Email remains one of the most prevalent communication tools in the digital realm, yet it is often overlooked in discussions about security. As individuals and organizations rely heavily on electronic mail, the urgency to safeguard our inboxes is paramount. A profound understanding of public key cryptography (PKC) illuminates how emails can remain secure amidst the vast landscape of cyber threats.
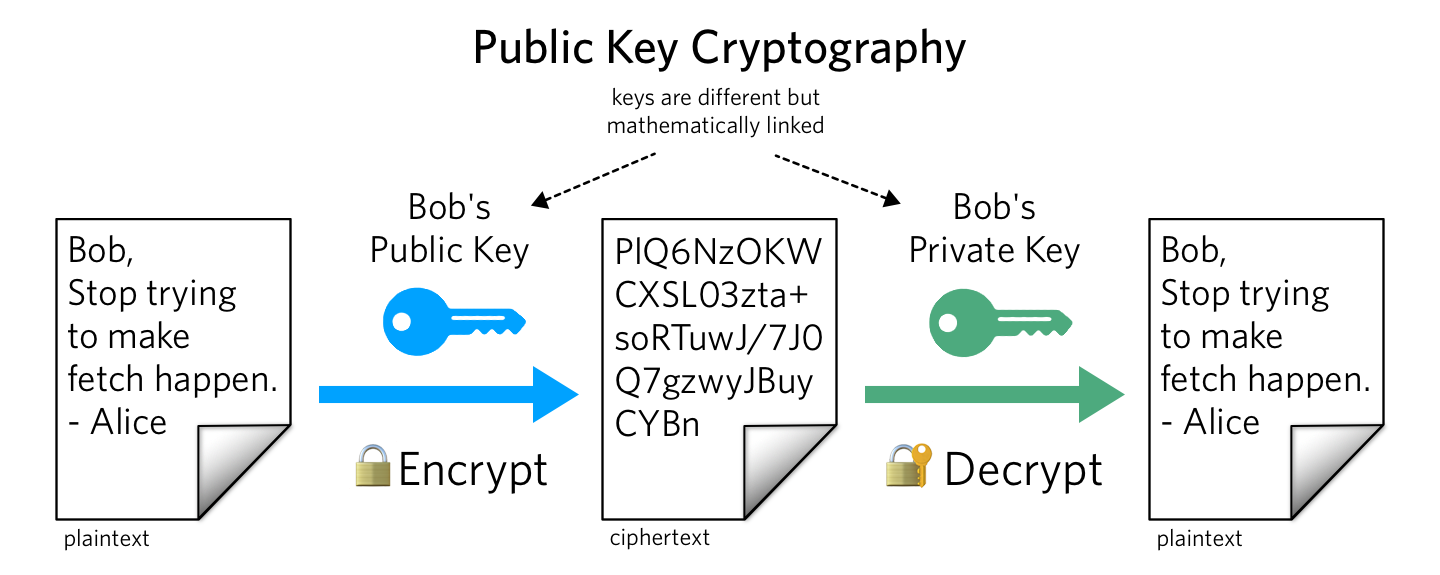
At its core, public key cryptography is predicated on the principles of asymmetric encryption, uniquely designed to fortify data transfer. Unlike symmetric cryptography, which utilizes a single key shared between the communicating parties, PKC employs a pair of keys: a public key and a private key. The public key may be disseminated freely and is utilized by anyone wishing to send secure information, while the private key is meticulously guarded by the recipient and should never be shared. This intricate dance of keys is pivotal to modern email security protocols.
As an email is dispatched, the sender leverages the recipient’s public key to encrypt the message. To an outsider, the encrypted email is simply a convoluted string of characters, devoid of discernible meaning. Only the corresponding private key can decode this information, allowing the intended receiver to access its content. This mechanism ensures that even if a malicious actor intercepts the communication, deciphering it without the private key is nearly insurmountable, thus safeguarding the sanctity of the correspondence.
Public key infrastructure (PKI) enhances this cryptographic landscape by establishing a framework for managing digital certificates and public-key encryption. Entities known as Certificate Authorities (CAs) vouch for the authenticity of public keys, thereby mitigating the risk of impersonation and man-in-the-middle attacks. The absence of such a verifying framework could lead to rampant impersonation, eroding trust in email as a reliable medium of communication. Consequently, CAs embody fundamental guardians of integrity in the digital communications ecosystem.
Cryptographic protocols like PGP (Pretty Good Privacy) and S/MIME (Secure/Multipurpose Internet Mail Extensions) are common implementations of public key cryptography in email systems. PGP, pioneered in the early 1990s, allows users to encrypt their emails and files, as well as append digital signatures. This dual functionality ensures confidentiality and non-repudiation; the recipient can ascertain the origin of the email and verify it has not been tampered with. On the other hand, S/MIME, which integrates seamlessly into most email clients, leverages X.509 certificates for similar purposes. Both systems ultimately reinforce the integrity and privacy of electronic communication.
Despite these stalwart security measures, several vulnerabilities stubbornly persist within the email infrastructure. Phishing attempts exploit human psychology, tricking users into divulging their private keys or login credentials. Social engineering tactics can bypass technological defenses, underscoring the importance of vigilance in conjunction with cryptographic solutions. Awareness and education about the characteristics of phishing schemes are essential to fortifying defenses against such deceptive tactics.
Moreover, while public key cryptography provides robust mechanisms for securing email at rest and in transit, it is not infallible. The reliance on users to manage their keys introduces a layer of risk. Compromise of a private key — whether through malware, social engineering, or theft — can exacerbate vulnerability. Thus, regular key rotations, judicious key management, and adopting strong passwords are prudent practices that should accompany cryptographic protocols.
In the grand tapestry of cybersecurity, trust is a cornerstone. Users must trust that the entities they communicate with are indeed who they purport to be. The presence of public key cryptography engenders a heightened degree of trustworthiness, fostering a secure environment in which sensitive information can be exchanged without fear of interception. The allure of PKC, therefore, lies in its capacity to facilitate secure digital dialogues, critical for both personal and institutional communications.
Your inbox is a repository of personal and professional correspondence; it contains nuggets of information that can profoundly impact your life. The increasing sophistication of cyberattacks demands an understanding and appreciation of the mechanisms that underpin email security. Public key cryptography serves as a bulwark against this ever-evolving threat landscape, endowing email with a semblance of safety in an otherwise perilous digital expanse.
While the technicalities of public key cryptography may seem daunting, its implications are straightforward: your email can remain secure. By embracing encryption, adopting advanced protocols such as PGP and S/MIME, and fostering a culture of awareness, we can collectively diminish the efficacy of malevolent cyber actors. The fascinating intricacies of PKC not only ensure the confidentiality of messages but also weave a fabric of trust essential for fruitful communications.
In conclusion, as long as email remains a staple of both personal and professional interaction, the mechanisms that keep it secure will also garner ongoing fascination and scrutiny. With the proliferation of sophisticated digital threats, public key cryptography will continue to play a pivotal role in preserving the sanctity and security of our inboxes. Maintaining a proactive approach to email security not only protects individual users but also fortifies the collective digital ecosystem against potential breaches.







Leave a Comment