Public-key cryptography, also known as asymmetric cryptography, represents one of the most significant advances in the field of information security. Its architecture enables secure communication over potentially insecure channels, and its intricate design reflects a brilliant blend of mathematical ingenuity and practical necessity. In this discourse, we will delve into the core characteristics of public-key cryptography that render it a pivotal element in the modern digital paradigm.
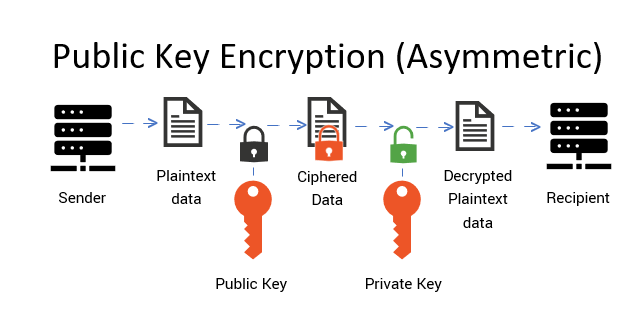
At its foundation lies the principle of dual-key pairs—public and private keys. This innovative mechanism distinguishes itself from traditional symmetric encryption methods, which rely on a single shared secret key. The public key is disseminated widely, allowing anyone to encrypt a message. Conversely, the private key remains confidential in the possession of the owner, ensuring that only they can decrypt any messages intended for them. This duality not only promotes secure communications but also facilitates authentication and data integrity, hallmark features of a robust cryptographic system.
The first notable characteristic of public-key cryptography is its reliance on complex mathematical algorithms. Algorithms such as RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) underpin this encryption model. RSA, developed in 1977, employs the difficulty of factoring large prime numbers, while ECC relies on the mathematical properties of elliptic curves. These cryptographic foundations allow for the creation of keys that are remarkably secure against brute-force attacks, ensuring that breaches remain profoundly challenging, even for advanced computational entities.
The concept of digital signatures emerges next as a critical facet of public-key cryptography. A digital signature, akin to a handwritten signature, provides verification of the signer’s identity and the message’s integrity. When a user signs a document with their private key, any recipient can employ the corresponding public key to authenticate the signature’s validity. This capability is paramount in various applications, from securing emails to validating software updates, thereby fostering trust in the digital ecosystem.
In addition to facilitating authentication, public-key cryptography also enhances confidentiality. This characteristic is particularly significant in an era where data breaches have become alarmingly common. When individuals or organizations send sensitive information, encrypting the message with the recipient’s public key ensures that only the intended recipient can decrypt it using their private key. This end-to-end encryption strategy is vital in safeguarding personal data, financial information, and confidential corporate communications.
Moreover, the scalability of public-key infrastructure (PKI) underscores its practicality in real-world applications. Unlike symmetric encryption, which necessitates prior secure distribution of secret keys between parties, public-key systems eliminate this requirement. Individuals or organizations can generate public and private key pairs at will, allowing seamless integration into various platforms. This scalability is instrumental in facilitating secure transactions in online banking, e-commerce, and digital signatures on blockchain systems.
However, no system is without its shortcomings. Public-key cryptography, while powerful, is not immune to vulnerabilities. One significant concern is the reliance on key management practices. Users must safeguard their private keys, as loss or compromise can lead to irreversible breaches. Furthermore, if a public key is erroneously tied to an identity through a flawed certificate authority (CA), malicious entities can execute man-in-the-middle attacks, intercepting sensitive information. Thus, it is imperative for users and organizations to understand proper key management and digital certificate vetting to maintain the integrity of the cryptographic framework.
Another dimension to consider is the computational overhead associated with public-key cryptography. The mathematical operations involved in encryption and decryption are generally more resource-intensive than those utilized in symmetric encryption. This computational weight can introduce latency, particularly in environments demanding real-time processing. Consequently, hybrid cryptographic systems often emerge, combining the strengths of both asymmetric and symmetric algorithms. For example, a public-key scheme can be employed to exchange a symmetric session key, subsequently encrypting the actual data more efficiently.
Furthermore, the ever-evolving landscape of cryptographic algorithms presents both challenges and opportunities. As computational power escalates and new vulnerabilities surface, the need for continually updated algorithms becomes crucial. The advent of quantum computing heralds a paradigm shift, as certain quantum algorithms could potentially compromise the encryption mechanisms presently in use. As a result, the cryptography community is actively researching quantum-resistant algorithms to safeguard against future threats.
In conclusion, the allure and significance of public-key cryptography lie in its ability to secure communication, authenticate identities, and preserve data integrity amidst expansive digital interactions. Its asymmetric nature, complex mathematical underpinnings, and scalable infrastructure provide a robust framework for addressing contemporary security challenges. As the digital landscape evolves, so too must our understanding and implementation of cryptographic methods. The safeguarding of information is not merely a technical task; it is an ongoing commitment to fostering trust and security in an increasingly connected world.








Leave a Comment