Triple DES, or 3DES, is an encryption algorithm that applies the Data Encryption Standard (DES) cipher three times to each data block. While initially deemed a robust enhancement over its predecessor due to its increased key length, which mitigated some vulnerabilities inherent in DES, the question remains: is Triple DES still vulnerable to meet-in-the-middle attacks? To address this inquiry, it is essential to analyze the foundational principles of meet-in-the-middle attacks, the architecture of Triple DES, and the current cryptographic landscape.
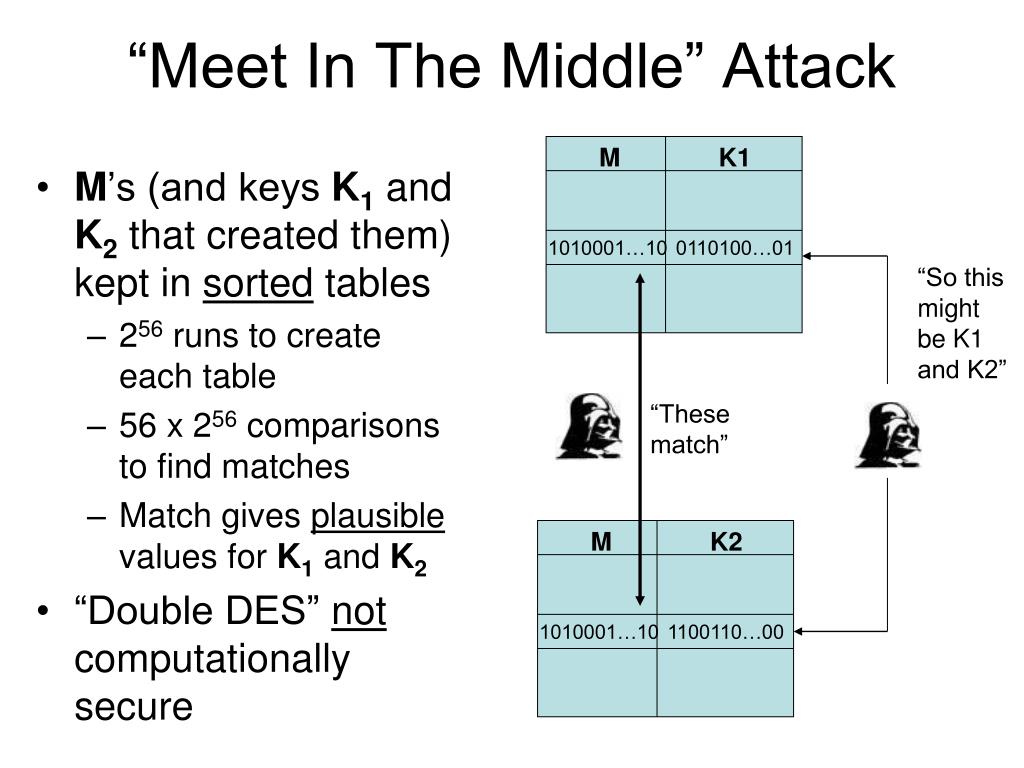
Meet-in-the-middle attacks exploit the nature of certain encryption algorithms where attackers can compromise security by simultaneously encrypting plaintext with one key and decrypting ciphertext with another key. Given the dual processes involved, attackers can potentially guess intermediate values that will align within the same operational matrix, thus narrowing down the possible combinations of keys. This attack method originated as a theoretical concept and gained prominence with the rise of block ciphers including DES.
Triple DES was conceived to extend the lifespan of DES by applying encryption in a more complex manner. It utilizes three different DES key applications: encrypt-decrypt-encrypt (EDE). This arrangement enables it to simulate a longer key size without necessitating an entirely new cryptographic standard. The essential feature here is that the effective key length of Triple DES escalates to 168 bits (in a three-key variant), a substantial increase compared to the 56 bits of the original DES. However, as security standards have evolved, the viability of such a configuration has come under scrutiny.
Critically, the increased key length does not inherently preempt a meet-in-the-middle attack. A direct examination reveals that an attacker could theoretically engage in a modified version of this attack. To employ a meet-in-the-middle attack against Triple DES, the approach would necessitate selecting pairs of plaintext and ciphertext, experimenting with potential first and second keys while simultaneously working backwards from the ciphertext. Although the complexities grow with the three applications, the fundamental vulnerability remains. In practical situations, the efficiency of such an attack can still be formidable, necessitating computational resources and time.
Recent advances in computational powers have further accentuated these vulnerabilities. The advent of highly sophisticated processing capabilities allows the execution of extensive brute-force attacks, diminishing the security guarantees provided by Triple DES. While the major cryptographic community and organizations have begun to phase out Triple DES in favor of more robust alternatives, such as AES, the continued existence of legacy systems employing Triple DES means this encryption form can still present a target. In the wake of these developments, it is crucial to delineate the implications for both current cryptographic practices and historical context.
The inherent design weakness of Triple DES can be viewed against the backdrop of cryptographic pragmatism. Despite its initial promise, the time complexity of a detailed meet-in-the-middle attack grows less feasible with increasing key lengths to some extent, it still poses a potential threat. Research has demonstrated that with sufficient determination and resources, the meet-in-the-middle approach can yield concrete results that implicate the efficacy of Triple DES as a choice for modern encryption protocols.
This contemplation leads to an inevitable query regarding the implications of utilizing outdated encryption mechanisms. As legacy systems persist in various sectors, particularly within the finance and healthcare industries, the fascination with these vulnerabilities intertwines with concerns around data security and the preservation of privacy. How such algorithms stand against modern threats establishes a compelling neologism within the cryptographic milieu: the struggle to reconcile security with practical functionality. The tendency towards entropy within these discussions prompts a broader consideration of how encrypted data is protected in real-world applications.
In conclusion, while Triple DES introduced certain advancements in securing data over its DES predecessor, the algorithm is still vulnerable to meet-in-the-middle attacks. The intricate dance of encryption and computational power has reshaped the landscapes of security. The innovations in computational technology necessitate a prudent reassessment of older algorithms. Transitioning towards more sophisticated alternatives, such as AES, represents not only an evolution of encryption standards but an essential response to the burgeoning complexities of information security, which must constantly adapt to emerging threats. As the digital realm continues to expand, vigilance in the pursuit of advanced cryptographic solutions becomes not just a scientific endeavor, but a crucial societal imperative.







Leave a Comment