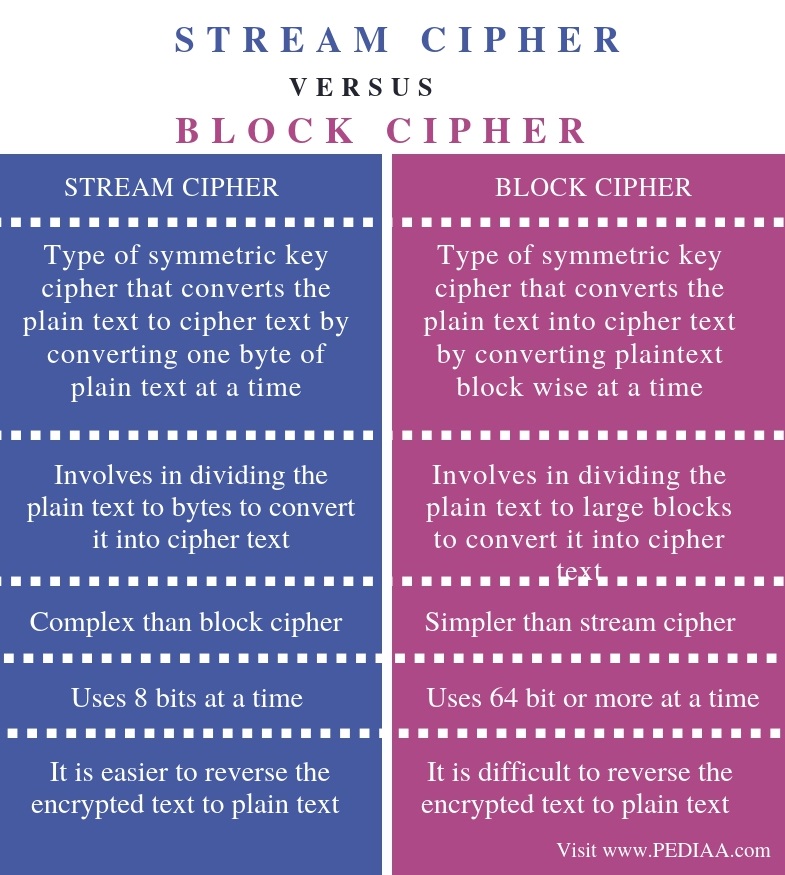
In the world of cryptography, two primary methods of encryption stand as formidable guardians of data integrity: stream ciphers and block ciphers. These two techniques serve the dual purpose of securing data while allowing it to navigate the vast expanse of digital communication. Their fundamental differences can be likened to the difference between a flowing river and the sturdy walls of a fortress. Each has its unique appeal, utility, and intricacies.
The river, representing stream ciphers, flows continuously, encrypting data bit by bit, like a fluid current weaving through the landscape. This method is akin to a painter delicately adding strokes to a canvas; every bit is significant and contributes to the ultimate masterpiece. Stream ciphers process plaintext in a continuous stream, applying a keystream generated by a pseudo-random generator. As long as the keystream remains secure and unpredictable, the resultant ciphertext remains impervious to prying eyes.
Conversely, the fortress symbolizes block ciphers, robust and structured, securing data in cohesive blocks. These ciphers take fixed-size chunks of plaintext and subject them to a series of complex transformations, producing corresponding blocks of ciphertext. It is as if the fortress’s walls are meticulously crafted to safeguard each precious gem within, ensuring that any attempt to breach them yields no valuable spoils. Block ciphers distill data into specified sizes, commonly 64 or 128 bits, firmly establishing a predictable framework for encryption.
Between these two methods, several characteristics emerge, illustrating their respective strengths and weaknesses. Stream ciphers excel in applications requiring high-speed encryption, such as voice communications or streaming video, where data flows continuously. They provide minimal latency, allowing for immediate encryption and decryption, so practical for real-time applications.
On the other hand, block ciphers showcase their strengths in environments demanding robustness. Their meticulous approach to data chunking and transformation fortifies them against various types of cryptographic attacks. As defenders of sensitive information, they provide an unyielding bastion against data breaches and unauthorized access. This is particularly evident when securing files or transmissions requiring a rigid level of security, as seen in banking systems and confidential communications.
While both encryption methods serve vital roles in securing data, their susceptibility to vulnerabilities makes them unique in their appeal. Stream ciphers, due to their nature, may become vulnerable if the keystream is reused; such instances can lead to catastrophic failures, illuminating the risk of exposing sensitive data. The famous RC4 stream cipher, once celebrated for its speed, faced scrutiny and degradation in security over the years, ultimately falling from grace in many applications.
Conversely, block ciphers face distinct challenges. When subjected to specific attack methodologies, such as differential and linear cryptanalysis, the integrity of a block cipher might become compromised. Renowned algorithms like AES (Advanced Encryption Standard) have emerged as resilient contenders against these potential vulnerabilities, embodying a classification of excellence in modern cryptographic practices.
A significant distinction in operational mechanisms also exists between stream and block ciphers. Stream ciphers often utilize XOR operations for encryption, a simple yet effective technique where each bit of the plaintext is combined with a corresponding bit from the keystream. This operation, while efficient, requires a highly randomized keystream to maintain security over time. The security of the stream relies fundamentally on the unpredictability of the keystream generated, making its robustness dependent on the underlying algorithm.
In contrast, block ciphers operate through substitution and permutation techniques within their defined framework. Algorithms, such as DES (Data Encryption Standard) and AES, employ several complex rounds, contributing to a fortress-like defence against unauthorized decryption attempts. Each block undergoes transformations that diffuse and disperse plaintext over the ciphertext, making it increasingly obscured and interwoven, thus enhancing security.
The choice between employing a stream cipher or a block cipher lies in assessing the specific requirements of a given application. Stream ciphers flourish in scenarios demanding high throughput and real-time efficiency, fabricating a fabric of data that aligns seamlessly with communication protocols. Their versatility in streaming applications—whether in encryption for audio calls, live video feeds, or ephemeral messaging—highlights their dynamic allure.
In a stark contrast, block ciphers reign supreme in environments necessitating structured security. Their methodical and calculated approach provides resilience against evolving threats. A banking institution, compelled to maintain confidentiality in transactions, opts for block ciphers to safeguard sensitive financial data, leveraging the protective intricate patterns forged through an extensive series of encryptions.
In conclusion, the intriguing juxtaposition of stream ciphers and block ciphers embodies the sophistication of modern cryptography. The flowing river, with its dynamic nature and speed, contrasts against the steadfast fortress, representing strength and integrity. To navigate the digital realms securely, understanding the nuanced distinctions between these two encryption methodologies is imperative. Each cipher possesses unique attributes tailored to diverse applications, offering an arsenal of options for safeguarding information. As technology evolves, so too will the defenses that these cryptographic strategies provide, ensuring a continuing evolution in the protection of our invaluable digital assets.







Leave a Comment