Unbreakable cryptography, a concept often romanticized in espionage thrillers and hailed as the holy grail of information security, beckons us to explore whether it truly exists. To unravel this conundrum, we must first examine the historical trajectory of cryptography and its metrical evolution, akin to the journey of a river twisting through varied landscapes, reflecting both clarity and obfuscation.
Cryptography has adorned human communication since antiquity. The ancient Greeks used transposition ciphers to encode messages, transforming plaintext into a seemingly indecipherable series of symbols. Fast forward to the era of the Renaissance, where the advent of the Vigenère cipher introduced a multiplicative complexity by employing a keyword to encrypt messages—a precursor to modern practices. Each advancement laid a foundation, illuminating the dark art of secret writing, while simultaneously exposing vulnerabilities to prying eyes.
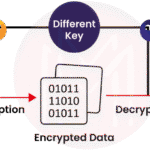
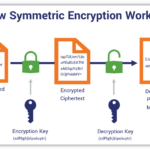
The digital age precipitated an explosion of cryptographic methodologies. In this tempest of technological advancement, public-key cryptography emerged as an ingenious abstraction, allowing two parties to communicate securely without prior exchange of keys. Public and private keys function like a locked mailbox; the public key is the mailbox you can distribute widely, while the private key remains your personal key to open it. However, while this innovation heralded new possibilities, it simultaneously invited scrutiny regarding its fortitude against an ever-evolving arsenal of computational power.
At the crux of the debate lies the characterization of ‘unbreakability.’ A viable metaphor can be drawn from the world of physical fortifications—a robust castle protected by towering walls and intricate moats may appear impregnable until adversaries devise innovative siege warfare techniques. Similarly, cryptographic systems may seem unassailable until new methods for decryption or unparalleled computational sophistication emerge.
For instance, the advent of quantum computing introduces uncharted territories in cryptography. Quantum mechanics operates on principles that defy classical logic, depicting electrons as both particles and waves. When applied to encryption, quantum computing could potentially unravel established cryptographic constructs, posing substantial threats to even the most complex algorithms. Shor’s algorithm, for example, is poised to dismantle the very fabric of widely-used RSA encryption. This existential question looms: is the tapestry of existing encryption techniques resilient enough to withstand the quantum tide?
In response to these existential threats, researchers have commenced a quest for post-quantum cryptography, striving to construct cryptographic algorithms that can withstand quantum attacks. This endeavor is akin to crafting a new alloy to resist the corrosive effects of saltwater on metal; the goal is to forge encryption mechanisms that endure despite shifting paradigms. The confluence of mathematics and computational science emerges as a bastion of hope, seeding potential solutions before quantum systems render current methods obsolete.
Moreover, the concept of unbreakability itself is inherently contingent upon context. The childhood belief in magic is akin to a child’s innocent understanding of invisibility cloaks; for those who do not possess the tools or knowledge to decipher code, the encryption is tantamount to being unbreakable. Yet, an adept cryptanalyst armed with empirical insights and advanced methodologies may expose a system’s vulnerabilities with relative ease. Thus, unbreakability is less a definitive state and more a movable goalpost, susceptible to the progression of knowledge and technology.
Furthermore, the arena of human factors in cryptography cannot be overlooked. The human element introduces vulnerabilities that technological fortifications cannot fully mitigate. The forgotten password, the weak passphrase, or even social engineering attacks—these are the cracks in the armor that adversaries exploit. Just as a well-constructed dam can fail not from the water pressure but from the undermining of its foundations, so too can a cryptographic system falter due to the fallibility of human behavior.
To navigate this intricate landscape, it is crucial to embrace a mutable perspective on security. Rather than aspiring for an unattainable state of unbreakability, the focus should shift toward achieving a robust yet adaptable security posture. This perspective champions the integration of cutting-edge technology with practical risk management and best practices in user behavior. Building a resilient information security framework is analogous to fostering a diverse ecosystem; it thrives on variety and adaptability, rather than mere brute strength.
In conclusion, while the quest for unbreakable cryptography remains tantalizing, it is crucial to acknowledge the nuanced realities dictated by technological advancement, human behavior, and the ever-looming specter of quantum computing. Cryptography, much like the tapestry of life itself, is replete with intricate patterns, dynamic interactions, and perpetual evolution. Though true unbreakability may reside in the realm of fantasy, the pursuit of ever-greater security continues to challenge the intellect and creativity of cryptographers worldwide. Ultimately, the conversation extends beyond mere algorithms and protocols, delving deep into the very fabric of information society, as we endeavor to shield our secrets from adversaries in an ever-expanding digital wilderness.






Leave a Comment