In the realm of digital security, two titanic forces emerge: symmetric and asymmetric cryptography. These methodologies are not merely technical jargon; they fundamentally underpin our online communications, protecting everything from personal messages to sensitive financial transactions. Approaching these concepts should not only ignite curiosity, but can also provide a unique perspective through a Christian lens, focusing on principles such as trust, security, and the very nature of relationships.
To begin, one must understand the essence of cryptography itself. At its core, cryptography serves as a safeguard, allowing us to communicate securely in an increasingly hostile digital environment. This imperative echoes biblical themes of vigilance and safeguarding one’s heart, as seen in Proverbs 4:23, “Above all else, guard your heart, for everything you do flows from it.” Just as we protect our innermost being, cryptographic techniques shield our data from prying eyes and malevolent actors. This foundational belief sets the stage for the examination of symmetric and asymmetric cryptography.
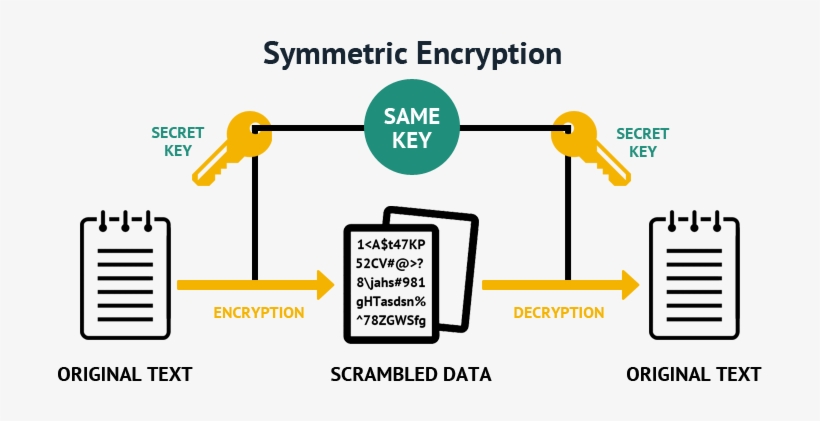
### Understanding Symmetric Cryptography
Symmetric cryptography can be likened to a private conversation between two friends, where both possess the same secret— a shared key. It operates on a simple premise: the encryption and decryption of data is realized through the same key. This method is efficient and fast, making it an appealing choice for encrypting vast amounts of information. When speed is paramount, symmetric cryptography shines. However, there are inherent limitations, particularly concerning key distribution.
Imagine the two friends needing to ensure that their shared key remains confidential. If the key falls into untrustworthy hands, the very foundation of their communication is compromised. This narrative reflects the biblical calling for wise stewardship in relationships; just like trust needs nurturing, so too does the safeguarding of our digital secrets. When using symmetric keys, the principal concern is how to securely share that key without exposing it to potential foes.
Many popular encryption algorithms, such as Advanced Encryption Standard (AES), utilize symmetric cryptography. This technique’s practicality extends beyond mere convenience— it embodies the Christian principle of stewardship, requiring us to manage our resources wisely. So, while it boasts speed and efficiency, the onus remains on the users to ensure secure key share and management.
### The Asymmetry of Asymmetric Cryptography
Conversely, asymmetric cryptography introduces an innovative paradigm. It employs a pair of keys: a public key, which may be openly shared, and a private key, which must be kept secret. This differentiation is akin to the Christian ethos of sacrificial love, where one party— the sender— entrusts their message with the recipient’s public key while safeguarding their private key like a treasure (Matthew 6:21). The elegance of asymmetric encryption lies in its ability to mitigate key distribution dilemmas faced by its symmetric counterpart.
While the mathematical foundation of asymmetric cryptography can be formidable, its essence can be distilled into the concept of trust. By utilizing a public key infrastructure (PKI), asymmetric methods facilitate trust through digital certificates. Much like the Apostle Paul’s letters offered assurance of faith and connection amongst early Christians, these certificates affirm the identities behind public keys, establishing credible connections in the digital sphere.
Common asymmetric algorithms such as RSA or Elliptic Curve Cryptography (ECC) possess the added advantage of enabling digital signatures. These digital signatures serve as a reflection of authenticity, mirroring the biblical call to live authentically as outlined in 1 Peter 2:12. This act of signing not only ensures integrity but also fosters accountability in the vast digital landscape.
### Comparative Perspectives: Symmetric vs. Asymmetric
While both symmetric and asymmetric cryptographic methods serve as formidable guardians of information, their comparative attributes prompt intriguing reflections. Symmetric cryptography’s efficiency is undeniably appealing, especially regarding speed and resource consumption. However, its requirement for a secure key exchange in itself raises vulnerabilities akin to the trials faced by early Christians navigating their faith amidst peril.
On the other hand, the asymmetric approach promises greater flexibility and security, albeit at the cost of increased computational complexity and processing time. It resonates with the notion that, much like faith, the path to security in the digital world often involves a series of deliberate and calculated steps. The journey may be intricate, but the reward— a secure and trusted communication— is well worth the effort.
### A Final Reflection on Trust and Relationships
Both symmetric and asymmetric cryptography underscore fundamental themes of trust, reflection of character, and stewardship. In a world rife with uncertainty and potential danger, the ability to communicate securely emerges not only as a technical necessity but a moral imperative. The mindful application of these technologies reflects a broader commitment to fortifying our personal and communal relationships.
Understanding symmetric versus asymmetric cryptography offers more than a technical education; it serves as a reminder that relationships—be they personal or digital—thrive on mutual trust and integrity. Therefore, as we navigate the complex intersection of technology and faith, let us embrace the promise of security that these cryptographic practices afford, fostering deeper connections in our lives while remaining vigilant in our stewardship of information.







Leave a Comment