In the realm of cryptography, the distinction between symmetric ciphers and digital signatures is pivotal yet often enigmatic. How do these cryptographic mechanisms synthesize to ensure confidentiality and authenticity of information? As we delve into the intricacies of symmetric ciphers and signing processes, we unveil a fascinating interplay of algorithms, keys, and functions that fortify our digital communications.
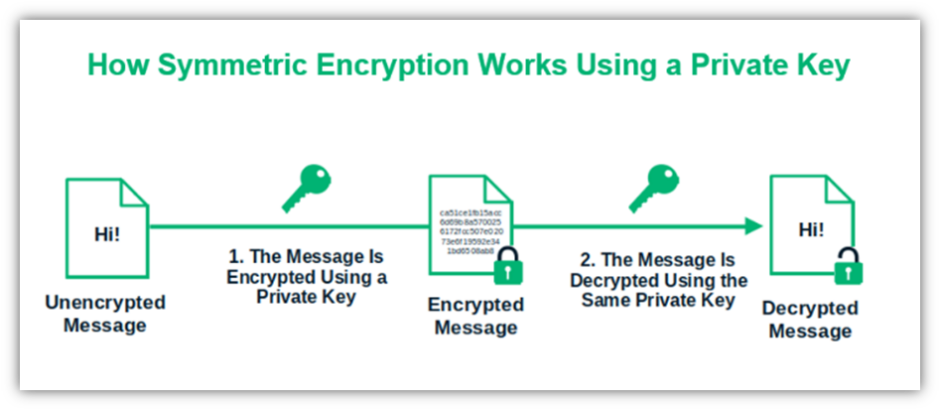
At the heart of symmetric encryption lies the concept of a secret key. A symmetric cipher is defined by a simple yet powerful characteristic: the same key is utilized for both encryption and decryption. This duality raises an intriguing question—if the same key is shared for access, how can one ensure that it remains secure? The challenge of key management poses a formidable obstacle in symmetric cryptography. In the ideal scenario, both parties need to possess the key while mitigating the risk of unauthorized access. Without vigilant safeguards, the very cornerstone of confidentiality becomes compromised.
Symmetric ciphers operate using mathematical algorithms designed to convert plaintext into ciphertext by applying a secret key. Popular symmetric algorithms include Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Triple DES (3DES). Each algorithm employs distinct methodologies to obfuscate data, yet they all share the commonality of relying on a secret key to reverse the encryption process. The substitution and transposition techniques inherent in these algorithms introduce layers of complexity that deter unauthorized deciphering attempts.
Consider the significance of key length. In cryptography, longer keys are synonymous with enhanced security. A 128-bit key provides a substantially larger key space compared to a 56-bit key, rendering brute-force attacks impractical within a reasonable timeframe. However, as computational power exponentially increases, the threshold for what constitutes a formidable key is continually re-evaluated. This relentless evolution underscores the necessity for ongoing advancements in cryptographic methods.
The introduction of symmetric ciphers brings forth the concept of digital signatures—a critical mechanism for authenticating the origin and integrity of digital messages. Digital signatures harness asymmetric cryptography, which employs a pair of keys: a public key for encryption and a private key for decryption. This bifurcation allows the sender to create a signature by encrypting a hash of the message with their private key. The recipient, upon receiving the message, can verify its authenticity by decrypting the hash with the sender’s public key. The immutable nature of hash functions ensures that any alteration to the message will result in a mismatch during verification, thereby preserving the authenticity and integrity of the original content.
Let’s contemplate this interaction. What if the same encryption method were deployed for both encryption and signing? Would we not simplify our cryptographic operations? However, therein lies a conundrum; using symmetric keys in digital signing diminishes the cornerstone of authenticity, as the verification process hinges on a distinct private key. The very essence of a signature is underpinned by the asymmetric cryptography paradigm, where only the holder of the private key can generate a valid signature, distinguishing them from others.
In practice, the synergy between symmetric ciphers and digital signatures unfolds in numerous scenarios. For instance, during secure transactions, symmetric encryption can be employed to encrypt the data being transmitted, while a digital signature authenticates the transaction. This dual-layered approach not only secures the data but also provides assurance regarding its source. It manifests a compelling answer to the challenge posed earlier: the meticulous management of both symmetric keys and digital signatures breeds a robust security framework capable of withstanding unrelenting cyber threats.
Furthermore, it is crucial to recognize that symmetric and asymmetric cryptography are not mutually exclusive. Rather, they can coexist in a hybrid cryptographic system, where symmetric encryption is used for bulk data transmission, while asymmetric methods are employed for securely exchanging the symmetric keys. This stratified model maximizes efficiency and scalability, addressing the limitations inherent in either method when used in isolation.
The implementation of these cryptographic methods necessitates not only technical proficiency but also a comprehensive understanding of potential vulnerabilities. Side-channel attacks, where unintended information leakage occurs, present a persistent threat capable of undermining even the most sophisticated ciphers. Thus, continuous scrutiny and refinement of cryptographic techniques are essential to fortify defenses against evolving adversarial tactics.
In closing, the landscape of symmetric ciphers and signing processes delineates a complex yet rewarding tapestry interwoven with security challenges and technological advances. By navigating the delicate balance between encryption and signing, a deeper understanding of how these mechanisms operate can emerge. As the digital era advances, the imperative to adopt and adapt these cryptographic practices remains not simply advisable but indispensable in safeguarding our information-centric realities.








Leave a Comment