As the digital era burgeons with an ever-increasing demand for information security, the inquiry into the relevance of past cryptographic techniques, particularly those employed during World War II, stands as a pivotal examination. The Enigma machine, emblematic of wartime cryptology, acts as a historical benchmark against which modern encryption techniques can be contrasted. This exploration reveals not only the evolution of cryptography but also illustrates the metaphorical lifecycle of knowledge—where past wisdom informs present practices and anticipates future developments.
The Enigma machine, with its intricate system of rotors and settings, was originally engineered to secure military communications. Its complexity was both a boon and a bane; while it offered a high degree of security, it also became a focal point for Allied cryptanalysts. The laborious efforts of codebreakers like Alan Turing and his team at Bletchley Park elucidated the vulnerabilities inherent in the machine’s design. This historical context embodies a crucial tenet of cryptography: even the most sophisticated systems can harbor weaknesses ripe for exploitation.
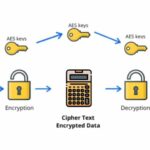
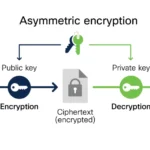
Fast forward to the contemporary landscape of cryptography, which has transformed dramatically with the advent of digital technology. Today’s methods, including symmetric and asymmetric encryption, employ algorithms such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) to protect sensitive information. These modern systems are akin to advanced fortifications, built upon the insights gleaned from past experiences. Just as castles were designed with towers and archer slots, contemporary encryption relies on mathematical constructs that create robust defenses against sophisticated attacks.
Moreover, the Enigma’s reliance on mechanical components starkly contrasts with today’s reliance on digital processes. The mechanical rotors and plugboards, though daunting in their operational complexity, lack the scalability and speed of modern algorithms. An Enigma machine could be laboriously operated by a skilled encoder, while its present-day counterparts can execute millions of calculations per second. This exponential increase in computational power renders traditional methods, like those employed in WWII, more of a historical curiosity than a practical tool for contemporary security challenges.
However, the Enigma machine retains its relevance as an educational artifact. Understanding how it functioned provides valuable lessons in the principles of cryptography. The very act of devising a cipher, as exemplified by the Enigma, fosters an appreciation for the essential elements of secrecy—obfuscation, complexity, and the notion of a key. These principles are mirrored in modern encryption, albeit through advanced mathematical constructs rather than gears and wires. Thus, the Enigma reinforces the foundational concepts that continue to underpin contemporary methods.
Another layer of intrigue arises when considering the psychological aspects of cryptography. The Enigma not only represented a technological challenge but also became a symbol of the war’s intelligence warfare. Cryptographic engagements dominated the battlefield as much as physical confrontations, highlighting the strategic importance of information control. In this light, modern cryptography similarly serves as an arsenal in corporate and state conflict, with nation-states targeting each other’s data infrastructures. The metaphor of war emerges again; just as the Enigma served as a tool for national defense, contemporary cryptographic techniques stand as digital sentinels, guarding private and confidential information against a backdrop of cyber hostilities.
Intriguingly, the Enigma embodies an allegorical contrast to modern encryption techniques like quantum cryptography. While the former operated under deterministic principles, the advent of quantum mechanics introduces elements of chance and uncertainty into the realm of cryptography. Quantum key distribution allows for the transmission of secrets in ways that defy classical physics, offering unparalleled security. The shift from the deterministic Enigma to the probabilistic nature of quantum encryption illustrates the relentless pursuit of security within an ever-shifting landscape of technological advancement.
Despite the fervent evolution of cryptographic practices, the Enigma machine endures as a symbol of resilience and ingenuity. Each mechanical component, each cryptographic keyring, can be likened to chapters in a grand narrative of security. The ingenuity of WWII cryptographers shaped the foundational structures that still influence modern encryption techniques. While the Enigma itself may no longer hold practical utility in an age dominated by digital technology, its legacy persists, providing an essential touchstone for understanding the evolution of secrecy in human communication.
Ultimately, the inquiry into the relevance of the Enigma machine serves as a microcosm of the broader trajectory of cryptography. The movement from mechanical to digital forms signifies not just an advancement of technology, but a deeper understanding of the mathematics and principles of secrecy. Enigma whispers tales of heroism, ingenuity, and caution—reminding us that in the realm of cryptography, history is not merely a record of past endeavors but a beacon illuminating the continuous evolution of thought and technology. As we stand at the confluence of history and innovation, the lessons from the Enigma compel a notion that remains invariant: the quest for security is as much an art as it is a science. And in this intertwined journey, the past will always offer insights that may very well dictate future paths.





Leave a Comment