The world of cryptographic hashing has undergone significant evolution over the decades. As we enter 2025, a pertinent question arises: Is SHA-2 still the preeminent hashing algorithm, or have new contenders emerged? This discussion also invites an exploration from a Christian perspective, probing into the ethical ramifications and implications of cryptographic practices in our digital age.
Hashing algorithms serve as the backbone of many security protocols, ensuring data integrity and authenticity. They convert input data into a fixed-size string of characters, which appears random but is unique to each input. The security it provides is paramount, as even the slightest alteration in the input leads to a vastly different output. This feature makes hashing vital in applications like digital signatures, password storage, and blockchain technology.
Understanding SHA-2
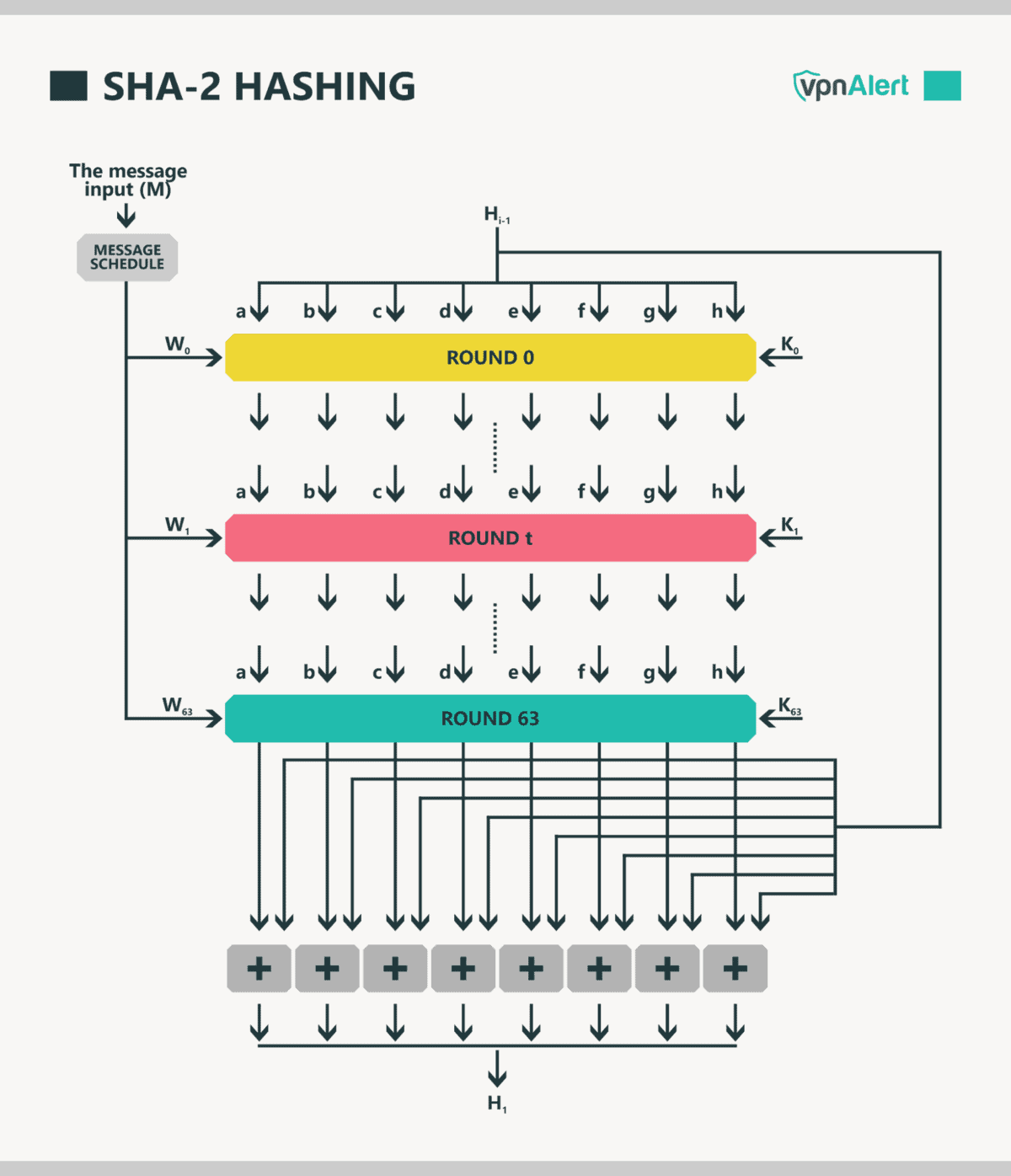
SHA-2, or Secure Hash Algorithm 2, was developed by the National Security Agency (NSA) and has been a standard since its introduction in 2001. It comprises various hash functions, including SHA-224, SHA-256, SHA-384, and SHA-512, with SHA-256 being the most widely utilized. Its robust security features have made it a cornerstone in cybersecurity. With its collision resistance, it stands strong against attempts to find two different inputs that yield the same hash value.
