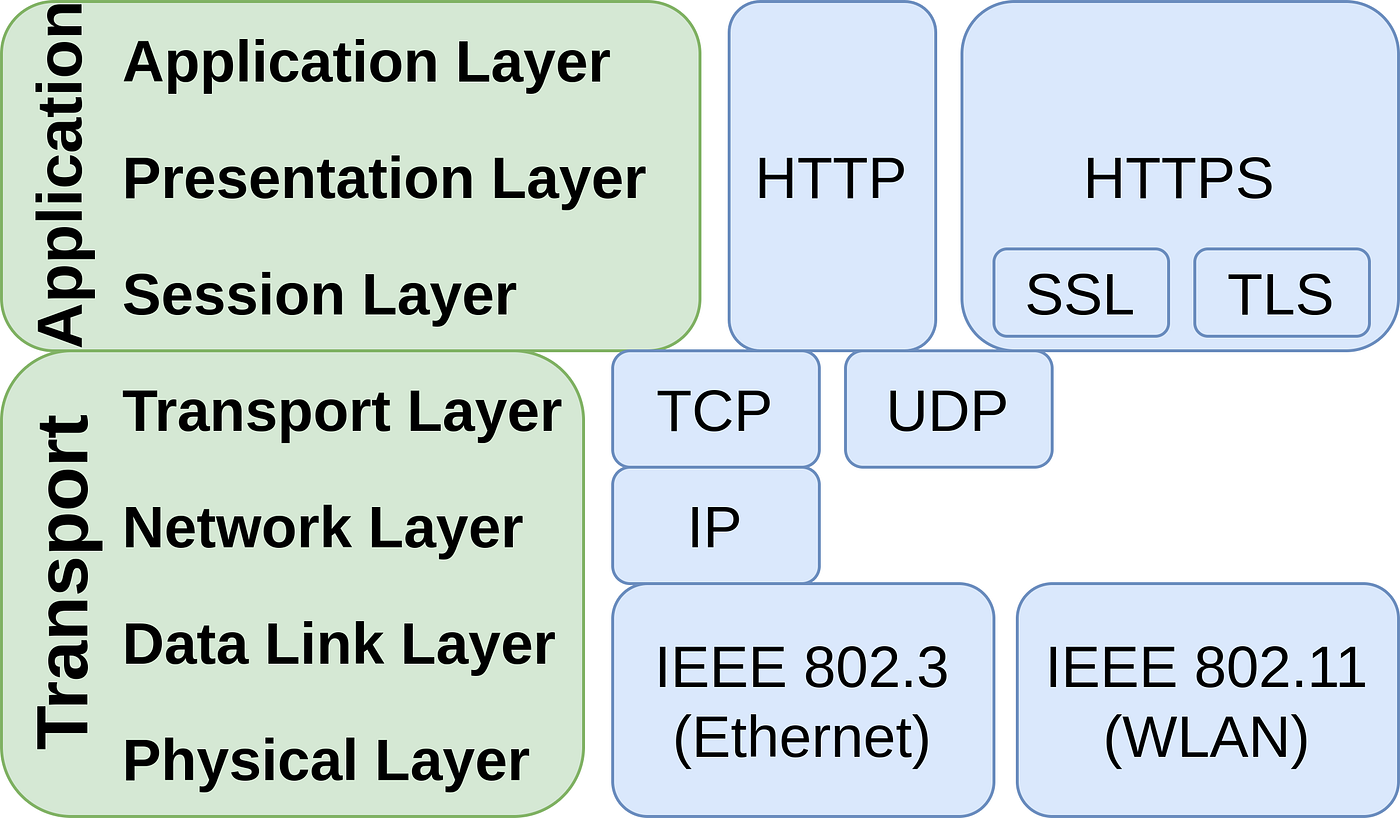
In an increasingly interconnected digital landscape, the protection of sensitive information has assumed paramount importance. Picture a medieval castle, fortified with robust walls, a moat, and guards vigilantly watching the gates. In this scenario, the castle symbolizes a secure online connection, while the walls and guards represent various protocols that ensure the integrity and confidentiality of the information within. Central to this digital fortification are three critical components: SSL, TLS, and HTTPS. Understanding their distinct roles in ensuring data security is crucial for anyone navigating the complexities of online communication.
