In the realm of digital security, encryption serves as a cornerstone in safeguarding sensitive data from prying eyes. Among the various cryptographic methods available, the use of 128-bit and 256-bit encryption keys has become a pivotal discussion point. A decisive factor in cryptography is the balance between security and performance. At first glance, it may seem that opting for a longer key invariably provides superior security. However, the question “Should you use 128-bit or 256-bit keys?” unveils a more nuanced narrative. The answer to this query isn’t straightforward; it heavily depends on contextual factors, including the nature of the data being protected and the threats it faces.
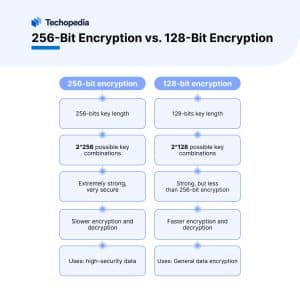
To understand the implications of key length, one must first appreciate the bedrock principles of cryptography. The strength of an encryption key is quantitatively assessed based on its key size; here lies the distinction between 128-bit and 256-bit keys. In simplistic terms, a key’s length determines the number of possible combinations available for decryption. A 128-bit key can have approximately 3.4 x 10^38 combinations, while a 256-bit key amplifies that figure to about 1.1 x 10^77. This exponential discrepancy raises an obvious question: does a longer key translate to unassailable security?
Besides mathematical prowess, one must analyze practical considerations. For most modern applications, particularly those utilized in consumer-grade scenarios, 128-bit encryption is generally deemed robust enough. Extensive cryptanalysis over the years has revealed no inherent vulnerabilities that would permit feasible brute-force attacks against properly implemented 128-bit keys. Therefore, for everyday tasks such as online banking and personal communications, 128-bit encryption often suffices to thwart unauthorized access.
However, as digital threats evolve, so too must our defensive strategies. Organizations dealing with highly sensitive information—financial institutions, government agencies, or medical facilities—may find the enhanced security of 256-bit keys invaluable. The potential for quantum computing techniques to disrupt established cryptographic standards presents an additional layer of complexity. Quantum resilience is still a theoretical discussion, but it looms large in strategic planning. Theoretically, a quantum computer could significantly reduce the time required to break cryptographic keys, rendering what is currently considered strong encryption vulnerable. In such scenarios, the extended security offered by 256-bit keys becomes not just desirable but necessary.
It’s also prudent to evaluate the regulations and compliance frameworks that govern your sector. The Payment Card Industry Data Security Standard (PCI DSS), for instance, emphasizes robust encryption protocols for protecting cardholder data. In these instances, the choice of a 256-bit key may align better with regulatory expectations and stringent security mandates, thus protecting the organization from potential legal repercussions.
Moreover, operational environments also play a critical role in this decision-making. For applications involving a high throughput of data or requiring low latency, the computational overhead associated with 256-bit encryption might present an inconvenient trade-off. The trade-offs between security and performance should not be underestimated. A significant increase in processing time or resource consumption can lead to bottlenecks that affect user experience. As such, organizations must thoughtfully assess their operational bandwidth when considering which encryption standard to implement.
It’s worth acknowledging that the situations are not black and white. Hybrid approaches can often be beneficial. For instance, employing 128-bit encryption in combination with other security measures—such as multifactor authentication, intrusion detection systems, and rigorous access control policies—can create a multilayered defense strategy. This blend allows organizations to take advantage of efficiency without sacrificing a commensurate level of security.
A context-based framework is vital in making this decision. Questions to contemplate include: What types of data are you encrypting? What are the potential costs of a data breach? Who are your adversaries, and what resources might they deploy to compromise your security? These inquiries catalyze a more detailed risk assessment, which in turn, can inform the choice between 128-bit and 256-bit encryption. An organization in an emerging market with limited resources may prioritize practical and responsive encryption solutions over theoretical maximum security. Conversely, an entity entrenched in a high-stakes environment must account for the value and sensitivity of their data, which may justify the expenditure associated with 256-bit keys.
In conclusion, the decision between 128-bit and 256-bit keys when encrypting data demands critical analysis that transcends surface-level perceptions. It is not merely a question of resistance against brute-force attacks or compliance with regulatory frameworks; it palpably impacts performance, user experience, and overall data integrity. Each organization has its unique risk profile shaped by operational needs, compliance mandates, and threat landscapes. Swerving toward a conclusion based on average assumptions may lead one astray. Essentially, the choice must be deliberate—balancing security, performance, and the lessons learned from past vulnerabilities while anticipating future developments in technology is paramount. Ultimately, the adage “it depends” serves as a fitting reminder of the complexities involved in cryptographic decisions. In this ever-evolving digital landscape, one must be adaptive and vigilant, constantly reassessing the efficacy of encryption strategies.







Leave a Comment