The world of cryptography is woven with intriguing innovations and pivotal complexities, often leaving the layperson bewildered yet captivated. Among these cryptographic innovations, stream ciphers stand out. They are an enigmatic yet fundamental component of modern cryptographic practices. Understanding stream ciphers is crucial, particularly as they play an essential role in safeguarding our digital conversations and transactions.
At its core, a stream cipher encrypts data by converting plaintext into ciphertext in a continuous stream. Unlike block ciphers, which encrypt data in fixed-size blocks, stream ciphers process data one bit or byte at a time. This fundamental difference leads to unique advantages and distinctive applications.
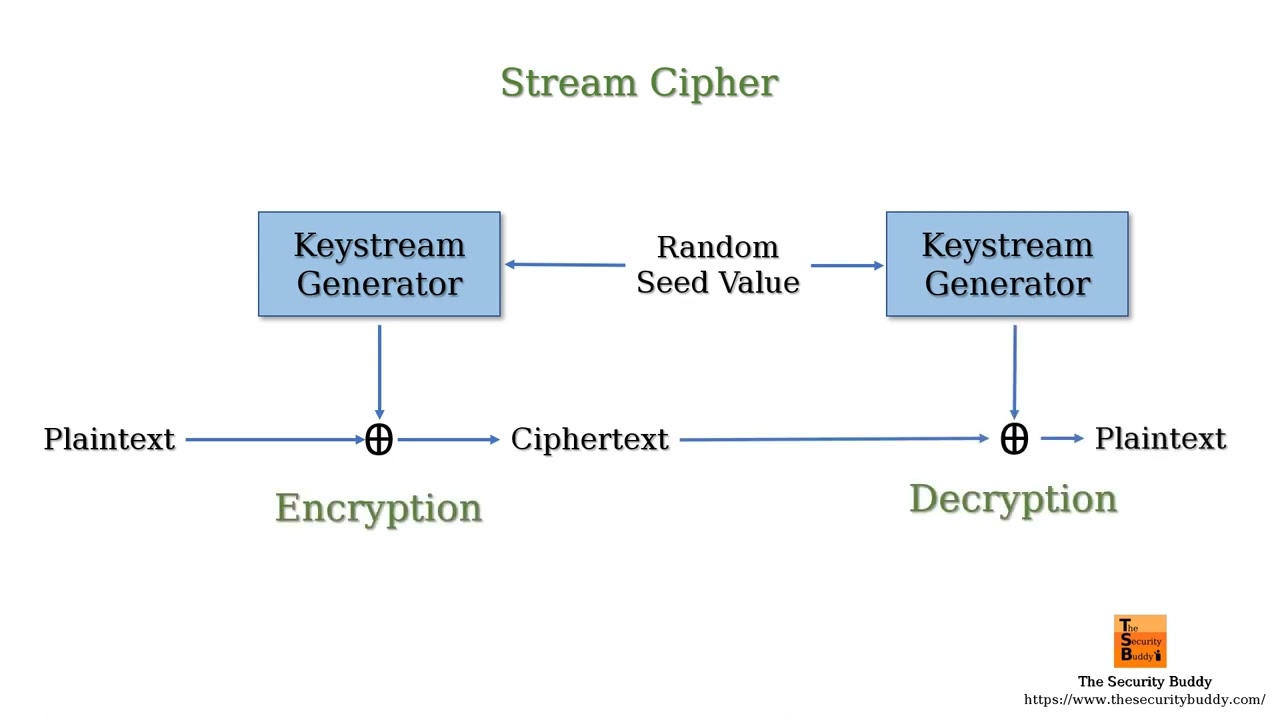
To comprehend the mechanism behind a stream cipher, one must first consider its operation. A stream cipher employs a pseudorandom keystream generator, which produces a sequence of bits that is statistically indistinguishable from random noise. The encryption process occurs by performing a bitwise operation, typically XOR (exclusive OR), between the plaintext and the generated keystream. This operation ensures that each bit of the plaintext is altered in a unique manner relative to the corresponding bit of the keystream.
For example, if the plaintext is represented in binary and the keystream is equally represented, the XOR operation can be visually illustrated as follows:
Plaintext: 10101101 Keystream: 11001010 Ciphertext: 01100111
The simplicity yet effectiveness of this operation emerges from the properties of the XOR function. If either of the inputs is 0, the output equals the other input. Conversely, if both inputs are 1, the output is 0. This property ensures that even a single bit of change in either the plaintext or the keystream results in a drastically different ciphertext, thereby enhancing security.
One might wonder why an individual would choose a stream cipher over its block cipher counterpart. Stream ciphers boast several remarkable advantages, particularly their speed and efficiency. As they process data in a continuous stream, they are remarkably suitable for applications where data is transmitted in real time, such as voice over IP (VoIP) or live video streaming. The low latency associated with stream ciphers allows for seamless data transfer, making them an attractive choice for numerous modern applications.
Furthermore, stream ciphers tend to consume fewer computational resources. The ability to encrypt data in smaller increments means that they require considerably less memory and processing power, making them optimal for devices with limited capabilities, such as IoT (Internet of Things) devices and mobile phones.
Nevertheless, the fascination with stream ciphers is not solely rooted in their efficiency. There are deeper considerations at play, particularly their security implications. The strength of a stream cipher largely depends on the randomness and unpredictability of the keystream. A significant vulnerability arises when the keystream is predictable or when it is reused across multiple encryption sessions. In such scenarios, attackers have the potential to exploit these weaknesses, extracting invaluable information by analyzing the relationship between the ciphertexts and their corresponding plaintexts.
Among the established stream ciphers, RC4, originally devised by Ron Rivest in 1987, garnered widespread popularity for its simplicity and effectiveness. However, its vulnerabilities were gradually uncovered, leading many to rethink the security of stream ciphers. The discovery of weaknesses in RC4 prompted the cryptographic community to develop and endorse more secure alternatives.
Two notable stream ciphers that emerged in recent years are ChaCha20 and Salsa20, both designed by Daniel J. Bernstein. These ciphers not only rectify the shortcomings of their predecessors but also exhibit enhanced performance, particularly in environments lacking hardware acceleration. ChaCha20, in particular, has gained traction as an alternative to the aging RC4, praised for its robust security features and efficiency.
Another critical aspect of stream ciphers is the concept of synchronization. Both the sender and receiver must maintain a synchronous keystream to ensure successful decryption. Without proper synchronization, the intended recipient will be unable to access the original message. This presents an additional layer of complexity in implementation, particularly in environments where interruptions may occur during transmission.
In addition, stream ciphers exhibit a characteristic termed ‘bit independence,’ which means the cipher can produce a new bit of ciphertext even when other bits are being processed. This trait makes stream ciphers particularly resilient to certain types of attacks that may target more traditional cryptographic structures.
However, it is crucial to exercise caution when deploying stream ciphers. Ensuring that the initial keystream used for encryption is truly random and unique is paramount, as any deficiencies in these areas could drastically undermine the encryption’s effectiveness. The reliance on secure pseudorandom number generators is essential, as they form the bedrock of a secure keystream.
In conclusion, stream ciphers remain a compelling fixture in the discipline of cryptography. Their efficient processing capabilities coupled with their profound implications for secure communications present a fascinating dichotomy. As we continue to delve deeper into the digital age, the intrigue surrounding stream ciphers will only deepen, surfacing questions about security, efficiency, and the intricate balance of cryptographic effectiveness. Understanding stream ciphers is crucial, as they encapsulate a significant aspect of the ongoing narrative in the realm of digital security.








Leave a Comment