The Caesar cipher, named after Julius Caesar who is said to have employed this method for securing military communications, stands as one of the most emblematic examples of classical encryption. This straightforward substitution cipher provides a fascinating lens through which to scrutinize the broader principles of symmetric and asymmetric cryptography. In exploring whether the Caesar cipher falls into the category of symmetric or asymmetric encryption, we embark on a journey through the realms of cryptographic theory and historical application.
To delineate our discussion, we first must grasp the definitions of symmetric and asymmetric encryption. Symmetric encryption operates on the principle that the same key is utilized for both encryption and decryption. In contrast, asymmetric encryption harnesses a pair of keys, typically referred to as the public and private keys. This dichotomy serves as the foundation for our inquiry into the nature of the Caesar cipher.
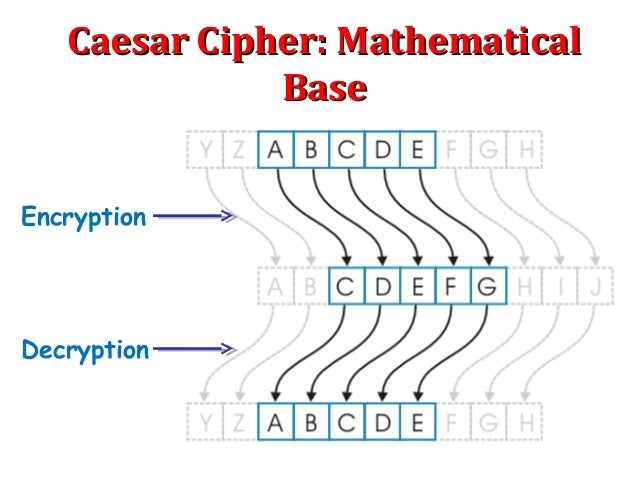
When we delve into the mechanics of the Caesar cipher, we unearth a method that is quintessentially symmetric. The fundamental operation involves shifting the letters of the plaintext by a fixed number of positions down the alphabet. For instance, if we choose a shift of three, the letter A becomes D, B transforms into E, and so forth. This relatively elementary transformation exemplifies how the same key—the number of positions in the shift—facilitates both the encryption of the plaintext into ciphertext and the subsequent decryption of the ciphertext back into plaintext.
To illustrate, one might envision the alphabet as a complex organism, one where each letter interacts symbiotically with its neighbors. When one shifts these letters, as in the Caesar cipher, it is akin to orchestrating a dance: each letter moves in tandem with a preset rhythm defined by the key. In this sense, the Caesar cipher symbolizes a cohesive system where the same mechanism is employed to cloister and then unveil information.
The elegance of the Caesar cipher lies in its simplicity, but this simplicity also belies its vulnerabilities. As a symmetric cipher, it suffers from the common pitfalls that plague this category. The determination of the key is paramount. If an adversary can ascertain the shift value, they can effortlessly decrypt the ciphertext. In reality, this facet manifests in the form of vulnerabilities such as frequency analysis, where the prevalence of certain letters can lead to the revelation of the key.
Despite its susceptibility, the Caesar cipher carries a unique allure. Its historical roots tether it to a period of strategic military maneuvering, and its unpretentious design contrasts sharply with the complex algorithms of contemporary asymmetric encryption methods. This juxtaposition invites a contemplation of both the progression of cryptographic techniques and the enduring nature of the fundamentals that bind them.
As we expand our perspective to the broader landscape of cryptography, symmetrical methods—like the Caesar cipher—are primarily beneficial for environments where the secure transmission of the key is feasible. In scenarios involving closed systems, where the channel through which messages flow is controlled, symmetric encryption provides efficiency and speed. These attributes fortify its appeal amongst cryptographic enthusiasts and historians alike.
Conversely, asymmetric encryption has carved out its niche within the contemporary digital paradigm. The advantages of utilizing two distinct keys are particularly salient in the realms of secure communications over untrusted networks. By incorporating a public key, anyone may encrypt a message while only the designated recipient, possessing the private key, can decrypt it. This paradigm effectively protects against eavesdroppers, ensuring that entities can communicate confidentially even in the absence of a pre-established secure key exchange.
Yet, it is essential to underscore that while the Caesar cipher may bask in its status as a symmetric encryption scheme, it remains fundamentally isolated from the complexities of modern cryptographic systems. With advancements in technology, the sheer computational power available to modern adversaries renders the Caesar cipher almost trivial to crack. Thus, it invites not merely admiration for its historical significance but also a critical perspective on the evolution of encryption methodologies.
Entwined in this dialogue of symmetry versus asymmetry is the inherent tension between simplicity and security. The Caesar cipher, in its archetypal form, encourages reflection on the delicate balance that exists in cryptographic practice. Every encryption technique, be it symmetric or asymmetric, carries with it an exchange—a trade-off between ease of use and level of security. The study of the Caesar cipher provides a cohesive entry point into understanding these broader dynamics and allows us to appreciate the artistry of encryption in a historical context.
In closing, the exploration of the Caesar cipher as a symmetric encryption method reveals not just its foundational attributes but serves as an enchanting window into the evolution of cryptographic practices. It embodies a narrative where simplicity reigns, yet challenges us to recognize the vulnerabilities that accompany it. Though antiquated in its application today, the Caesar cipher continues to provoke thought, illustrating the perennial dance between communication, encoding, and the perpetual quest for security against the backdrop of an ever-evolving digital landscape.







Leave a Comment