogously to handwritten signatures, providing authenticity and non-repudiation to digital messages. To create a digital signature, the sender first generates a hash of the message, then encrypts this hash with their private key. The resulting signature can be verified by anyone with knowledge of the sender’s public key, thus confirming both the sender’s identity and the message’s integrity. This technique is instrumental in various applications, notably in software distribution, financial transactions, and electronic contracts.
Mathematical cryptography is not just an array of algorithms and functions; it manifests a profound influence over our digital interactions. Online banking, e-commerce, and private communications hinge on these cryptographic principles. For instance, when browsing the internet, many websites use HTTPS, which amalgamates Transport Layer Security (TLS) protocols, relying on cryptographic techniques to secure data exchanged between the user’s browser and the web server. The presence of a padlock icon signifies that the data transmitted is protected through mathematical encryption, ensuring confidentiality and privacy.
However, implementing cryptographic systems is merely the beginning. The ongoing challenge is to safeguard against ever-evolving threats posed by cyber adversaries. As computational power increases, particularly with advancements in quantum computing, certain algorithms that are currently deemed secure may become vulnerable. This foresight has led to the burgeoning field of post-quantum cryptography, which strives to develop algorithms resistant to quantum attacks.
As we navigate this digital age, maintaining a principled understanding of mathematical cryptography remains essential. It fosters a robust framework that not only secures personal transactions but also upholds national security in an increasingly connected world. The continuous advancement of mathematical theories and technological implementations showcases the dynamic nature of this domain, challenging cryptographers to innovate perpetually.
In summary, the basics of mathematical cryptography encompass a rich tapestry of concepts, from symmetric and asymmetric encryption to hashing and digital signatures. The interplay of these mechanisms ensures secure communication, protects data integrity, and enhances individual privacy. As we delve deeper into the intricacies of cryptographic applications, it becomes increasingly clear that mathematical cryptography is not merely a technical discipline; it is a cornerstone of trust in our information-saturated reality.







Leave a Comment