The realm of cybersecurity is fraught with a myriad of threats, each with its own complexities and nuances. Among these, eavesdropping and man-in-the-middle (MitM) attacks stand out as particularly insidious forms of cyber intrusion. Though they share some superficial similarities, a comprehensive analysis reveals they are distinct in essence, methodology, and implications.
At its core, eavesdropping refers to the unauthorized interception of communications, where an adversary listens in on conversations, typically without the knowledge of the participating parties. This can occur in various contexts—from telephone calls to electronic communications. The goal of eavesdropping is often to harvest sensitive information or intelligence, making it a pervasive threat in both personal and corporate settings.
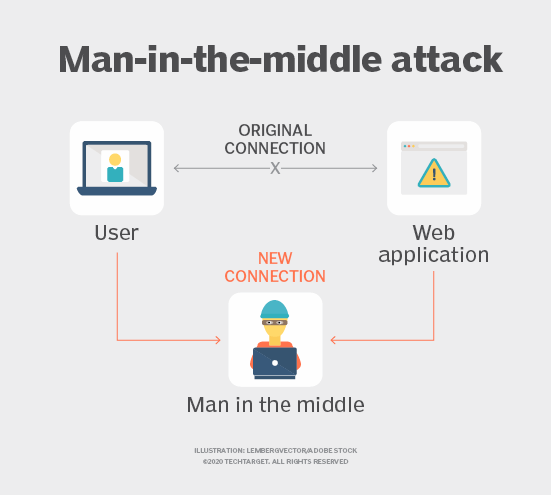
In contrast, a man-in-the-middle attack involves a more active and sophisticated engagement between two parties. In this scenario, the attacker positions themselves within the communication stream, effectively relaying messages between the two, often altering or extracting information without either party’s awareness. While the concept of eavesdropping might evoke images of covert surveillance, a MitM attack is akin to a puppeteer, orchestrating the flow of information and manipulating it to suit their ends.
To distill the differences further, consider the methods employed by both threats. Eavesdropping may utilize passive techniques, such as intercepting radio signals or exploiting vulnerabilities in Wi-Fi networks. For instance, an individual with the right tools could capture unencrypted packets of data floating through the air—merely listening and recording. On the other hand, a MitM attack often necessitates a more elaborate setup, such as deploying rogue routers or using phishing schemes to coax users into connecting to malicious networks. The adversary in this scenario does not merely listen; they engage with and influence the conversation, making it a more dynamic and perilous threat.
Understanding the motivations behind these attacks reveals further insights. Eavesdropping is often driven by a desire for information gathering. For example, companies may engage in corporate espionage, listening in to rival communications to gain competitive advantage. Alternatively, individuals may eavesdrop out of curiosity, malice, or under the guise of protecting themselves or others. Conversely, the motivations for executing a MitM attack can be more diverse, ranging from financial gain through identity theft to political agendas where manipulation of information plays a pivotal role in swaying public opinion or sowing discord.
Moreover, the implications for victims diverge significantly between the two. Eavesdropping primarily leads to privacy invasions, where sensitive conversations are exposed, potentially resulting in reputational damage or the leaking of confidential information. For instance, a business leader’s private negotiations might be overheard, giving competitors an unfair advantage. Conversely, the ramifications of a MitM attack can be substantially more severe. Consider the potential for data alteration, where an attacker not only listens but also modifies the information being communicated. An example might involve altering a bank transaction’s details, redirecting funds to the attacker’s account. Thus, the scope of damage is magnified in MitM scenarios, presenting a far more complex web of risks.
Despite these distinctions, it is not uncommon for individuals to conflate eavesdropping with MitM attacks, perhaps due to their overlapping nature in the digital landscape. Bots that scrape websites for information may engage in eavesdropping, while malicious actors leveraging that stolen data may embark on a MitM endeavor. This interconnectedness can underscore a larger phenomenon: the chronic state of vulnerability inherent in modern communication systems. As technology evolves, so too do the tactics employed by cybercriminals, necessitating an ongoing vigilance and understanding among users.
The burgeoning tale of eavesdropping and MitM attacks speaks to an innate fascination with the pervasive nature of surveillance in the digital age. It evokes a sense of intrusion—a breach of trust in the sanctum of private communication. The very act of eavesdropping is cloaked in ethical ambiguity, often invoking debates about privacy rights and the extent to which society is willing to relinquish its liberties for security. Meanwhile, MitM attacks highlight the fragile architecture of our digital communications, wherein the safety of our interactions rests precariously on trust in technology.
Ultimately, effective mitigation strategies must account for the distinguishing characteristics of both eavesdropping and MitM attacks. Encryption, for instance, serves as a formidable shield against both threats; however, its efficacy hinges on proper implementation. Regularly updated security protocols can thwart potential MitM attacks, while strong encryption methods can protect against eavesdropping attempts. Individual awareness and rigorous cybersecurity training are imperative, enabling users to identify suspicious conduct—be it an unauthorized access point in a Wi-Fi network or anomalous alterations to received messages.
In conclusion, while eavesdropping and man-in-the-middle attacks share a common thread of unauthorized access to information, they diverge significantly in their mechanisms, intent, and implications. Recognizing these distinctions is essential for developing robust defenses against the evolving landscape of cybersecurity threats. As society becomes increasingly intertwined with digital communication, understanding the intricacies of these threats will remain vital in fostering secure interactions in a volatile cyber environment.







Leave a Comment