In the vast expanse of cryptography, where secrets intertwine with layers of complexity, one algorithm has stirred both admiration and disdain: RC4. Initially heralded as a robust stream cipher, its legacy has come under scrutiny in the contemporary realm of cybersecurity. So, is RC4 truly obsolete or does it still possess a unique allure amidst modern encryption battles?
To understand the trajectory of RC4’s acceptance, one must traverse back to its genesis. Developed by Ron Rivest in 1987, the RC4 algorithm emerged during a time when the digital landscape was burgeoning with potential yet inadequately equipped to navigate the intricacies of security. With its simplicity in design and a remarkably fast execution, it swiftly became a favorite among developers. Picture a Swiss Army knife in the hands of an ambitious explorer—versatile, adaptable, and immensely popular.
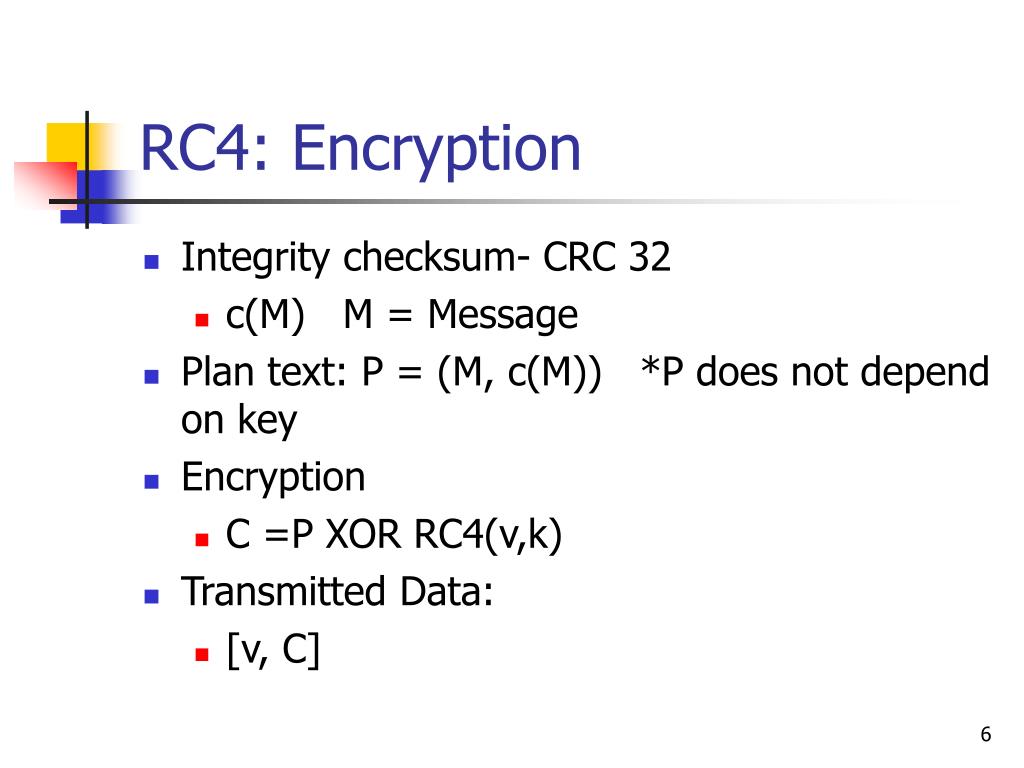
RC4 operates by generating a stream of pseudo-random bits derived from a secret key, effectively transforming plaintext into ciphertext. It’s a mesmerizing dance of bits, where the key acts as a conductor guiding the orchestra of data. However, as the world of digital communication evolved—growing in complexity and sophistication—the weaknesses of RC4 began to surface like cracks in an old dam. What was once viewed as a nimble tool became a point of contention.
The emergence of cryptographic analysis revealed vulnerabilities inherent in RC4. Particularly alarming was its susceptibility to biases in its output stream, which could be exploited by adversaries to infer details about the plaintext. It was as if the ice beneath a seemingly pristine lake began to fracture, revealing treacherous waters below. Consequently, the advent of advanced cryptographic techniques and the revelation of these vulnerabilities ushered the algorithm into a maelstrom of obsolescence.
In the face of such adversity, RC4 has been officially deprecated by many organizations and standards bodies, including the Internet Engineering Task Force (IETF). They issued warnings akin to cautionary tales to those who would still consider wielding this outdated cipher. It is recommended to relinquish the once-beloved Swiss Army knife and instead opt for more fortified alternatives, like AES (Advanced Encryption Standard). However, the question emerges: does the obsolescence of RC4 signify its complete demise, or is there a sliver of utility dissolved within its code?
In certain niche scenarios, RC4 may still find application. Its speed remains a remarkable asset, which can be particularly advantageous in environments where performance trumps stringent security requirements. For example, in lightweight applications or constrained devices with limited processing capabilities, the agility of RC4 can render it a practical, albeit lower-security option. Imagine a seasoned locksmith offering a quick, temporary solution for an enduring problem—efficient, yet not immune to scrutiny. In such instances, context is critical. While RC4 may perform efficiently, understanding the inherent risks involved is paramount.
Considering the evolution of networking protocols further illustrates the dichotomy of RC4’s status. For instance, its incorporation within the WEP (Wired Equivalent Privacy) protocol was disastrous. WEP’s inadequacies became painfully evident, leading to a rapid decline in confidence among users and the eventual development of stronger protocols, such as WPA2 (Wi-Fi Protected Access II). Here lies a cautionary metaphor: reveling in the nostalgia of a well-loved relic is futile if it causes more harm than good. The lesson learned fosters the breed of caution required when dealing with legacy encryption mechanisms.
Transitioning from the past to the present, it becomes increasingly evident that modern encryption standards—specifically AES—have set a superior benchmark, combining robustness with efficiency. AES employs a block cipher methodology, deliberately designed to resist even the most aggressive of attacks. It is not merely an upgrade of its predecessors but rather a fortress built with walls of sophisticated mathematical structures, standing resolute against the test of time and evolution of technique.
Nonetheless, the allure of RC4 cannot be entirely disregarded. It is a vestige of a bygone era, embodying a unique narrative in the annals of cryptography. As discussions transpire around its obsolescence, one remains fascinated by the dichotomy of admiration and caution. For some, it encapsulates the romance of early secure communications—when the digital world was trying to unveil its myriad complexities, and RC4 was at the forefront, a symbol of innovation.
Ultimately, as we navigate the intricate web of cryptography, RC4 serves as both a lingering whisper and a stark reminder of the progress made. While the official consensus categorizes it as a relic best left behind, it continues to pique interest within specific applications where speed is critical and security is secondary. Whether one views RC4 as obsolete or still useful ultimately depends on the lens through which it is examined—the historic lens of innovation or the contemporary lens of cybersecurity demands.
In conclusion, the winding path of RC4’s legacy plays out in stark contrasts— a tale of brilliance and caution. Its presence in modern cryptography might dwindle, yet its story remains significant, reminding us of the necessity for continuous evolution in our approaches to secure communication. Thus, as the digital landscape continually expands, so too must our commitment to adapt and fortify the enigma of information security.








Leave a Comment