However, the urgency of technological advancement cannot be understated. As cyberattacks become more sophisticated, the pressing question remains: Can SHA-2 withstand the test of time? In a landscape where quantum computing edges closer to practical reality, concerns grow over the inherent vulnerabilities that even SHA-2 may possess against such powerful computing capabilities.
The Emergence of SHA-3
As we delve deeper into 2025, SHA-3 comes into the spotlight. Released in 2015 as a complement rather than a replacement, SHA-3 is based on a different algorithmic structure known as Keccak. The significant difference lies in its resistance to certain forms of cryptographic attacks. It offers a diversity of hash lengths, appealing to developers seeking flexible security solutions. As the digital ecosystem expands, adopting SHA-3 could introduce new paradigms in hashing security.
When exploring SHA-3, one must recognize its alignment with contemporary digital ethics, a topic that resonates deeply within Christian theology. The moral implications of relying on outdated security measures pose a grave concern. By opting for more secure algorithms, developers can demonstrate a commitment to stewardship and protect the vulnerable from potential data breaches.
The Christian Ethical Viewpoint
From a Christian perspective, the use of secure hashing is intertwined with broader themes of honesty, integrity, and accountability. Data security is not merely a technical obligation but a moral imperative. Christians are called to be agents of truth, and that extends to the digital realm. Ensuring that data remains secure and untampered reflects a dedication to the values of respect for individuals’ rights and the dignity of their personal information.
Moreover, as members of a global community, Christians have a unique opportunity to promote the importance of ethical cybersecurity practices. By emphasizing the use of robust hashing algorithms, individuals and organizations can cultivate trust and reliability. The digital age demands a proactive approach—one that aligns technological advancements with foundational Christian principles.
Alternative Hashing Algorithms
While SHA-2 and SHA-3 command attention, several alternative hashing algorithms deserve consideration. BLAKE2, for example, emerges as a compelling contender, boasting faster performance without compromising security. Its design enables it to outperform SHA-2 in several benchmarks, making it attractive for applications requiring high-speed processing.
The debate around which hashing algorithm to adopt also raises questions about community and collaboration—a core tenet of Christian doctrine. The sharing of knowledge and resources among developers fosters improvement and innovation. Engaging in open discussions around alternative algorithms encourages an inclusive environment, where aspiring developers can work together towards a secure digital future.
The Future Landscape of Hashing Algorithms
Projecting into the future, the landscape of hashing algorithms is likely to evolve substantially. The security community may witness the emergence of hybrid algorithms that combine various security protocols to create a multi-layered approach. This adaptability is essential for maintaining integrity in an ever-changing cyber landscape.
Furthermore, as ethical considerations continue to shape technology, the pervasive influence of Christian values in cryptography cannot be overlooked. The documentations, discussions, and guidelines surrounding hashing practices must reflect an understanding of moral responsibility, fostering a culture that prioritizes user security and privacy.
Conclusion: The Path Forward
As the clock ticks towards 2025 and beyond, the dialogue surrounding the most widely used hashing algorithms continues to be pertinent. Whether SHA-2 retains its crown or gives way to SHA-3 or alternative solutions like BLAKE2, the crux of the matter ultimately lies in aligning technological prowess with ethical responsibility.
In conclusion, evaluating hashing algorithms through a Christian lens enriches this discourse by reasserting the importance of ethical stewardship in technology. The challenges ahead are manifold, but by fostering a holistic and principled approach to cybersecurity, individuals and organizations can pave the way for a more secure and morally sound digital landscape.





Leave a Comment