In the realm of cryptography, the significance of ensuring data integrity has led to the development of different mechanisms to authenticate messages. One such mechanism is the Message Detection Code (MDC), which plays a pivotal role in securing communications. This article delves into the attributes of MDCs, compares them with similar cryptographic constructs like Message Authentication Codes (MACs), and explores their implications in contemporary cybersecurity.
Cryptography fundamentally involves transforming information into a secure format so that only authorized parties can access it. At the heart of this discipline lies the essential need to verify that a message has not been altered during transmission. This is where MDCs come to the forefront. An MDC is a mathematical construct that detects alterations in a message by generating a distinct code from the original message data.
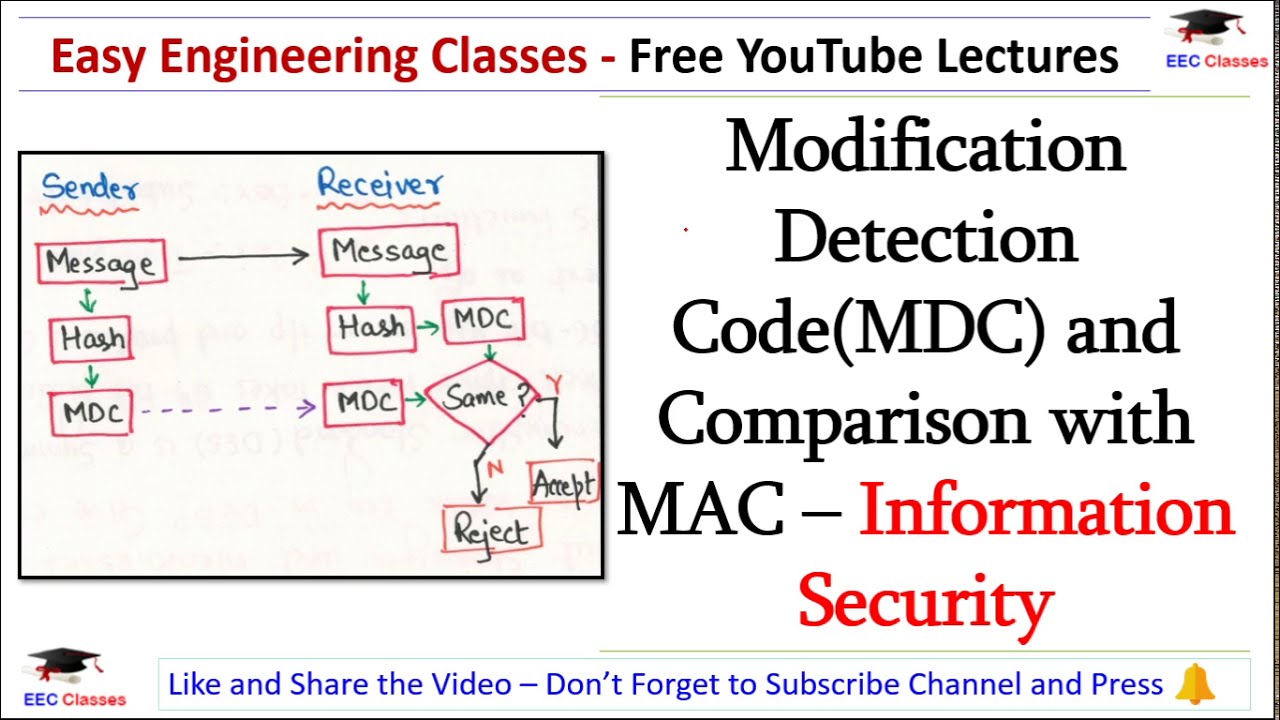
To appreciate the function of MDCs, it is important to understand the underlying principles of how they operate. At its core, the MDC takes input in the form of a message and applies cryptographic algorithms to produce a ‘code’ that represents the original data. This code is appended to the message before transmission. Upon receipt, the recipient can recompute the code from the received message and compare it to the code that accompanied it. If the two codes are congruent, the integrity of the message is assured, indicating no tampering occurred.
The utility of MDCs transcends simple integrity checks. One intriguing characteristic of MDCs is their ability to offer a level of validation that is less computationally demanding than more robust methods like MACs. While MACs incorporate a secret key in their generation process, thereby imposing an additional layer of security, MDCs can be constructed using public key techniques. This potentially widens their application scope, especially in environments where key management is cumbersome.
However, it is essential to acknowledge the inherent limitations that accompany MDCs. Although they proficiently detect modifications, they do not provide authentication of the source or the sender of the message. This means that while an MDC can indicate whether a message has been tampered with, it cannot distinguish whether the message originated from a legitimate source. This gap in security is primarily where MACs excel, as they integrate a secret key to safeguard both the content and the sender’s credibility.
Understanding the distinction between MDCs and MACs unveils the allure of this discussion. While some may view MDCs as a lesser tool in the cryptographic toolbox, their existence highlights a critical point of fascination in data integrity verification. The tension arises from the trade-off between performance and security. In low-risk applications or environments where performance is prioritized over heightened security, MDCs can serve as an effective first line of defense against data corruption.
A typical application of MDCs can be observed in file transfer protocols where large payloads traverse potentially insecure networks. When transferring files, it is crucial to verify that the data remains unaltered from sender to receiver. Here, employing MDCs aligns with the necessity for speed without relying on a complex key management system. In these scenarios, one might appreciate the simplicity and efficiency brought forth by MDCs, despite their fundamental limitation.
As technology advances and data breaches become increasingly sophisticated, the relevance of every component within the cryptographic realm, including MDCs, evolves. With advancements in machine learning and artificial intelligence, newly developed algorithms and methods hint at promising ways to bolster the efficacy and reliability of MDCs. Researchers are actively exploring enhanced versions of MDCs that incorporate machine learning techniques to create even more resilient verification systems. This intriguing blend of traditional cryptography with modern computational capabilities represents a fertile area of exploration for future developments.
Furthermore, the evolution of cryptography is also influenced by the rising demand for secure communication across various platforms, particularly as digital interactions dominate our personal and professional lives. The omnipresence of cyber threats necessitates robust measures for data verification, which, while acknowledging the inherent shortcomings of MDCs, elevates their significance in everyday applications.
In contrast, the emergence of quantum computing posits a formidable challenge for contemporary cryptographic methods, necessitating ongoing discussions around the adaptability of MDCs to withstand future threats. As such conversations unfold, the basic framework of MDCs calls to mind the agility embedded within the cryptographic field. MDCs exemplify a crucial aspect of cryptography, where a delicate balance between simplicity and security is continuously navigated.
Ultimately, as the landscape of digital communication continues to evolve, MDCs serve as both a recognition of the intricacies of data integrity and a reminder of the persistent critiques that accompany any cryptographic tool. Their existence not only showcases the foundational concepts of data verification but also emphasizes the necessity of vigilance in the pursuit of security. Thus, the intrigue of Message Detection Codes extends beyond mere mathematical constructs and finds its way into broader discourses on the integrity and authenticity of information in our interconnected world.







Leave a Comment