In the realm of digital security, the discussion surrounding password-based AES (Advanced Encryption Standard) encryption continues to gain traction. As data breaches and cyber threats proliferate, it is imperative to scrutinize the efficacy of encryption methods, especially those reliant on user-generated passwords. This article delves into the nuances and complexities of password-based AES encryption, examining its mechanisms, effectiveness, vulnerabilities, and alternative strategies.
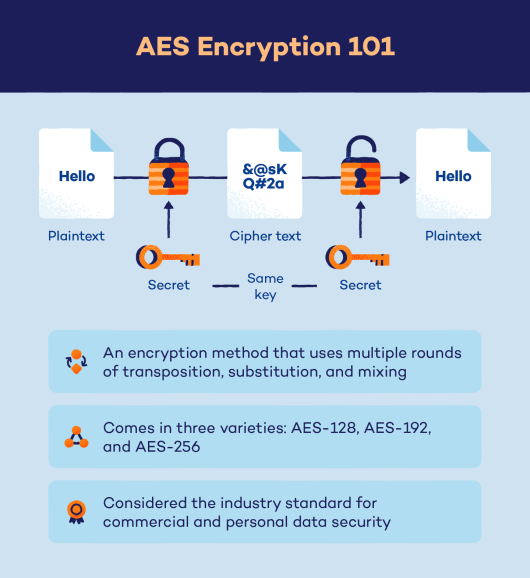
AES encryption is a symmetric key algorithm adopted globally for securing sensitive information. Its robust structure allows it to encrypt data in blocks of 128 bits using key sizes of 128, 192, or 256 bits. While the strength of AES is well-documented, the security of a system employing AES encryption hinges significantly on the quality of the passwords used.
Understanding the interplay between passwords and encryption is fundamental. In password-based systems, the user provides a password which is transformed into an encryption key through a process known as key derivation. Herein lies the first challenge: the efficacy of AES encryption is intrinsically linked to the complexity of the password. Weak passwords can easily be compromised through various means such as brute force attacks or dictionary attacks.
Brute force attacks exploit computational power to systematically check every possible password until the correct one is found. Given that modern computers can execute billions of calculations per second, a simple, common password (e.g., “123456”) can be cracked rapidly. Furthermore, tools that automate this process have become increasingly accessible, making it imperative for individuals and organizations to adopt stronger password policies.
Dictionary attacks take a different approach. These attacks utilize pre-existing lists of common passwords and variations thereof. The efficiency of dictionary attacks underscores the need for users to eschew easily guessable passwords and opt for longer, more complex selections comprising a mix of letters, numbers, and symbols. With the average user typically gravitating towards convenience, the propensity for using weak passwords poses a significant threat to the integrity of AES encryption.
Moreover, the process of key derivation itself can introduce vulnerabilities. To generate encryption keys from passwords, cryptographic functions such as PBKDF2, bcrypt, or Argon2 are often employed. These functions apply a hashing algorithm multiple times to increase the time required to crack the hash, thus augmenting security. However, if the password chosen is weak or if the iterations used are insufficient, the entire encryption scheme becomes perilous.
Another critical factor influencing the security of password-based AES encryption is the management of the encryption keys. Key management varies significantly across contexts, and an insecure method can nullify the benefits of robust encryption. For example, if a password is stored alongside the encrypted data without any form of secure storage mechanism, an attacker gaining access to that data can easily obtain the password and, by extension, the encryption key itself.
Adverse scenarios are compounded in environments where users engage in password reuse—adopting the same password across multiple platforms. A data breach on one service can expose passwords for others, presenting a cascading effect that compromises multiple layers of security. The implications for AES encryption—operating on such reused credentials—can be dire, resulting in unauthorized access to encrypted data across various systems.
As vulnerabilities become apparent, the quest for alternative methods to enhance AES encryption security persists. Multi-factor authentication (MFA) combines something the user knows (the password) with something the user has (a hardware token or smartphone) or something inherent (biometric data), thereby safeguarding against password theft. By requiring multiple forms of identification, MFA significantly mitigates the risks associated with password-based systems.
Beyond MFA, transitioning towards passwordless authentication methods offers a potentially more secure trajectory. Such methods leverage cryptographic keys, hardware tokens, or biometrics directly, eliminating the dependence on potentially weak passwords. This paradigm shift holds promise in circumventing the myriad pitfalls associated with traditional password-based encryption.
When assessing the true security of password-based AES encryption, a nuanced approach is essential. On one hand, AES itself remains a bastion of cryptographic strength. On the other hand, the security of implementations relying on user-generated passwords remains precarious, laden with vulnerabilities exacerbated by human behavior. The synthesis of strong passwords, adherence to efficient key management practices, and the integration of supplementary authentication measures are crucial for bolstering encryption security.
In conclusion, while AES offers formidable encryption capabilities, the overarching framework of password-based security requires vigilant scrutiny and continuous evolution. For users and organizations alike, the mandate is clear: prioritize security by enforcing stringent password policies, adopting innovative authentication methods, and embracing a culture of cybersecurity awareness. The integrity of encrypted data and the safeguarding of sensitive information depend on these critical steps.







Leave a Comment