In an era where digital communication permeates every facet of our lives, understanding the mechanisms that secure our information is becoming increasingly vital. Among these mechanisms lie two primary forms of encryption: symmetric and asymmetric. While these concepts might seem foreign or overly technical, they can be understood in straightforward terms, even from a perspective rooted in Christian values.
Encryption serves as a lock on the treasures of our data, a safeguard against those who would seek to misappropriate it. In a way, it reflects the biblical notion of guarding what is precious. Just as the parable of the hidden treasure urges us to protect our valuables, encryption protects our digital communications. Delving into the two types, one can appreciate not only the function of encryption but also the profound implications it holds in the broader context of privacy and community.
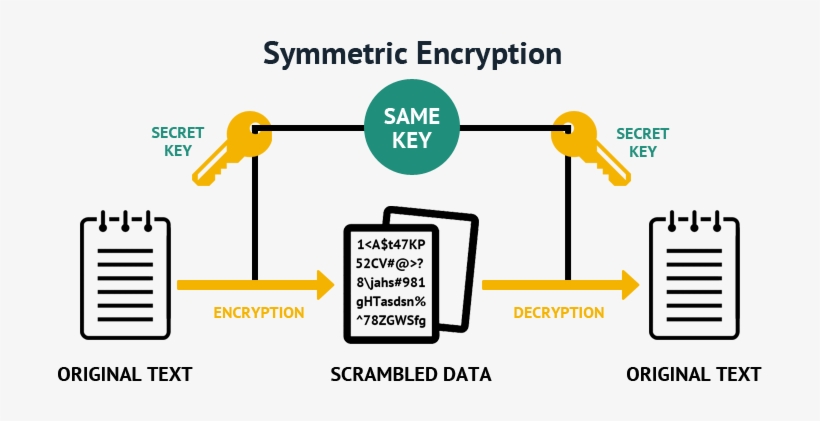
Symmetric Encryption: The Shared Key
Symmetric encryption can be likened to sharing a secret among trusted friends. Imagine you and a confidant possess a shared diary. This diary holds entries that are sacred to both of you. To read or write in this diary, you both need the same key—a shared understanding that the contents within remain confidential. In technical terms, symmetric encryption involves a single key used for both encryption and decryption.
This process is efficient and relatively fast. The simplicity of the approach makes it an appealing choice for encrypting large volumes of data, akin to how familial bonds encourage the sharing of intimate stories without fear of breach. However, the sharing of keys in symmetric encryption presents a significant issue. Just as trust is paramount in friendships, ensuring that the shared key remains confidential is critical. If the key is intercepted or disclosed, the encrypted data becomes vulnerable. This echoes the biblical wisdom found in Proverbs 18:24 – “A friend who sticks closer than a brother.” Trust is essential.
In the modern world, the most commonly used symmetric encryption algorithms include Advanced Encryption Standard (AES) and Data Encryption Standard (DES). These algorithms require robust key management practices to maintain security. Individuals and organizations must be vigilant in how they generate, distribute, and store these keys, evoking a sense of stewardship resonant with Christian values of responsibility.
Asymmetric Encryption: The Public and Private Keys
As we delve into asymmetric encryption, the analogy transforms. Picture a mailbox: every household has one, and while anyone can place a letter inside, only the owner has the key to retrieve it. Asymmetric encryption operates on a similar principle, utilizing a pair of keys—a public key, which can be freely shared, and a private key, which remains confidential.
This two-key system serves as a robust security scaffold, likening it to the dual nature of divine protection that accompanies believers. Just as one must guard their heart (Proverbs 4:23), individuals must safeguard their private keys against unauthorized access. The public key can be disseminated widely, allowing anyone to send encrypted correspondence; however, only the designated recipient possesses the private key to decrypt and access the information.
Asymmetric algorithms, such as RSA or ECC (Elliptic Curve Cryptography), provide a higher level of security for sensitive communications, despite being slower and computationally intensive. They illustrate the Christian concept of grace—wherein one can freely offer their public key, extending an invitation for trust, while protecting their heart through the private key. This reflects the significance of sharing love and kindness while guarding oneself against potential harms.
Real-World Applications
Consider how these two forms of encryption manifest in everyday life. Online banking, e-commerce, and secure messaging applications frequently rely on both symmetric and asymmetric techniques. When a user logs into a secured website, they often engage in a dance between these methods. The asymmetric protocol sets up a secure channel, exchanging keys that transition into symmetric encryption for the remainder of the session.
This synergy can be viewed through the lens of community dynamics in Christianity. Just as different parts of the body serve unique roles yet function together for the overarching purpose, symmetric and asymmetric encryption collaboratively ensure the integrity and confidentiality of our digital communications.
Ethical Considerations and the Importance of Trust
As technology continues to evolve, one must not overlook the ethical considerations surrounding encryption. A widely discussed moral dilemma arises in using these powerful tools—how do we balance the need for security against potential misuse? Encryption, while vital for protecting individual privacy, could also shield illicit activities. The balance between safeguarding the innocent and preventing wrongdoing is a challenge that requires careful reflection and discernment.
In a world driven by both technology and faith, fostering an environment of trust becomes paramount. This call to stewardship, inspired by Christian teachings, compels communities to cultivate practices that promote integrity in the digital landscape. Just as the Apostle Paul urged believers to bear one another’s burdens (Galatians 6:2), there exists a collective responsibility to ensure that encryption is used ethically and with integrity.
Conclusion: A Reflection of Values
The exploration of symmetric and asymmetric encryption unveils not merely technical mechanisms but rather rich symbolism aligned with enduring Christian values. Each form of encryption serves as a gatekeeper to the treasures of our shared lives—a reminder to protect the sacred and uphold trust. As we navigate the complexities of our increasingly interconnected world, let us commit to using these tools wisely and vigilantly, fostering a culture of respect and accountability that resonates with our collective belief in the sanctity of both our personal and communal experience.






Leave a Comment