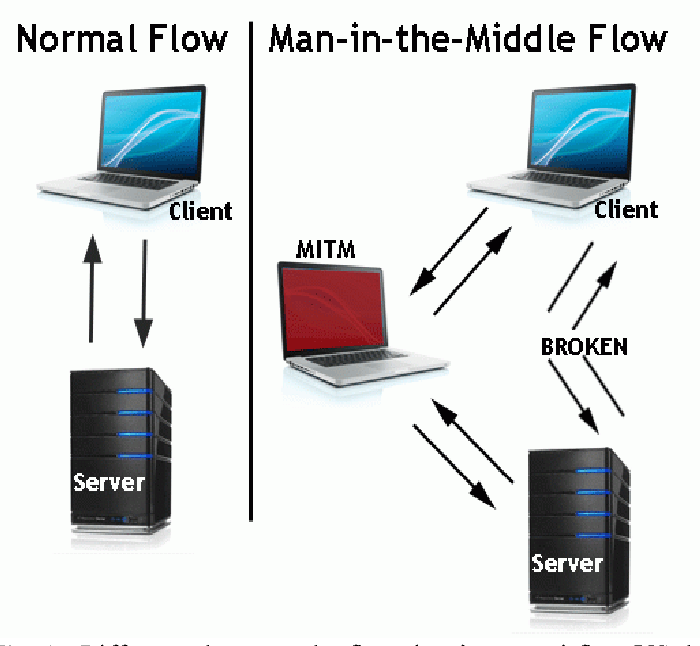
The realm of cybersecurity is rife with intricacies, and among the multitude of threats that lurk within the digital landscape, the man-in-the-middle (MITM) attack stands out as a particularly insidious variation. MITM attacks occur when an adversary covertly intercepts and possibly alters communications between two parties, unbeknownst to them. These attacks can manifest in various forms, each with its own modus operandi and ramifications.
In the context of exemplifying real-world MITM attacks, it is essential to delineate the types of attacks, the mechanisms employed, and instances in which they have played out. By doing so, we can glean a deeper understanding of the vulnerabilities that pervade our digital interactions.
Initially, one must explore the fundamental types of MITM attacks. One of the most prevalent forms is the “Wi-Fi Eavesdropping” attack. Here, the perpetrator endeavors to create a hostile Wi-Fi access point—often masquerading as a legitimate one—to lure unsuspecting individuals. Once connected, the cybercriminal can capture sensitive data transmitted over the network. This type of attack is not merely theoretical; instances abound where unsuspecting café patrons unknowingly expose their login credentials and financial information to malicious actors.
A more sophisticated form of MITM attack materializes in what is known as “SSL Stripping.” This strategy exploits the security afforded by HTTPS, the secure version of HTTP. The assailant intercepts the connection and downgrades it to an unencrypted HTTP session. Unsuspecting users may believe they are communicating securely, yet they are unwittingly divulging sensitive data in plain text. This attack gained notoriety in various high-profile breaches, where users of banking websites were targeted, leading to significant financial losses.
Another type worth discussing is the “Session Hijacking” attack, which involves taking over a user session after a user has logged into a web application. Once the malicious actor has acquired the session token, they can impersonate the legitimate user, often accessing sensitive information or executing unauthorized actions. This form of attack has typically been executed against webmail platforms and social media accounts, leading to potential identity theft. Cases abound wherein hackers have hijacked social media accounts, wreaking havoc on the target’s online presence.
It is imperative to consider the various industries affected by these attacks. Financial institutions represent a prime target for MITM attacks. With the proliferation of online banking, attackers have devised strategies to exploit vulnerabilities. Reports have indicated instances in which cybercriminals successfully executed MITM attacks on online banking platforms, siphoning off funds through phishing and credential theft. The ramifications are dire, not just for the individual account holders but also for the institutions involved, prompting substantial financial repercussions and reputational harm.
Further illustrating the real-world implications of MITM attacks are cases involving corporate espionage. Numerous businesses have faced breaches wherein competitors or malicious adversaries have intercepted communication channels, gaining access to proprietary information and trade secrets. These incidents exemplify the broader ramifications of MITM attacks on business integrity and economic stability. The stakes are particularly high in industries like technology and health care, where the theft of data can have cascading effects on confidentiality and compliance.
The societal impact of MITM attacks extends beyond immediate financial loss. The psychological toll on victims—who grapple with the violation of privacy and potential future insecurity—cannot be overstated. Victims often endure the aftermath of such attacks, embodying a lingering fear of future breaches and a misguided trust in seemingly secure platforms.
Fortunately, a multifaceted approach can significantly mitigate the risk of MITM attacks. Users should practice vigilance by ensuring their connections are encrypted, using reputable virtual private networks (VPNs), and refraining from connecting to unsecured public Wi-Fi without adequate protection. Additionally, security measures, such as multifactor authentication, can greatly reduce the effectiveness of session hijacking attempts, as they require more than just a password.
Moreover, organizations must place a high premium on cybersecurity protocols. Implementing comprehensive security training programs for employees can foster awareness and bolster resistance against social engineering tactics that often accompany MITM attacks. Regularly updating security software and enforcing strict password policies are also critical steps organizations can take. Furthermore, employing intrusion detection systems can facilitate the timely identification of anomalous activities, enabling prompt countermeasures.
In summation, MITM attacks serve as a salient reminder of the vulnerabilities present within our interconnected world. As technology evolves, so too must our understanding and responses to such threats. With an arsenal of preventative measures and constant vigilance, individuals and organizations can bolster their defenses against the ever-present specter of man-in-the-middle attacks. The proactive adaptation to the shifting sands of cybersecurity will ultimately delineate the survivors from the casualties of the digital age.







Leave a Comment