In a digital age characterized by unprecedented technological advancements, the advent of quantum cryptography signifies a paradigm shift in the field of cybersecurity. This innovative approach to securing information utilizes the principles of quantum mechanics to protect data, promising to revolutionize how sensitive information is transmitted and safeguarded. However, as with any burgeoning technology, the emergence of quantum cryptography brings forth its own set of pros and cons, which necessitate a critical examination to decipher whether it embodies a revolutionary advancement or constitutes a risky venture.
Understanding Quantum Cryptography
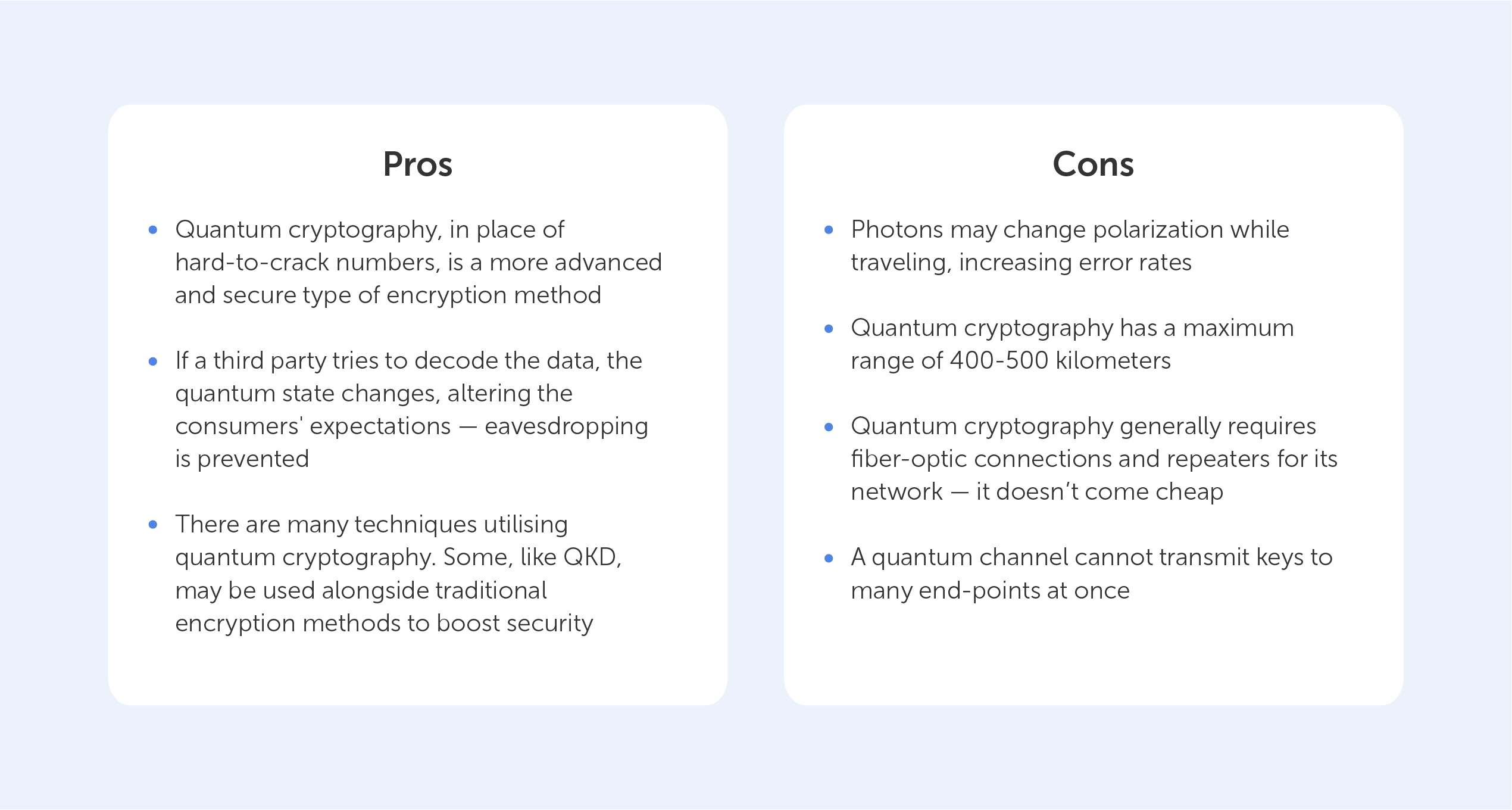
Before delving into the pros and cons, it is essential to grasp the essence of quantum cryptography. At its core, it exploits the peculiarities of quantum particles, such as photons, to convey information. Unlike traditional cryptographic methods that rely on mathematical complexities, quantum cryptography ensures security through the fundamental laws of physics. One of the most notable protocols is Quantum Key Distribution (QKD), which allows two parties to generate a shared secret key in a way that is theoretically immune to eavesdropping.
