The digital landscape has evolved dramatically, with threats emerging from various angles. One profound threat is the concept of spoofing, frequently linked to the notorious Man-in-the-Middle (MitM) attacks. Understanding the nuances of these two concepts is paramount, especially in an age where internet communications are vital for both personal and corporate interactions. This article provides a deep dive into the relationship between spoofing and MitM attacks, elucidating the mechanics, implications, and preventive measures.
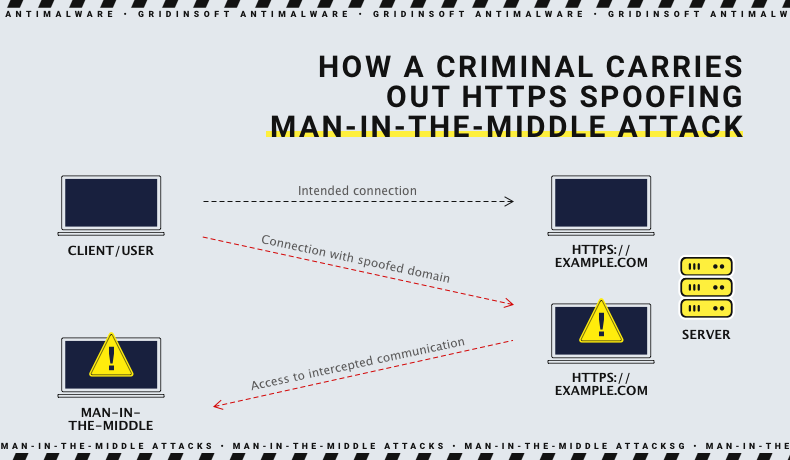
To appreciate the intricacies of spoofing and MitM attacks, one must first delineate the definitions. Spoofing generally refers to impersonation tactics in cyberspace, where an attacker masquerades as a legitimate entity. Conversely, a Man-in-the-Middle attack involves an intruder secretly intercepting and possibly altering the communications between two parties without their knowledge. At a glance, it seems that spoofing can indeed be a component of a MitM attack. However, the complexities merit further examination.
First, let’s explore the manifold types of spoofing that can facilitate MitM attacks. One prevalent variant is IP spoofing, where the attacker sends IP packets from a false (or spoofed) source address to deceive the recipient. This tactic is commonly employed to trick network devices into thinking the spoofed packets derive from a trusted source, thus opening the door for further exploits, including MitM attacks. Similarly, ARP (Address Resolution Protocol) spoofing is another technique allowing attackers to map the network address of a target to the attacker’s MAC address. Consequently, the attacker reroutes the traffic intended for the legitimate device, effectively positioning themselves as the intermediary.
The omnipresence of social engineering in the digital realm cannot be overlooked. Spoofing can extend into email and text messaging, known as phishing attacks. An attacker might create a seemingly authentic email masquerading as a reputable organization, prompting the recipient to divulge sensitive information. Should an unsuspecting victim forward such data without verification, an unholy trifecta of phishing and spoofing culminates into a MitM attack, where the attacker can hijack further communications.
MitM attacks showcase various methodologies, each of which is potent in its distinctive manner. The simplest form is the eavesdropping attack, where an attacker passively monitors network traffic, capturing data such as login credentials or personal details. More invasive is the active interception method, where malicious actors manipulate the data flow between two communicating entities. This manipulation can include injecting malware or redirecting users to compromised websites, producing dire implications for both personal privacy and organizational security.
Analysis reveals that while spoofing often serves as an enabler for MitM attacks, it is far from the singular pathway. Therein lies the importance of recognizing the multifaceted nature of security vulnerabilities. Tools such as packet sniffers can help attackers garner sensitive data without actively engaging in direct communication disruption. This nuance leads to a critical discussion on the implications of these attacks for both individuals and organizations.
For individuals, the repercussions of falling victim to a MitM attack can be devastating. Identity theft represents a significant threat, where personal information harvested can lead to unauthorized bank transactions or financial losses. Moreover, the psychological toll of having one’s privacy breached is incalculable. For organizations, the stakes escalate significantly. Data breaches, resulting from MitM attacks, can irreparably tarnish reputations, resulting in consumer trust erosion and potentially crippling financial penalties.
To counteract the rising tide of spoofing and MitM attacks, a fortified approach towards cybersecurity is essential. Encryption serves as a strong defensive mechanism, particularly Transport Layer Security (TLS), which secures communications to deter interception. Additionally, employing Virtual Private Networks (VPNs) can obscure users’ IP addresses, enhancing anonymity and complicating an attacker’s ability to execute MitM attacks.
Moreover, user awareness is pivotal. Organizations should invest in training programs equipping employees with knowledge to identify phishing attempts. Recognizing the hallmarks of spoofed communications can dramatically decrease the likelihood of succumbing to an attack. Multi-factor authentication further reinforces security measures, as it requires users to provide two or more verification factors, thus creating a robust barrier against unauthorized access.
The dialogue surrounding spoofing and Man-in-the-Middle attacks is expansive, touching on technical aspects, implications for security, and preventative measures. As digital communication continues to flourish, the necessity for vigilance cannot be overstated. Understanding the relationship between spoofing and MitM attacks empowers both individuals and organizations to navigate the digital world more safely. In a constantly evolving threat landscape, knowledge serves as a potent weapon against malicious actors intent on exploiting vulnerabilities.
In summation, while spoofing can indeed be a manifestation of a Man-in-the-Middle attack, it is essential to comprehend it as part of a broader spectrum of cybersecurity threats. Through heightened awareness and proactive defenses, individuals and organizations can mitigate risks associated with these nefarious tactics, fostering a more secure digital environment.







Leave a Comment