To embark on this exploration, it is essential to first delineate the nuances between SSL (Secure Sockets Layer) and TLS (Transport Layer Security). SSL emerged in the mid-1990s as one of the first protocols designed to provide secure communication over the internet. It employs encryption to obfuscate data in transit, protecting it from prying eyes. However, while SSL laid the groundwork for secure communications, it is now considered obsolete, largely due to vulnerabilities that emerged over time. The final versions of SSL, namely SSL 2.0 and 3.0, have been officially deprecated and should no longer be used for securing communications.
Enter TLS, the successor to SSL, which was introduced in 1999 as an evolution of this security protocol. Think of TLS as a refined version of SSL, warranting robust security features that address the vulnerabilities inherent in its predecessor. TLS 1.0 and subsequent versions have enhanced encryption capabilities, improved authentication methods, and more rigorous integrity checks. It is akin to upgrading from an ancient castle model to a modern fortress equipped with advanced surveillance technology and sophisticated defenses.
While SSL and TLS may be used interchangeably in casual conversation, it is crucial to recognize that TLS is the contemporary standard for secure communications. Consequently, any reference to SSL in today’s context typically implies TLS, marking an essential distinction that underscores the evolution of digital security.
Now, let us expand the focus to HTTPS (Hypertext Transfer Protocol Secure). At its core, HTTPS is an extension of HTTP that incorporates SSL/TLS protocols, thus guaranteeing a secure channel over an insecure network, such as the Internet. It is comparable to an armored transport vehicle delivering sensitive cargo; while the vehicle itself may traverse perilous roads, its armored shell provides security for the goods within. The encapsulation of HTTP within the protective layer of SSL/TLS ensures that data exchanges between a client (like a web browser) and a server retain confidentiality and integrity.
When a user visits an HTTPS-enabled website, a secure connection is established through a process called the SSL/TLS handshake. This handshake serves as a negotiation phase between the client and server, determining which version of SSL/TLS to use, the specific encryption algorithms, and the necessary cryptographic keys. The intricacies of this handshake are akin to two knights engaging in parley before entering into a truce; each party must first agree upon terms before trust can be established, ensuring the safe passage of information.
One of the salient features of TLS is its integration of public key infrastructure (PKI), which utilizes a pair of cryptographic keys—a public key, which can be freely shared, and a private key that remains confidential. When a client initiates a connection to a server, the server provides its public key, allowing the client to encrypt a message that only the server can decrypt using its private key. This ingenious symbiosis ensures that intercepted messages remain indecipherable without access to the corresponding private key. It is the quintessence of modern cryptographic practices, exemplifying the allure of duality: sending and receiving in equal measure, echoing harmony in communication.
Despite the elegance of these protocols, the digital realm is not impervious to threats. Cyber adversaries frequently target vulnerabilities in outdated systems. The infamous Heartbleed bug, which exploited weaknesses in OpenSSL, demonstrated that even robust castles could fall prey to unforeseen breaches. Such vulnerabilities highlight the importance of continuous updates and adherence to best practices when implementing SSL/TLS and HTTPS. Ensuring that the cryptographic libraries and configurations are up to date becomes paramount in countering emerging threats.
Furthermore, recent trends indicate a growing focus on the importance of HTTPS as a ranking factor in search engine algorithms. Websites employing HTTPS not only secure user data but also enhance their credibility in the eyes of visitors and search engines alike. This is reminiscent of a country’s commitment to public safety; societies that value security are often perceived as more stable and attractive to citizens and visitors. In this digital age, HTTPS is no longer an optional add-on; it has become the sine qua non for trustworthy web presence.
In summation, the interplay between SSL, TLS, and HTTPS serves as the cornerstone of secure online communication. Each component possesses distinct attributes that contribute to an overarching protective strategy in safeguarding data transmissions. As our digital lives become increasingly intertwined with sensitive personal information, understanding these protocols becomes paramount. Much like the nobility of a castle defending its treasures, securing online interactions is a collective responsibility, requiring vigilance, knowledge, and a steadfast commitment to embracing the most advanced security measures available.








Leave a Comment