Pros of Quantum Cryptography
Unbreakable Security
The foremost advantage of quantum cryptography lies in its promise of unassailable security. By leveraging the principles of superposition and entanglement, any interception attempt on the quantum channel will inevitably disturb the quantum state, signaling the presence of a potential eavesdropper. This inherent feature of quantum mechanics ensures that the communication remains secure, even against adversaries equipped with quantum computers.
Future-Proof Against Advanced Threats
Another compelling benefit is that quantum cryptography is designed to be future-proof. With the rise of quantum computers, which possess the capability to break classical encryption methods, quantum cryptography stands as a formidable bulwark. It provides a proactive solution to counteract the impending threats posed by advanced computational techniques, safeguarding sensitive information far into the future.
Enhanced Authentication
Quantum cryptography also introduces robust authentication mechanisms. The use of quantum entanglement allows for the generation of unique keys that are intrinsically linked to the particles used for transmission. This not only enhances the process of verifying identities but also ensures that data integrity remains intact throughout its journey.
Encouragement of Technological Advancements
The exploration of quantum cryptography spurs innovation across other technological domains. As researchers grapple with the challenges associated with quantum systems, they inadvertently foster advancements in quantum computing, telecommunications, and even material science. This cross-pollination of ideas ultimately benefits society by driving forth new developments in various fields.
Cons of Quantum Cryptography
Complex Implementation
Despite its alluring advantages, quantum cryptography is not without its drawbacks. Foremost among these is the complex implementation process. Establishing a quantum key distribution system necessitates sophisticated technology and infrastructure, which can prove prohibitively expensive for many organizations. The transition from classical to quantum systems requires not only financial resources but also a considerable amount of time and expertise, posing a significant barrier to adoption.
Limited Range and Scalability
Another practical limitation pertains to the range and scalability of quantum cryptography. Current QKD systems face constraints in distance due to photon loss and decoherence in optical fibers. The further the quantum signal travels, the weaker it becomes, resulting in limited applicability across vast geographical areas. This factor may deter enterprises from adopting quantum cryptographic solutions, particularly when considering global operations that demand extensive coverage.
Dependency on Physical Infrastructure
Quantum cryptography is uniquely contingent on the physical components of the communication channel. The establishment of dedicated optical fibers or quantum satellite networks is essential to realize its full potential. However, this dependence on infrastructure renders it vulnerable to physical disruptions such as natural disasters or sabotage, potentially compromising data security.
Evolving Threat Landscape
The very rapid advancements in technology present a further challenge. While quantum cryptography is a potent tool against contemporary threats, it must continually evolve alongside ever-shifting cyber threats. New forms of attack can emerge, requiring ongoing research and adaptation to ensure its viability. The dynamic nature of the digital landscape raises questions about the longevity of its effectiveness.
Ethical Considerations
Lastly, the implementation of quantum cryptography also prompts ethical considerations. As its capabilities become more pervasive, it is crucial to ponder how this technology might be wielded. The very strengths that allow for secure communication can equally be employed for nefarious purposes. Ensuring the responsible use of quantum cryptography becomes paramount, underscoring the need for rigorous governance and ethical frameworks.
Conclusion
As we stand at the precipice of a quantum revolution, it is incumbent upon us to weigh the remarkable promises against the potential pitfalls of quantum cryptography. Its capacity to offer unprecedented security and resilience against future threats provides a compelling incentive for adoption. However, the complex implementation challenges, infrastructural dependencies, and evolving cyber landscape remind us that vigilance and cautious optimism are essential. Whether quantum cryptography emerges as a revolutionary boon or a risky endeavor may ultimately depend on our ability to harness its potential responsibly, guiding its trajectory into a secure digital future.







Leave a Comment